2022-8-1 23:0:43 Author: xz.aliyun.com(查看原文) 阅读量:156 收藏
https://archives2.manageengine.com/passwordmanagerpro/12100/ManageEngine_PMP_64bit.exe
补丁
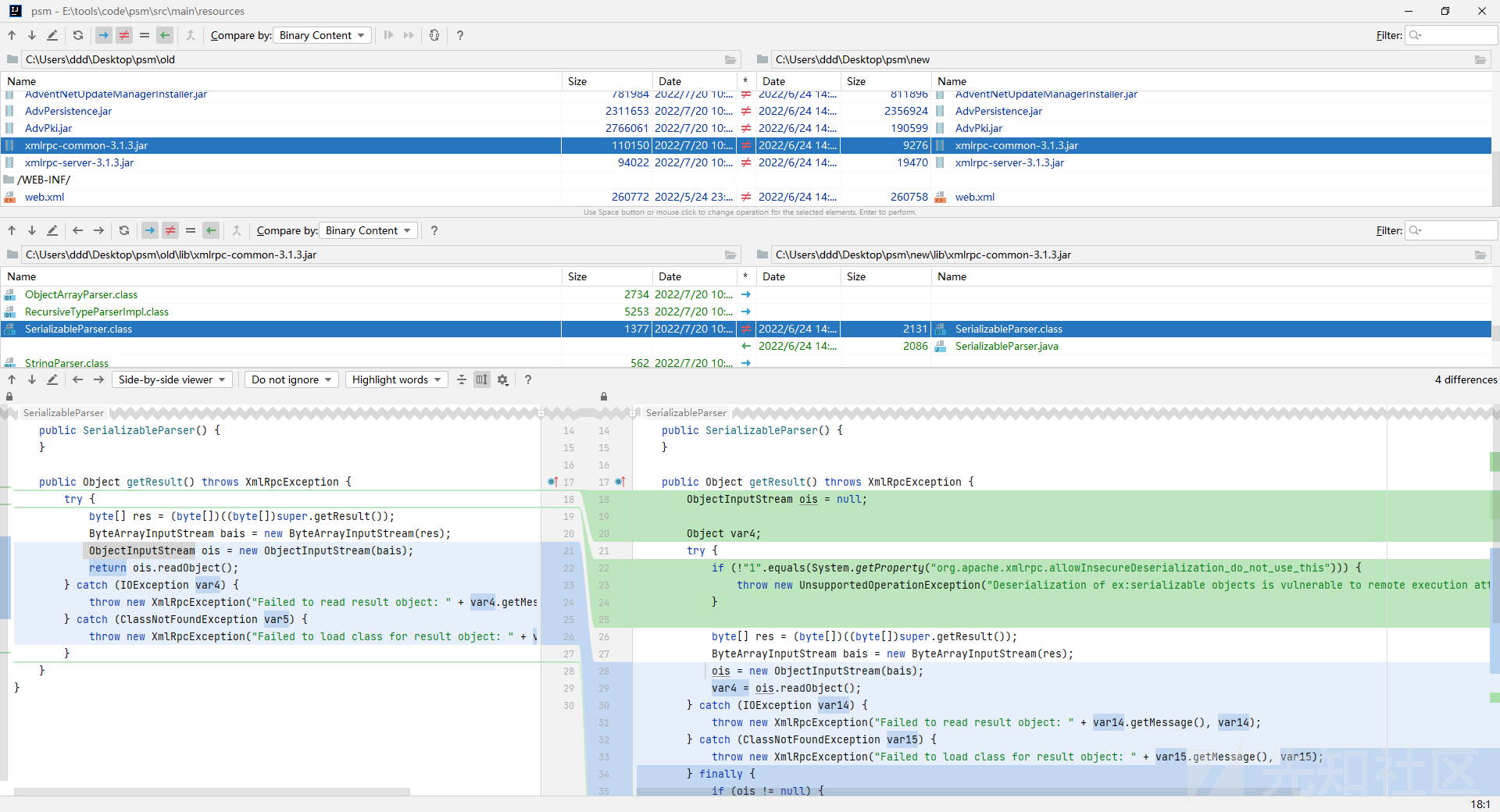
org.apache.xmlrpc.parser.SerializableParser#getResult 关了反序列化

通过漏洞描述可知为XML-RPC的反序列化RCE

回顾 CVE-2020-9496 Apache Ofbiz XMLRPC RCE漏洞 漏洞由XmlRpcRequestParser解析xml时触发,由此我们用tabby来查询谁调用了XmlRpcRequestParser

从路径的源头查询
org.apache.xmlrpc.webserver.PmpApiServlet#doPost

调用super的post函数 org.apache.xmlrpc.webserver.XmlRpcServlet#doPost

继续跟进 org.apache.xmlrpc.webserver.XmlRpcServletServer#execute

继续调用 org.apache.xmlrpc.server.XmlRpcStreamServer#execute

其中getRequest函数会从原始request构建XmlRpcRequest org.apache.xmlrpc.server.XmlRpcStreamServer#getRequest

在这里就开始解析xml,触发rpc了。poc和CVE-2020-9496一样
贴一下堆栈。
getResult:36, SerializableParser (org.apache.xmlrpc.parser)
endValueTag:78, RecursiveTypeParserImpl (org.apache.xmlrpc.parser)
endElement:185, MapParser (org.apache.xmlrpc.parser)
endElement:103, RecursiveTypeParserImpl (org.apache.xmlrpc.parser)
endElement:165, XmlRpcRequestParser (org.apache.xmlrpc.parser)
endElement:-1, AbstractSAXParser (org.apache.xerces.parsers)
scanEndElement:-1, XMLNSDocumentScannerImpl (org.apache.xerces.impl)
dispatch:-1, XMLDocumentFragmentScannerImpl$FragmentContentDispatcher (org.apache.xerces.impl)
scanDocument:-1, XMLDocumentFragmentScannerImpl (org.apache.xerces.impl)
parse:-1, XML11Configuration (org.apache.xerces.parsers)
parse:-1, XML11Configuration (org.apache.xerces.parsers)
parse:-1, XMLParser (org.apache.xerces.parsers)
parse:-1, AbstractSAXParser (org.apache.xerces.parsers)
parse:-1, SAXParserImpl$JAXPSAXParser (org.apache.xerces.jaxp)
getRequest:76, XmlRpcStreamServer (org.apache.xmlrpc.server)
execute:212, XmlRpcStreamServer (org.apache.xmlrpc.server)
execute:112, XmlRpcServletServer (org.apache.xmlrpc.webserver)
doPost:196, XmlRpcServlet (org.apache.xmlrpc.webserver)
doPost:117, PmpApiServlet (org.apache.xmlrpc.webserver)
service:681, HttpServlet (javax.servlet.http)
service:764, HttpServlet (javax.servlet.http)
internalDoFilter:227, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:53, WsFilter (org.apache.tomcat.websocket.server)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:76, ADSFilter (com.manageengine.ads.fw.filter)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:300, PassTrixFilter (com.adventnet.passtrix.client)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:414, SecurityFilter (com.adventnet.iam.security)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:34, NTLMV2CredentialAssociationFilter (com.adventnet.authentication)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:155, NTLMV2Filter (com.adventnet.authentication)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:118, MSPOrganizationFilter (com.adventnet.passtrix.client)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:149, PassTrixUrlRewriteFilter (com.adventnet.passtrix.client)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:109, SetCharacterEncodingFilter (org.apache.catalina.filters)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:32, ClientFilter (com.adventnet.cp)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:80, ParamWrapperFilter (com.adventnet.filters)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:51, RememberMeFilter (com.adventnet.authentication.filter)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
doFilter:65, AssociateCredential (com.adventnet.authentication.filter)
internalDoFilter:189, ApplicationFilterChain (org.apache.catalina.core)
doFilter:162, ApplicationFilterChain (org.apache.catalina.core)
invoke:197, StandardWrapperValve (org.apache.catalina.core)
invoke:97, StandardContextValve (org.apache.catalina.core)
invoke:540, AuthenticatorBase (org.apache.catalina.authenticator)
invoke:135, StandardHostValve (org.apache.catalina.core)
invoke:92, ErrorReportValve (org.apache.catalina.valves)
invoke:687, AbstractAccessLogValve (org.apache.catalina.valves)
invoke:261, SingleSignOn (org.apache.catalina.authenticator)
invoke:78, StandardEngineValve (org.apache.catalina.core)
service:357, CoyoteAdapter (org.apache.catalina.connector)
service:382, Http11Processor (org.apache.coyote.http11)
process:65, AbstractProcessorLight (org.apache.coyote)
process:895, AbstractProtocol$ConnectionHandler (org.apache.coyote)
doRun:1681, Nio2Endpoint$SocketProcessor (org.apache.tomcat.util.net)
run:49, SocketProcessorBase (org.apache.tomcat.util.net)
processSocket:1171, AbstractEndpoint (org.apache.tomcat.util.net)
completed:104, SecureNio2Channel$HandshakeReadCompletionHandler (org.apache.tomcat.util.net)
completed:97, SecureNio2Channel$HandshakeReadCompletionHandler (org.apache.tomcat.util.net)
invokeUnchecked:126, Invoker (sun.nio.ch)
run:218, Invoker$2 (sun.nio.ch)
run:112, AsynchronousChannelGroupImpl$1 (sun.nio.ch)
runWorker:1191, ThreadPoolExecutor (org.apache.tomcat.util.threads)
run:659, ThreadPoolExecutor$Worker (org.apache.tomcat.util.threads)
run:61, TaskThread$WrappingRunnable (org.apache.tomcat.util.threads)
run:748, Thread (java.lang)
poc不放了 懂得都懂。
其实刚开始找的并不直接是漏洞点,而是在找xml parse的点 com.adventnet.tools.prevalent.InputFileParser#parse

经过多次调试发现这个类自己实现了startElement和endElement,并不会调用endValueTag(),进而没有type parse一说,所以根本不会触发反序列化。
后来重新看了历史的漏洞文章,换了思路直接找org.apache.xmlrpc.webserver.XmlRpcServlet的引用就发现了漏洞点,瞬间感觉自己太蠢了。u1s1,静态软件分析工具还是有用。
如有侵权请联系:admin#unsafe.sh