2022-7-21 19:0:11 Author: www.sentinelone.com(查看原文) 阅读量:124 收藏
By Jim Walter & Aleksandar Milenkoski
LockBit 3.0 ransomware (aka LockBit Black) is an evolution of the prolific LockBit ransomware-as-a-service (RaaS) family, which has roots that extend back to BlackMatter and related entities. After critical bugs were discovered in LockBit 2.0 in March 2022, the authors began work on updating their encryption routines and adding several new features designed to thwart researchers. In June 2022, LockBit 3 caught the interest of the media as the ransomware operators announced they were offering a ‘bug bounty’ to researchers. In this post, we provide an overview of the LockBit 3.0 ransomware update and offer a technical dive for researchers into LockBit 3.0’s anti-analysis and evasion features.
LockBit 3.0 Changes and New Features Since LockBit 2.0
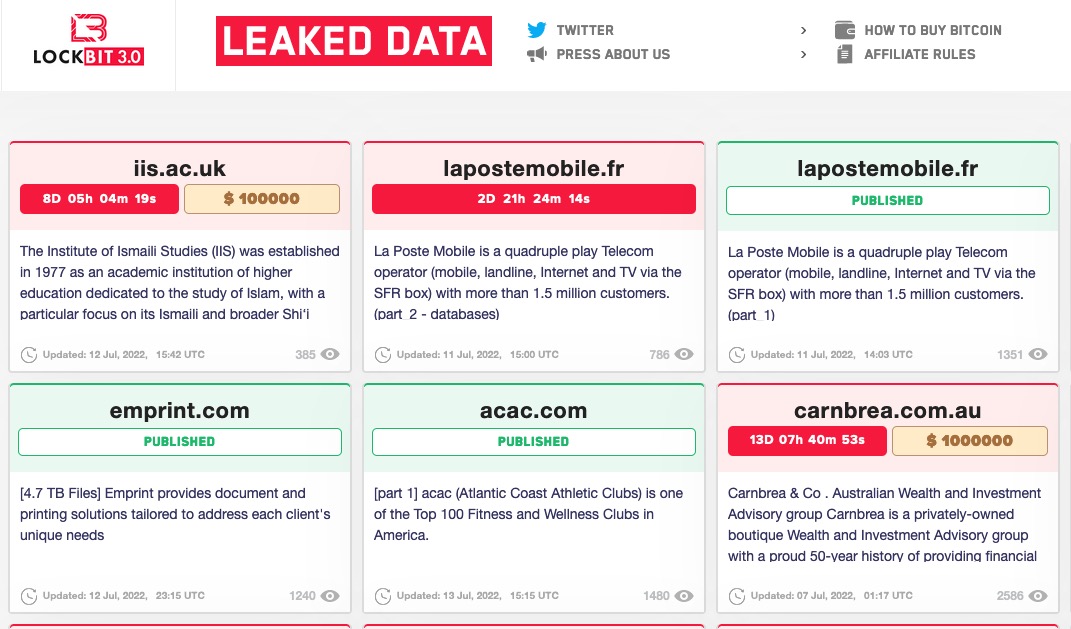
Around June of 2022, operators and affiliates behind LockBit ransomware began the shift to LockBit 3.0. Adoption of LockBit 3.0 by affiliates has been rapid, and numerous victims have been identified on the new “Version 3.0” leak sites, a collection of public blogs naming non-compliant victims and leaking extracted data.

In order to improve resilience, the operators have been aggressive with regards to standing up multiple mirrors for their leaked data and publicizing the site URLs.
LockBit has also added an instant search tool to their leaks site.

The authors of LockBit 3.0 have introduced new management features for affiliates and added Zcash for victim payments in addition to Monero and Bitcoin.
The ransomware authors also claim to have opened a public “bug bounty” program. Ostensibly, this appears to be an effort to improve the quality of the malware, and financially reward those that assist.
Lockbit ransomware group announced today Lockbit 3.0 is officially released with the message: "Make Ransomware Great Again!"
Additionally, Lockbit has launched their own Bug Bounty program paying for PII on high-profile individuals, web security exploits, and more… pic.twitter.com/ByNFdWe4Ys
— vx-underground (@vxunderground) June 26, 2022
On top of that, there is a purported $1 million reward on offer to anyone who can uncover the identity of the program affiliate manager. Understandably, given the criminal nature of the operators, would-be researchers may find that reporting bugs to a crimeware outfit may not lead to the promised payout but could lead to criminal charges from law enforcement.
LockBit 3.0 Payloads and Encryption
The updated LockBit payloads retain all the prior functionality of LockBit 2.0.
Initial delivery of the LockBit ransomware payloads is typically handled via 3rd party frameworks such as Cobalt Strike. As with LockBit 2.0, we have seen infections occur down the chain from other malware components as well, such as a SocGholish infection dropping Cobalt Strike, which in turn delivers the LockBit 3 ransomware.
The payloads themselves are standard Windows PE files with strong similarities to prior generations of LockBit as well as BlackMatter ransomware families.

LockBit ransomware payloads are designed to execute with administrative privileges. In the event that the malware does not have the necessary privileges, a UAC bypass will be attempted (CMSTP).
LockBit 3.0 achieves persistence via installation of System Services. Each execution of the payload will install multiple services. We have observed the following service names in conjunction with LockBit 3.0 ransomware payloads.
SecurityHealthService Sense sppsvc WdBoot WdFilter WdNisDrv WdNisSvc WinDefend wscsvc vmicvss vmvss VSS EventLog
As with previous versions, LockBit 3.0 will attempt to identify and terminate specific services if found. The following service names are targeted for termination in analyzed LockBit 3.0 samples:
backup GxBlr GxCIMgr GxCVD GxFWD GxVss memtas mepocs msexchange sophos sql svc$ veeam vss
In addition, the following processes are targeted for termination:
agntsvc dbeng50 dbsnmp encsvc excel firefox infopath isqlplussvc msaccess mspub mydesktopqos mydesktopservice notepad ocautoupds ocomm ocssd onenote oracle outlook powerpnt registry sqbcoreservice steam synctime tbirdconfig thebat thunderbird visio winword wordpad xfssvccon
LockBit 3.0 writes a copy of itself to the %programdata% directory, and subsequently launches from this process.
The encryption phase is extremely rapid, even when spreading to adjacent hosts. The ransomware payloads were able to fully encrypt our test host in well under a minute.
On execution, the LockBit 3.0 ransomware will drop newly-formatted ransom notes along with a change to the desktop background. Interestingly, notepad and wordpad are included in the list of prescribed processes as noted above. Therefore, if a victim attempts to open the ransom note immediately after it is dropped, it will promptly close since the process is blocked until the ransomware completes its execution.
The new LockBit 3.0 ransomware desktop wallpaper is a simple text message on a black background.

The extension appended to newly encrypted files will also differ per campaign or sample. For example, we have seen “HLJkNskOq” and “futRjC7nx”. Both encrypted files and the ransom notes will be prepended with the campaign-specific string.
futRjC7nx.README HLJkNskOq.README
During our analysis, we observed infected machines shutting down ungracefully approximately 10 minutes after the ransomware payload was launched. This behavior may vary per sample, but it is worth noting.
Post-infection, LockBit 3.0 victims are instructed to make contact with their attacker via their TOR-based “support” portal.

LockBit 3 Anti-Analysis & Evasion
The LockBit 3.0 ransomware uses a variety of anti-analysis techniques to hinder static and dynamic analysis, and exhibits similarities to the BlackMatter ransomware in this regard. These techniques include code packing, obfuscation and dynamic resolution of function addresses, function trampolines, and anti-debugging techniques. In this section, we cover some of the anti-analysis techniques that LockBit 3.0 uses.
LockBit 3.0 payloads require a specific passphrase to execute. The passphrase is unique to each sample or campaign and serves to hinder dynamic and sandbox analysis if the passphrase has not been recovered along with the sample. A similar technique has been used by Egregor and BlackCat ransomware. The passphrase is provided upon execution via the -pass parameter. For example,
lockbit.exe -pass XX66023ab2zyxb9957fb01de50cdfb6
The LockBit 3.0 ransomware decrypts the contents of its executable segments at runtime using an XOR mask. The images below show the content of the ransomware’s .text executable segment before (label 1) and after (label 2) the ransomware has decrypted the segment content. The .text segment starts at the virtual address 0x401000.


LockBit 3.0 also first stores in heap memory and then uses trampolines for executing functions, for example, the Windows system calls NtSetInformationThread and ZwProtectVirtualMemory. The ransomware obfuscates the function addresses that the trampolines execute using the XOR and/or bit rotation obfuscation technique.

Several techniques are implemented for detecting the presence of a debugger and hindering dynamic analysis. For example, the ransomware evaluates whether heap memory parameters that indicate the presence of a debugger are set. Such flags are HEAP_TAIL_CHECKING_ENABLED (0x20) and HEAP_VALIDATE_PARAMETERS_ENABLED (0x40000000).
LockBit 3.0 examines the ForceFlags value in its PEB (Process Environment Block) to evaluate whether HEAP_VALIDATE_PARAMETERS_ENABLED is set.

The ransomware also evaluates whether the 0xABABABAB byte signature is present at the end of heap memory blocks that it has previously allocated. The presence of this byte signature means that HEAP_TAIL_CHECKING_ENABLED is set.

The LockBit 3.0 ransomware executes the NtSetInformationThread function through a trampoline, such that the ThreadHandle and ThreadInformationClass function parameters have the values of 0xFFFFFFFE and 0x11 (ThreadHideFromDebugger). This stops the flow of events from the current ransomware’s thread to an attached debugger, which effectively hides the thread from the debugger and hinders dynamic analysis.

In addition, LockBit scrambles the implementation of the DbgUiRemoteBreakin function to disable debuggers trying to attach to the ransomware process. When a debugger attaches to a process, LockBit 3.0 ransomware:
- Resolves the address of
DbgUiRemoteBreakin. - Executes the
ZwProtectVirtualMemoryfunction through a trampoline to apply the PAGE_EXECUTE_READWRITE (0x40) protection to the first 32 bytes of the memory region where the implementation ofDbgUiRemoteBreakinresides. This makes the bytes writable. - Executes the
SystemFunction040(RtlEncryptMemory) function through a trampoline to encrypt the bytes that the ransomware has previously made writable. This scrambles the implementation of theDbgUiRemoteBreakinfunction and disables debuggers to attach to the ransomware process.

The images below depict the implementation of the DbgUiRemoteBreakin function before (label 1) and after (label 2) the LockBit 3.0 ransomware has modified the implementation of the function.


Conclusion
LockBit has fast become one of the more prolific ransomware-as-a-service operators out there, taking over from Conti after the latter’s fractious fallout in the wake of the Russian invasion of Ukraine.
LockBit’s developers have shown that they are quick to respond to problems in the product they are offering and that they have the technical know-how to keep evolving. The recent claim to be offering a ‘bug bounty’, whatever its true merits, displays a savvy understanding of their own audience and the media landscape that surrounds the present tide of crimeware and enterprise breaches.
Short of intervention by law enforcement, we expect to see LockBit around for the forseeable future and further iterations of what is undoubtedly a very successful RaaS operation. As with all ransomware, prevention is better than cure, and defenders are encouraged to ensure that they have comprehensive ransomware protection in place. SentinelLabs will continue to offer updates and reports on LockBit activity as it develops.
Indicators of Compromise
SHA256
f9b9d45339db9164a3861bf61758b7f41e6bcfb5bc93404e296e2918e52ccc10
a56b41a6023f828cccaaef470874571d169fdb8f683a75edd430fbd31a2c3f6e
d61af007f6c792b8fb6c677143b7d0e2533394e28c50737588e40da475c040ee
SHA1
ced1c9fabfe7e187dd809e77c9ca28ea2e165fa8
371353e9564c58ae4722a03205ac84ab34383d8c
c2a321b6078acfab582a195c3eaf3fe05e095ce0
.ONION domains
lockbitapt2d73krlbewgv27tquljgxr33xbwwsp6rkyieto7u4ncead[.]onion
lockbitapt2yfbt7lchxejug47kmqvqqxvvjpqkmevv4l3azl3gy6pyd[.]onion
lockbitapt34kvrip6xojylohhxrwsvpzdffgs5z4pbbsywnzsbdguqd[.]onion
lockbitapt5x4zkjbcqmz6frdhecqqgadevyiwqxukksspnlidyvd7qd[.]onion
lockbitapt6vx57t3eeqjofwgcglmutr3a35nygvokja5uuccip4ykyd[.]onion
lockbitapt72iw55njgnqpymggskg5yp75ry7rirtdg4m7i42artsbqd[.]onion
lockbitaptawjl6udhpd323uehekiyatj6ftcxmkwe5sezs4fqgpjpid[.]onion
lockbitaptbdiajqtplcrigzgdjprwugkkut63nbvy2d5r4w2agyekqd[.]onion
lockbitaptc2iq4atewz2ise62q63wfktyrl4qtwuk5qax262kgtzjqd[.]onion
lockbit7z2jwcskxpbokpemdxmltipntwlkmidcll2qirbu7ykg46eyd[.]onion
lockbitsupa7e3b4pkn4mgkgojrl5iqgx24clbzc4xm7i6jeetsia3qd[.]onion
lockbitsupdwon76nzykzblcplixwts4n4zoecugz2bxabtapqvmzqqd[.]onion
lockbitsupn2h6be2cnqpvncyhj4rgmnwn44633hnzzmtxdvjoqlp7yd[.]onion
lockbitsupo7vv5vcl3jxpsdviopwvasljqcstym6efhh6oze7c6xjad[.]onion
lockbitsupq3g62dni2f36snrdb4n5qzqvovbtkt5xffw3draxk6gwqd[.]onion
lockbitsupqfyacidr6upt6nhhyipujvaablubuevxj6xy3frthvr3yd[.]onion
lockbitsupt7nr3fa6e7xyb73lk6bw6rcneqhoyblniiabj4uwvzapqd[.]onion
lockbitsupuhswh4izvoucoxsbnotkmgq6durg7kficg6u33zfvq3oyd[.]onion
lockbitsupxcjntihbmat4rrh7ktowips2qzywh6zer5r3xafhviyhqd[.]onion
MITRE ATT&CK
T1547.001 – Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
T1543.003 – Create or Modify System Process: Windows Service
T1055 – Process Injection
T1070.001 – Indicator Removal on Host: Clear Windows Event Logs
T1622 – Debugger Evasion
T1548.002 – Abuse Elevation Control Mechanism: Bypass User Account Control
T1485 – Data Destruction
T1489 – Service Stop
T1490 – Inhibit System Recovery
T1003.001 – OS Credential Dumping: LSASS Memory
T1078.002 – Valid Accounts: Domain Accounts
T1078.001 – Valid Accounts: Default Accounts
T1406.002 – Obfuscated Files or Information: Software Packing
T1218.003 – System Binary Proxy Execution: CMSTP
T1047 – Windows Management Instrumentation
T1119 – Automated Collection
如有侵权请联系:admin#unsafe.sh