
Executive SummaryMicrosoft i 2022-7-28 07:0:42 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:79 收藏

Executive Summary
Microsoft introduced patches for several critical vulnerabilities in their April and May 2022 security updates, including the following vulnerabilities:
- CVE-2022-26809: An unauthorized attacker can exploit this vulnerability by sending a specially crafted Remote Procedure Call (RPC) to remotely execute arbitrary code on the vulnerable device.
- CVE-2022-26923: A low-privileged user can escalate privilege to a domain administrator in a default Active Directory environment with the “Active Directory Certificate Services” server role installed.
- CVE-2022-26925: Unauthenticated attackers can remotely exploit and force domain controllers to authenticate them via the Windows NT LAN Manager (NTLM) security protocol.
We highly recommend that customers apply these security updates to address these issues.
Palo Alto Networks customers receive protections from these vulnerabilities through the Next-Generation Firewall with a Threat Prevention subscription, Cortex XDR and other products.
| CVEs discussed | CVE-2022-26809, CVE-2022-26923, CVE-2022-26925 |
Table of Contents
Affected Versions
Mitigations for CVE-2022-26809, CVE-2022-26923, CVE-2022-26925
Exploits
Conclusion
Additional Resources
Affected Versions
CVE-2022-26809
The following versions of the Microsoft Windows OS are vulnerable to CVE-2022-26809:
Windows 7 for 32-bit systems Service Pack 1
Windows 7 for x64-based systems Service Pack 1
Windows 8.1 for 32-bit systems
Windows RT 8.1
Windows 8.1 for x64-based systems
Windows 10 Version 20H2 for ARM64-based systems
Windows 10 Version 1909 for ARM64-based systems
Windows 10 Version 1809 for x64-based systems
Windows 10 for 32-bit systems
Windows 10 Version 21H2 for x64-based systems
Windows 10 Version 21H2 for ARM64-based systems
Windows 10 Version 21H2 for 32-bit systems
Windows 10 Version 1809 for 32-bit systems
Windows 10 Version 21H1 for 32-bit systems
Windows 10 Version 21H1 for ARM64-based systems
Windows 10 Version 21H1 for x64-based systems
Windows 10 Version 20H2 for 32-bit systems
Windows 10 Version 20H2 for x64-based systems
Windows 10 Version 1607 for x64-based systems
Windows 10 Version 1607 for 32-bit systems
Windows 10 for x64-based systems
Windows 10 Version 1909 for x64-based systems
Windows 10 Version 1909 for 32-bit systems
Windows 10 Version 1809 for ARM64-based systems
Windows 11 for ARM64-based systems
Windows 11 for x64-based systems
Windows Server 2008 R2 for x64-based systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based systems Service Pack 1
Windows Server 2008 for x64-based systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based systems Service Pack 2
Windows Server 2008 for 32-bit systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit systems Service Pack 2
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2016
Windows Server 2016 (Server Core installation)
Windows Server, version 20H2 (Server Core Installation)
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows Server 2022 (Server Core installation)
Windows Server 2022
CVE-2022-26923
The following versions of the Microsoft Windows OS are vulnerable to CVE-2022-26923:
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows RT 8.1
Windows 8.1 for x64-based systems
Windows 8.1 for 32-bit systems
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows 10 Version 1607 for x64-based systems
Windows 10 Version 1607 for 32-bit systems
Windows 10 for x64-based systems
Windows 10 for 32-bit systems
Windows 10 Version 21H2 for x64-based systems
Windows 10 Version 21H2 for ARM64-based systems
Windows 10 Version 21H2 for 32-bit systems
Windows 11 for ARM64-based systems
Windows 11 for x64-based systems
Windows Server, version 20H2 (Server Core Installation)
Windows 10 Version 20H2 for ARM64-based systems
Windows 10 Version 20H2 for 32-bit systems
Windows 10 Version 20H2 for x64-based systems
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows 10 Version 21H1 for 32-bit systems
Windows 10 Version 21H1 for ARM64-based systems
Windows 10 Version 21H1 for x64-based systems
Windows 10 Version 1909 for ARM64-based systems
Windows 10 Version 1909 for x64-based systems
Windows 10 Version 1909 for 32-bit systems
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 1809 for ARM64-based systems
Windows 10 Version 1809 for x64-based systems
Windows 10 Version 1809 for 32-bit systems
CVE-2022-26925
The following versions of the Microsoft Windows OS are vulnerable to CVE-2022-26925:
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based systems Service Pack 1 (Server Core installation)
Windows Server 2008 R2 for x64-based systems Service Pack 1
Windows Server 2008 for x64-based systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based systems Service Pack 2
Windows Server 2008 for 32-bit systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit systems Service Pack 2
Windows RT 8.1
Windows 8.1 for x64-based systems
Windows 8.1 for 32-bit systems
Windows 7 for x64-based systems Service Pack 1
Windows 7 for 32-bit systems Service Pack 1
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows 10 Version 1607 for x64-based systems
Windows 10 Version 1607 for 32-bit systems
Windows 10 for x64-based systems
Windows 10 for 32-bit systems
Windows 10 Version 21H2 for x64-based systems
Windows 10 Version 21H2 for ARM64-based systems
Windows 10 Version 21H2 for 32-bit systems
Windows 11 for ARM64-based systems
Windows 11 for x64-based systems
Windows Server, version 20H2 (Server Core Installation)
Windows 10 Version 20H2 for ARM64-based systems
Windows 10 Version 20H2 for 32-bit systems
Windows 10 Version 20H2 for x64-based systems
Windows Server 2022 (Server Core installation)
Windows Server 2022
Windows 10 Version 21H1 for 32-bit systems
Windows 10 Version 21H1 for ARM64-based systems
Windows 10 Version 21H1 for x64-based systems
Windows 10 Version 1909 for ARM64-based systems
Windows 10 Version 1909 for x64-based systems
Windows 10 Version 1909 for 32-bit systems
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 1809 for ARM64-based systems
Windows 10 Version 1809 for x64-based systems
Windows 10 Version 1809 for 32-bit systems
Mitigations for CVE-2022-26809, CVE-2022-26923, CVE-2022-26925
Microsoft released patches for CVE-2022-26809, CVE-2022-26923 and CVE-2022-26925. All three vulnerabilities and exploit details are publicly available, and CVE-2022-26925 was detected as being exploited in the wild. We strongly recommend patching them as soon as possible.
Exploits
CVE-2022-26809 – RPC Remote Code Execution Vulnerability
In Microsoft’s April security update, there was a severe RPC vulnerability that could lead to remote code execution. This would provide an adversary with a remote attack surface, allowing them to attack the Windows SMB service remotely and execute code. This threat is not limited to Windows SMB service and may affect other services using the vulnerable RPC component.
On May 1, 2022, we observed a public proof of concept (PoC) published on GitHub. The researcher conducted analysis of CVE-2022-26809 and created the PoC to trigger the vulnerable function OSF_SCALL::GetCoalescedBuffer. The PoC is created based on an RPC sample code, Hello, from Microsoft. Since all interfaces for programs using RPC must be defined in Microsoft Interface Definition Language (MIDL) and compiled with the MIDL compiler, the researcher added a new pipe type and several functions in the IDL file. This is because the server side needs to use pipe in order to trigger the vulnerability. The related modifications are shown in Figure 1:
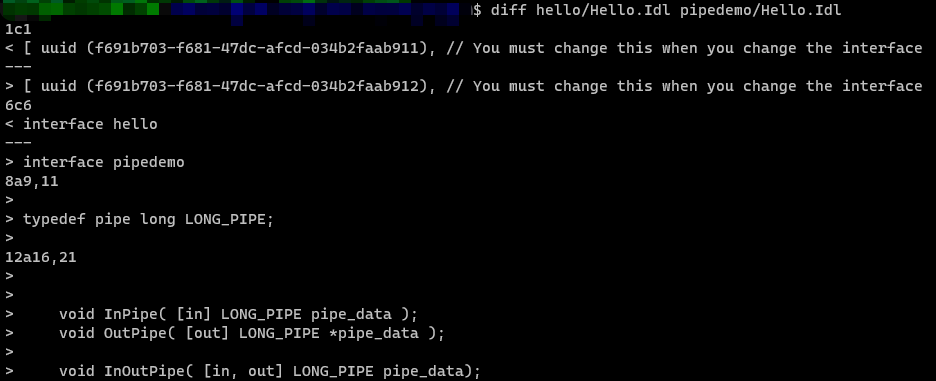
The PoC client utilizes impacket.dcerpc.v5.rpcrt to send the data. Additionally, the researcher modified the packet handling logic of the rpcrt library. Although the PoC only works on a customized RPC server and a successful exploitation of this vulnerability requires specific settings on the server side, it could be modified by an attacker to construct a feasible exploit for the default Windows service. We strongly recommend patching CVE-2022-26809 as soon as possible.
CVE-2022-26923 – Active Directory Domain Service Privilege Escalation Vulnerability
This vulnerability allows a low-privileged user to escalate privileges to a domain administrator in a default Active Directory environment with the “Active Directory Certificate Services” server role installed. It is a logic issue that gets a valid certificate by using a fake domain controller, dNSHostName, and then gets the domain controller privileges by authenticating the certificate to the domain controller. Microsoft fixed CVE-2022-26923 in May’s security update but the vulnerability and exploit details are publicly available. We strongly recommend patching it as soon as possible.
CVE-2022-26925 – Windows LSA Spoofing Vulnerability
An unauthenticated attacker could call a method on the LSARPC interface and coerce the domain controller to authenticate the attacker using NTLM. Once the attacker gets the NTLM hash by the NTLM relay attack, the attacker can further use the leaked main controller NTLM hash to attack the system. CVE-2022-26925 was detected as being exploited in the wild and is publicly available. Microsoft fixed this vulnerability in May’s security update. We strongly recommend patching it as soon as possible.
Conclusion
CVE-2022-26809 is still being actively monitored due to its potential to be exploited in widespread attacks. Given the information currently available, this vulnerability may have a high impact in the future. RPC is widely used by a wide variety of Windows and Windows Server versions. Besides that, the vulnerable rpcrt4.dll is not only used by Microsoft services but also by other applications. CVE-2022-26923 and CVE-2022-26925 exploits are publicly available, and it’s only a matter of time until those vulnerabilities are abused by attackers. Users are encouraged to take all necessary steps to ensure they are protected against these vulnerabilities.
The Palo Alto Networks Next-Generation Firewall with a Threat Prevention subscription can block the attack traffic related to these vulnerabilities.
- CVE-2022-26809 Coverage: Threat ID 92490 (Application and Threat content update 8557)
- CVE-2022-26923 Coverage: Threat ID 92548 (Application and Threat content update 8568)
- CVE-2022-26925 Coverage: Threat ID 92549 (Application and Threat content update 8568)
Palo Alto Networks Cortex customers are protected from CVE-2022-26923 and CVE-2022-26925.
Additional Resources
Remote Procedure Call Runtime Remote Code Execution Vulnerability – Microsoft
Active Directory Domain Services Elevation of Privilege Vulnerability – Microsoft
Certifried: Active Directory Domain Privilege Escalation (CVE-2022–26923) – IFCR
PetitPotam – GitHub
Microsoft fixes new PetitPotam Windows NTLM Relay attack vector – BleepingComputer
Windows LSA Spoofing Vulnerability – Microsoft
Remote procedure call (RPC) – Microsoft
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh