, or how to get to P1–P3 from a slightly different recon
When it comes to recon, especially looking for subdomains, there have been a ton of tools and writeups since the beginning of hacking. But, somehow the least discussed approach is the one that can yield the most amazing results (not always though), and I had only found one tool dealing with it before ffuf existed, but I gave up on it (could be I was doing it wrong, but whatever (: ). I’m talking about vhost discovery using ffuf, which can also be used for regular subdomain discovery with easier to configure against false positives.
FFUF for more than dir bruteforce
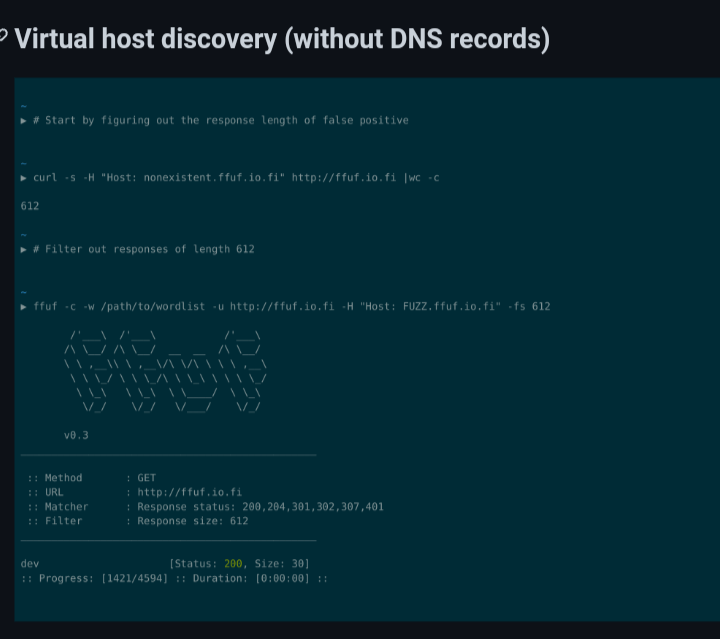
There is a nice piece of seemingly simple way to achieve vhosts scanning using ffuf:

I mean, it’s logically sound… up to a point. The thing that it doesn’t account for is that sometimes there are subdomains/vhosts with 403, 404, 400 that are still interesting to dig deeper into. Using ffuf for file/folder bruteforcing and gau/wayback machine to maybe find some obscure yet interesting endpoints.
Another thing is figuring out whether the size of response means false positive or a redirect to the same destination, etc. That is why you also have to keep an eye on the output and if you notice that the size is the same for multiple subdomains, and also what subdomains are named then you'll have to Ctrl+c or drop into ffuf interactive shell and readjust the -fs flag or maybe even -fw and -fl flags.
For example, maybe host:junkword.target.com has size 123, and you add -fs 123, but then you notice that host:service.target.com and host:services.target.com and host:service1.target.com have the exact same size, words, lines, and response code 403, so clearly you'd want to filter this out because it's very likely some blacklisting on the target in question.
Hunting internal subdomains
I’m gonna jump straight into the most interesting part, and most likely to immediately result in a P1-P3 bug — hunting down some, assumed to be only internally accessible, subdomains that tend to contain sensitive data due to the security through obscurity approach or a misconfiguration.
Here are the scripts (cleaned up versions (: ) that I use on the ffuf output saved as csv. Obviously, feel free to adjust to your needs or merge them, etc.
#!/bin/bash
echo “Usage: ./interesting results-from-ffvhost domain.com"
read -p “Press any key if ready”
cut -d’,’ -f1 $1 | sed s/$/.$2/ | sort -u > foralive2.$1
./alive2 foralive2.$1
alive2:
#!/bin/bash
nmap -iL $1 -sn
The output will show which subdomains can be resolved into ip and which can't. Those that can't are interesting ones, especially if they are 200 OK, but even 404 can yield results.
Hunting for external subdomains
Depending on whether bbp in question is widescope and how the server is configured you may be able to use ffuf as a subfinder type of tool, only much faster and easier to filter out the false positives.
Bypass
OK. The previous two sections have been incredibly useful for me, and I had success with those. But, during one of these recons, I found some interestingly named subdomain and even though it resolved to a regular ip I wanted to see what it had. But, to my surprise even though ffuf got 200 OK response code, curl and Firefox/Chrome got 403.
And then I did the following to confirm that it was quite something:
curl https://domain.com -H host: interesting-sub.domain.com
And got 200 OK and P2 bug.
So, hopefully you can see from this article how ffuf is more of a swiss army knife of bug hunting, much like ncat, but with a different focus (:
This goes well with my article here because it can be done from a android or iPhone:
https://medium.com/@vuk.ivanovic9000/but-hunting-from-a-car-on-a-cheap-mostly-d052397fc9b2
If you want to support my more frequent writing about hunting for bugs which would mean me moving to a country with a cheaper rent sooner please feel free to do so by a whatever tip you can spare, thanks. https://ko-fi.com/bushi1947
如有侵权请联系:admin#unsafe.sh