
This post is also available i 2022-7-26 18:0:49 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:47 收藏
This post is also available in: 日本語 (Japanese)
Executive Summary
Software vulnerabilities remain a key avenue of initial access for attackers according to the 2022 Unit 42 Incident Response Report. While this underscores the need for organizations to operate with a well-defined patch management strategy, we’ve observed that attackers are increasingly quick to exploit high-profile zero-day vulnerabilities, further increasing the time pressure on organizations when a new vulnerability is disclosed.
The 2022 Unit 42 Incident Response Report analyzes more than 600 incident response cases conducted over the past year alongside in-depth interviews with our incident response experts to identify key patterns and trends that can be used by defenders to prioritize where and how to deploy protections.
Here, we share key insights from the report, including statistics on suspected means of initial access among our cases, which software vulnerabilities attackers exploited most and our observations of how attacker behavior around zero-day vulnerabilities is shifting. For more in-depth analysis, download the full report.
Palo Alto Networks customers receive protections against the specific vulnerabilities discussed in this post through Cortex XDR, Prisma Cloud, Cloud Delivered Security Services and other products. You can also take preventative steps by requesting any of Unit 42’s cyber risk management services.
Table of Contents
Software Vulnerabilities and Initial Access
Vulnerabilities Most Commonly Exploited for Initial Access
Time to Patch Is Getting Shorter
Conclusion
Protections and Mitigations
Additional Resources
Software Vulnerabilities and Initial Access
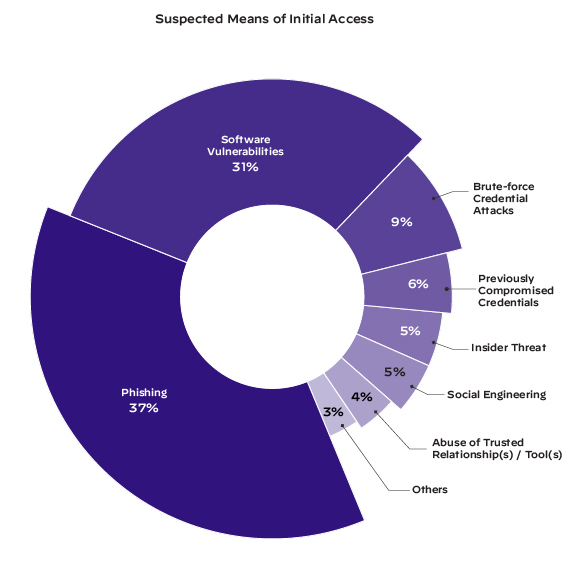
Software vulnerabilities remain one of the top observed access vectors for threat actors. We found that they were the suspected initial access vector of intrusion in 31% of our cases, second only to phishing at 37%.
Vulnerabilities Most Commonly Exploited for Initial Access
In cases where responders positively identified the vulnerability exploited by the threat actor, over 87% of them fell into one of six CVE categories, as shown in Figure 2.
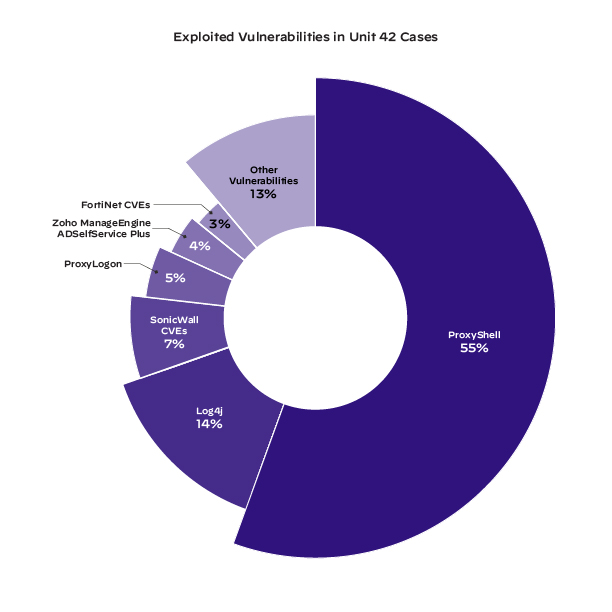
Note that top categories include Log4j and Zoho ManageEngine ADSelfService Plus, both of which were high-profile zero-day vulnerabilities disclosed toward the end of 2021.
Anytime a new vulnerability is publicized, our threat intelligence team observes widespread scanning for vulnerable systems. Our security consultants say they’re also seeing threat actors – ranging from the sophisticated to the script kiddies – moving quickly to take advantage of publicly available PoCs to attempt exploits.
Time to Patch Is Getting Shorter
While some threat actors continue to rely on older, unpatched vulnerabilities, we’re increasingly seeing that the time from vulnerability to exploit is getting shorter. In fact, it can practically coincide with the reveal if the vulnerabilities themselves and the access that can be achieved by exploiting them are significant enough. For example, Palo Alto Networks released a Threat Prevention signature for the F5 BIG-IP Authentication Bypass Vulnerability (CVE-2022-1388), and within just 10 hours, the signature triggered 2,552 times due to vulnerability scanning and active exploitation attempts.
The 2022 Attack Surface Management Threat Report found that attackers typically start scanning for vulnerabilities within 15 minutes of a CVE being announced.
Additionally, end-of-life (EoL) systems remain unpatchable and available to an opportunistic attacker for exploitation. For example, the same report found that nearly 32% of exposed organizations are running the EoL version of Apache Web Server, which is open for remote code execution from the vulnerabilities CVE-2021-41773 and CVE-2021-42013.
We expect this trend to continue and be augmented by the ongoing increase in internet-exposed attack surface.
Conclusion
Organizations may have previously grown used to taking time between the disclosure of a vulnerability and patching it, but while it’s still necessary to perform due diligence on a patch, attackers’ ability to scan the internet in search of vulnerable systems means it’s more important than ever to shorten the time it takes to patch. Organizations need to ramp up patch management and orchestration to try to close these known holes as soon as possible.
An attack surface management solution can help organizations identify vulnerable internet-exposed systems and can often catch systems that organizations may not be aware are running on the network.
The information in this blog is based on the 2022 Unit 42 Incident Response Report, which includes in-depth information on attacker behavior gathered from hundreds of incident response cases as well as a series of interviews with experienced incident responders. Defenders can use these insights to prioritize resources and close cybersecurity gaps that attackers look for and commonly exploit.
The report includes:
- The seven most common contributing factors when a breach occurs.
- Capabilities attackers most commonly use after initially compromising a network.
- Our incident responders’ predictions for attack trends in the year to come.
- The six key protections our experts recommend that organizations put in place.
Download the full 2022 Unit 42 Incident Response Report to learn more, and register to attend the 2022 Incident Response Report webinar to hear our security experts discuss the key findings in the report and answer your questions live.
Protections and Mitigations
Palo Alto Networks customers can take advantage of Cortex Xpanse for attack surface management. Customers also receive protections against the specific vulnerabilities discussed in this post through Cortex XDR, Prisma Cloud, Cloud Delivered Security Services and other products.
If you think you may have been impacted by a cyber incident or have specific concerns about any of the vulnerabilities discussed here, please contact Unit 42 to connect with a team member. The Unit 42 Incident Response team is available 24/7/365. If you have cyber insurance, you can request Unit 42 by name. You can also take preventative steps by requesting any of our cyber risk management services.
Additional Resources
Today’s Cyberthreats: Ransomware, BEC Continue to Disrupt
If You Know What Attackers are After, You Know What to Protect Most
Key Considerations When Building an Incident Response Plan
Cloud Incident Response Readiness Evalutation
Unit 42 Incident Response Methodology
Unit 42 Retainer Datasheet
Other Recent Unit 42 Reports
Unit 42 Cloud Threat Report, Volume 6
2022 Unit 42 Ransomware Threat Report
2022 Unit 42 Network Threat Trends Research Report
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh