Mobile forensics is not limited to phones and table 2022-7-20 14:55:17 Author: blog.elcomsoft.com(查看原文) 阅读量:28 收藏
Mobile forensics is not limited to phones and tablets. Many types of other gadgets, including IoT devices, contain tons of valuable data. Such devices include smart watches, media players, routers, smart home devices, and so on. In this article, we will cover the extraction of an Apple TV 4K, one of the most popular digital media players.
We already covered Apple TV forensics in the past; check out the following articles:
- Apple TV and Apple Watch Forensics 01: Acquisition
- Apple TV Forensics 03: Analysis
- Forensic Acquisition of Apple TV with checkra1n Jailbreak
- Jailbreaking Apple TV 4K
There are generally two methods to access data stored in an Apple TV: logical acquisition (media files with the metadata, diagnostics logs), and full file system extraction. The latter required jailbreaking (see above), which is limited to certain versions of tvOS. We have the full checkm8 support for all models up to and including the Apple TV 4K, which means that the version of tvOS no longer matters. Only the latest Apple TV HDR is not vulnerable.
The problem
Everything was relatively simple up to and including the Apple TV 4. The 4K version, however, has two problems:
- No USB port
- Difficult to enter DFU
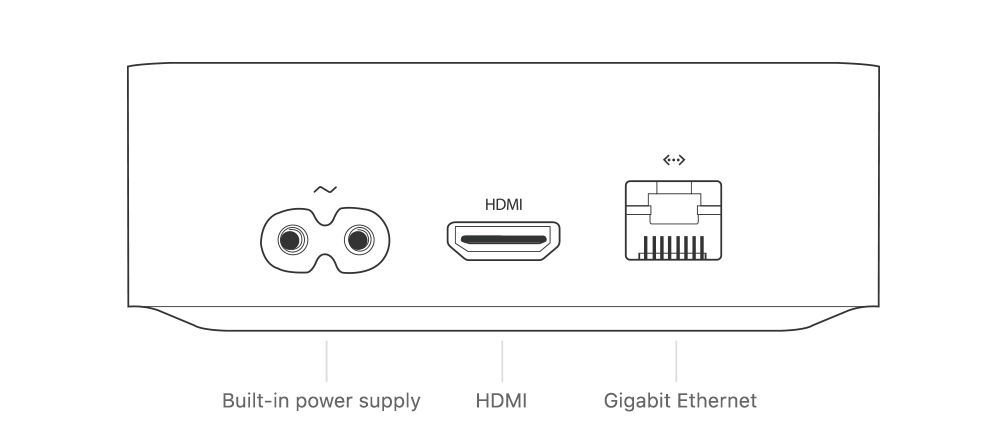
The first problem has been resolved, as a hidden port was discovered under the Ethernet (RJ45) socket. A special connector is now available, the GoldenEye (or Foxlink X892), which is available for around 40€. With this adapter, you can connect your Apple TV 4K using a standard lightning cable and perform logical acquisition (the good news is that the Apple TV cannot be locked with a passcode).
The second problem is more serious. In order to run the checkm8 exploit, the device must be in DFU mode. The Apple TV 4 and older models can be placed into DFU using the remote control with a special combination of buttons. This is not the case for the Apple TV 4K.
One way to place the 4K model into DFU uses a special breakout cable (available at around $70), but the installation is difficult and requires some soldering skills.
The solution
Fortunately, there is an easier way, revealed by @matteyeux about two years ago. Apart of the GoldenEye cable, you will also need the DCSD cable; we covered it in The Mysterious Apple DCSD Cable Demystified. The adapter is easily available at around 20€.
So here is how to place the AppleTV 4K into DFU:
- Disconnect Apple TV 4K from the power source
- Connect the DCSD cable to the computer’s USB port
- Connect the GoldenEye adapter to the DCSD cable (using Lightning)
- Connect the GoldenEye to the Apple TV 4K
- Connect the Apple TV 4K to the power source
And there we go: the Apple TV 4K is automatically boots into DFU!
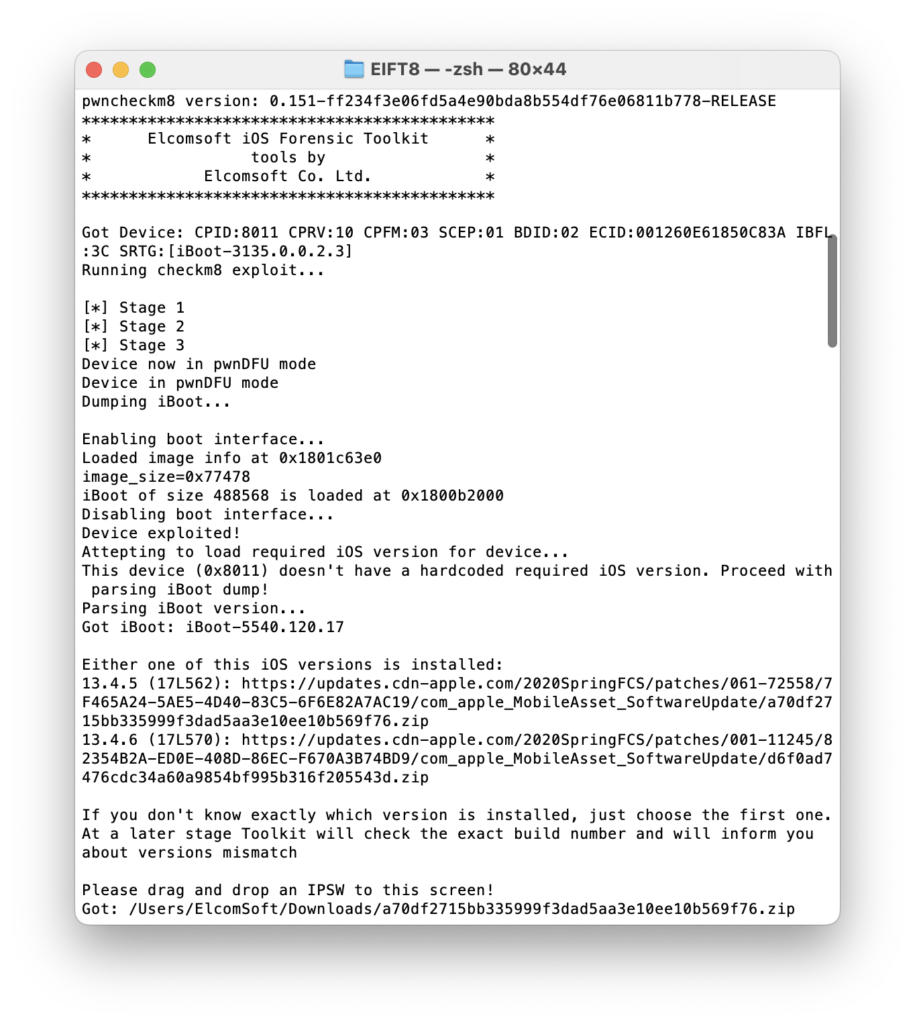
You can now install the checkra1n jailbreak if your Apple TV runs tvOS 14 or older, or use the latest Elcomsoft iOS Forensic Toolkit 8.0 beta to perform a forensically sound keychain and file system extraction. As easy as that.
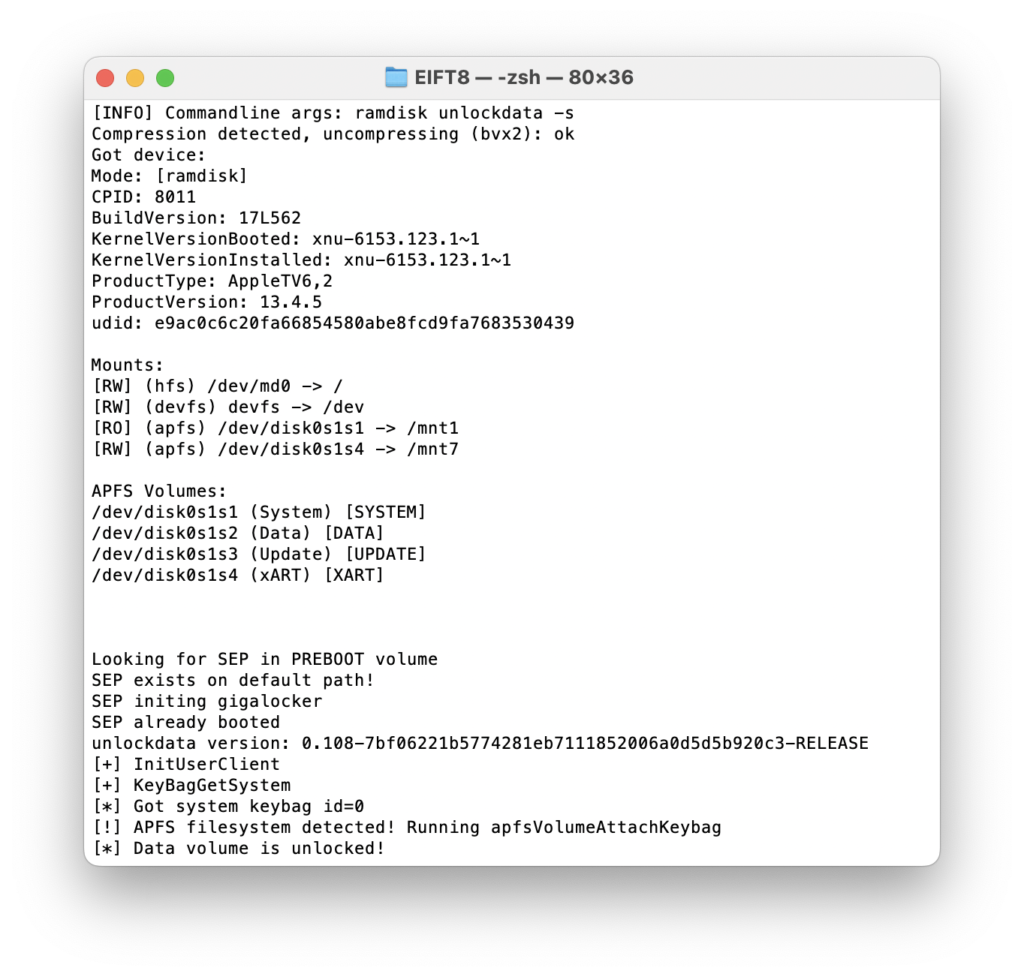
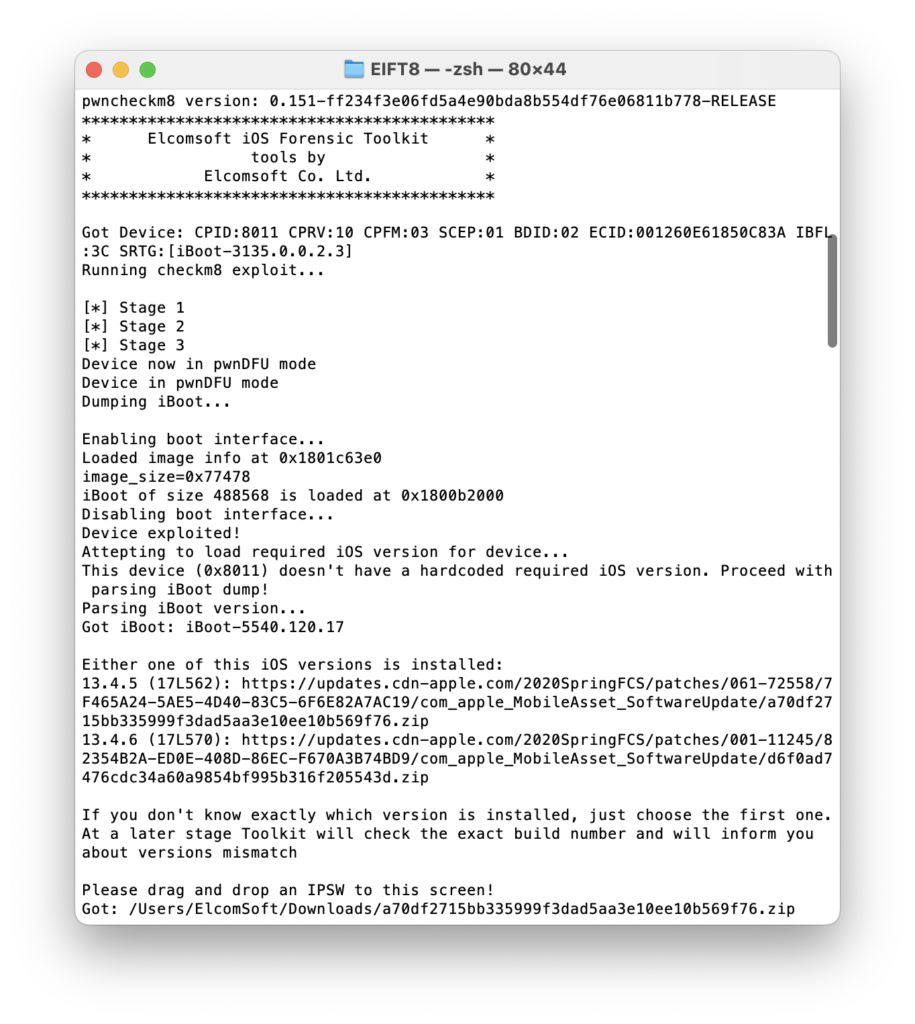
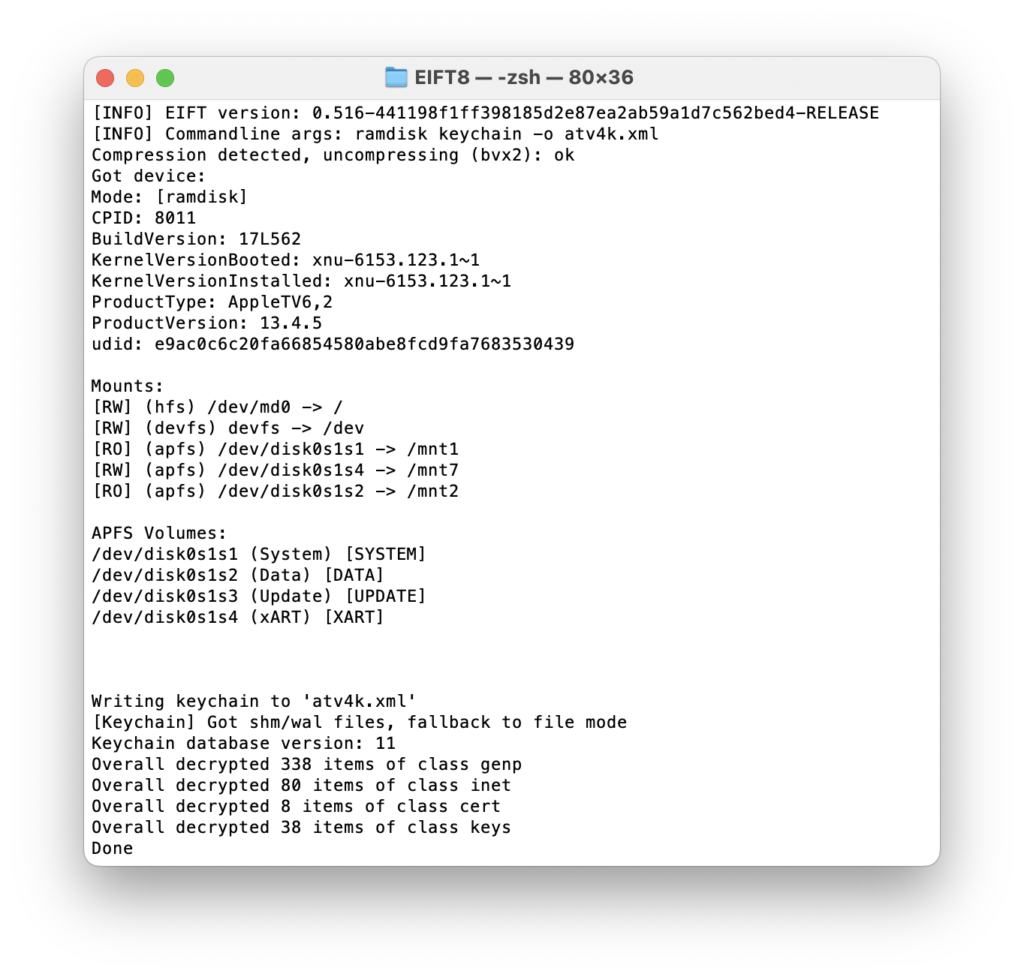
The acquisition steps are basically the same as for iPhones and iPads. Boot our custom ramdisk (you will have to download a proper firmware image using the link provided in our software):
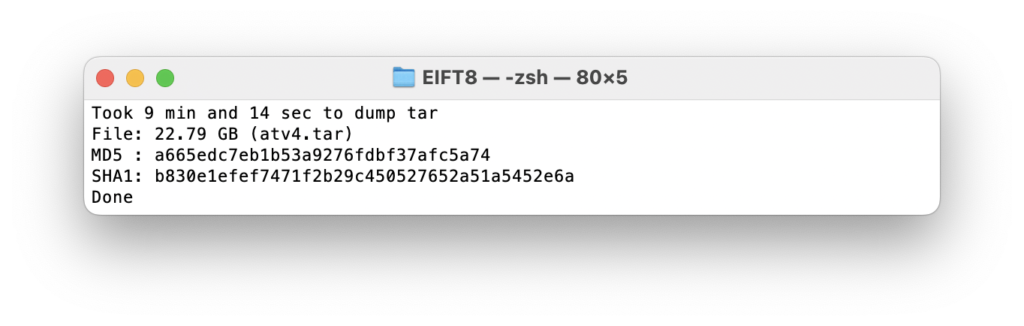
And then pull the keychain (lightning fast) and the file system (at an impressive ~2.5 GB per minute).
 Conclusion
Conclusion
Elcomsoft iOS Forensic Toolkit remains the only software capable of performing a forensically sound keychain and file system extraction from the majority of Apple TV models including the second and third generations, Apple TV HD and Apple TV 4K. If you are working in the field, do not miss the opportunity to get valuable data from this part of Apple ecosystem!
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh