tetragon是cilium的子项目,基于ebpf监控容器的进程行为、文件访问、网络访问,以及特权的使用,本周按照官方指导进行了简单实践,安装tetragon,helm r 2022-8-7 09:9:46 Author: 云计算和网络安全技术实践(查看原文) 阅读量:35 收藏
tetragon是cilium的子项目,基于ebpf监控容器的进程行为、文件访问、网络访问,以及特权的使用,本周按照官方指导进行了简单实践,
安装tetragon,
helm repo add cilium https://helm.cilium.io,
helm repo update,
helm install tetragon cilium/tetragon -n kube-system,
安装Tetragon CLI工具,
GOOS=$(go env GOOS),
GOARCH=$(go env GOARCH),
curl -L --remote-name-all https://github.com/cilium/tetragon/releases/download/tetragon-cli/tetragon-${GOOS}-${GOARCH}.tar.gz{,.sha256sum},
sha256sum --check tetragon-${GOOS}-${GOARCH}.tar.gz.sha256sum,
sudo tar -C /usr/local/bin -xzvf tetragon-${GOOS}-${GOARCH}.tar.gz,
rm tetragon-${GOOS}-${GOARCH}.tar.gz{,.sha256sum},
验证进程执行监控,安装测试容器,
wget https://raw.githubusercontent.com/cilium/cilium/v1.11/examples/minikube/http-sw-app.yaml,
kubectl apply -f http-sw-app.yaml,
进入容器执行命令,
kubectl exec -it xwing -- /bin/bash,
whoami,
查看监控效果,
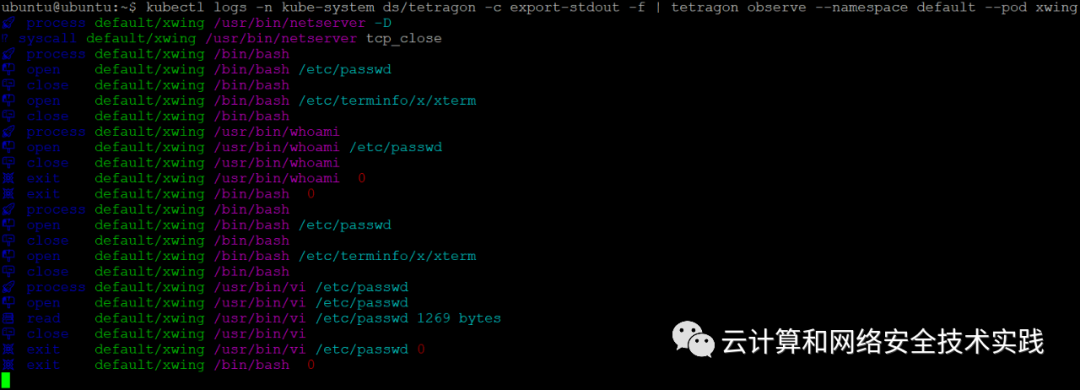
kubectl logs -n kube-system ds/tetragon -c export-stdout -f | tetragon observe --namespace default --pod xwing,
验证文件访问监控,安装文件访问监控策略,
wget https://raw.githubusercontent.com/cilium/tetragon/main/crds/examples/sys_write_follow_fd_prefix.yaml,
kubectl apply -f sys_write_follow_fd_prefix.yaml,
进入容器执行命令,
kubectl exec -it xwing -- /bin/bash,
vi /etc/passwd,
查看监控效果,
kubectl logs -n kube-system ds/tetragon -c export-stdout -f | tetragon observe --namespace default --pod xwing,
验证网络访问监控,安装网络访问监控策略,
wget https://raw.githubusercontent.com/cilium/tetragon/main/crds/examples/tcp-connect.yaml,
kubectl apply -f tcp-connect.yaml,
执行网络访问命令,kubectl exec -it xwing -- curl http://cilium.io,
查看监控效果,
kubectl logs -n kube-system ds/tetragon -c export-stdout -f | tetragon observe --namespace default --pod xwing,
验证特权使用监控,安装测试容器,
wget https://raw.githubusercontent.com/cilium/tetragon/main/testdata/specs/testpod.yaml,
kubectl apply -f testpod.yaml,
查看监控效果,
kubectl logs -n kube-system ds/tetragon -c export-stdout -f | tetragon observe --namespace default --pod test-pod,
如有侵权请联系:admin#unsafe.sh