
2022-8-3 20:44:35 Author: infosecwriteups.com(查看原文) 阅读量:24 收藏
Hello Security Researchers
Have you ever encountered a bug where it’s hard to show impact due to the lack of enumeration of a certain value of a parameter ?
Well if yes, In this writeup I will talk about how you can find and abuse URL shortners to ATO or Information disclosure
Many companies use URL shortners to send private invite and passwordless logins and things along those lines and it’s really difficult to guess or to brute these but there’s always a way to do things by thinking outside the box 📦
Let’s talk about URL shortners and their types:
URL shortners are mostly linked to 3rd party services like https://bitly.com https://cutt.ly/ and others are made by company and they have custom built
Like : https://indd.jobs | https://inst.cr
How can we approach this:
We can use multiple scenarios first we can test functionalities that triggers email and view the source of them if they contain a URL shortner check twitter account of company and extract all the links they share
How URL Shortners Work:
Most of the case we should look for something that has this kind of behavior
URLshortner.com/{HASH} ===> Website.com/?token={YOU-CANT-GUESS-THIS}
and based on that we can enumerate more and see more
Complexity Level:
The complexity is based on the HASH used after the URL so it’s either integer strings and or both Uppercase / Lowercase length of the hash that starts from 5 characters plus
Examples:
https://url.com/12345 | https://url.com/A2B4C | https://url.com/A2B4CGFDFF33434
So if we are facing only integers it’s the easiest case here we can of course generate all the possible and it’s kinda difficult for other case OR IS IT ? 😈
Exploitation:
For our write up we will focus on inst.cr since it has a custom built and it’s so difficult to guess http://inst.cr/t/UEJBUThINjYx
So how can we guess the hash?
We don’t, we don’t need to we can basically throw the domain into waybackurls or gau and see the results

Now we need to see where the links are redirecting and see if something useful is the paths that we can make a use of
we simply do this
gau inst.cr | httpx -location -mc 301,302 | grep -Eo ‘\[(.*?)\]’
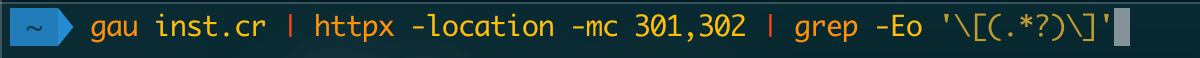
In order to grep the value of all the rediction and spit it out in your terminal

Now based on the application logic, you can search for keywords that are interesting like token id uuid and things along those lines
after that you will have a very good argument to convince the team that you were able to get the value of a certain parameter that they made difficult to guess
Results?
Blind ATO twice in a private program due to valide token on URLshortner
site.com/?basket=token

Multiple IDORS went from Invalid to valid

I hope you enjoyed reading this and I will catch you in the next one
You can find at:
Discord: Ayoub#1969
Twitter: https://twitter.com/OriginalSicksec
Stay curious ❤
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE!
如有侵权请联系:admin#unsafe.sh