
Android Exploitation and sudo Exploit

Hello Everyone I am Hac and today we will be doing Router space from Hackthebox it’s an easy retired Linux box in which you have to exploit Android app to get initial foothold on the box and then we will use sudo exploit to escalate your privileges to root user .
Tools we need :
We Will Start With Nmap Scan
There are two port’s open 22 (ssh) and 80 (http) . As Always we will start looking at port 80 . Because it has a larger attack surface .

We can also Download Button “RouterSpace.apk” which looks interesting to me . There are many things we can do with an apk file . In CTF we can use tool like Mobsf to look for “token or creds” or we can use tools like apktool , dex2jar and jadx for manual approach .
Mainly There are two ways / approach for Android app Analysis
1- Static Analysis
2- Dynamic Analysis
We will try both Approach since we don’t know much about the apk . Usually I start with Static Analysis .
But Before that We need to know what the heck is an“apk” . “Apk” is a file format which is used by Android Operating System for distribution of android app . Right now we Need to know that Apk is like a zip file , And Yes we can unzip it by Using tools like “unzip” .
Static Analysis
We can Unzip the file then we can use dex2jar to convert “.dex” file as “.class” file zipped as “jar”


Now we can unzip the “.jar” . And look for Interesting File / Directory like AndroidManifest.xml and smali code . But For Initial foothold we need to Dynamic Analysis So we won’t be going deep into Static Analysis Part .
Dynamic Analysis
I could be tricky if you are doing this for the first time . But trust me it’s easy and remember one thing if you get any error use google . With that said let’s start this part .
We need genymotion as android emulator then we need to configure our burp suite in order to intercept HTTP request . If have made a detailed walk-through of setting your android lab . So go ahead and check that article in order to hack .
Once we are done with our setup , we will open up the android app and click on “Check Status” button .
We Should receive this request if your proxy/setup is done properly .
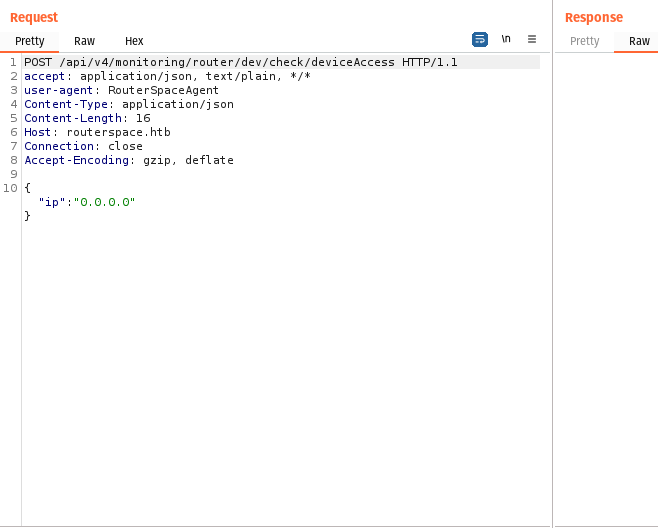
I made some changes and I was able to execute system commands .

Now I tried for revershell but seems like there is something (firewall) which i blocking our request . I did some enumeration and found that we have write access to /home/paul/.ssh . I added my public key into/home/paul/.ssh/authorized_keys

Now I logged in via ssh

Now I ran Linpeas to find out possible ways to get root on this box . I found a root exploit .
sudo-1.8.31 
如有侵权请联系:admin#unsafe.sh