2022-6-29 20:39:14 Author: infosecwriteups.com(查看原文) 阅读量:21 收藏

Content spoofing, also referred to as content injection, “arbitrary text injection” or virtual defacement, is an attack targeting a user made possible by an injection vulnerability in a web application. When an application does not properly handle user-supplied data, an attacker can supply content to a web application, typically via a parameter value, that is reflected back to the user. This presents the user with a modified page under the context of the trusted domain. This attack is typically used as, or in conjunction with, social engineering because the attack is exploiting a code-based vulnerability and a user’s trust. As a side note, this attack is widely misunderstood as a kind of bug that brings no impact.
A content spoofing attack would be to present false information to a user via text manipulation. An attack scenario is demonstrated below.
- An attacker identifies a web application that gives recommendations to its users on whether they should buy or sell a particular stock
- The attacker identifies a vulnerable parameter
- The attacker crafts a malicious link by slightly modifying a valid request
- The link containing the modified request is sent to a user and they clicks the link
- A valid webpage is created using the attackers malicious recommendation and the user believes the recommendation was from the stock website
Valid Page
http://vulnerablesite/suggestions.php?stockid=123&stockrecommendation=We+Recommend+You+Buy+Now
Modified Page
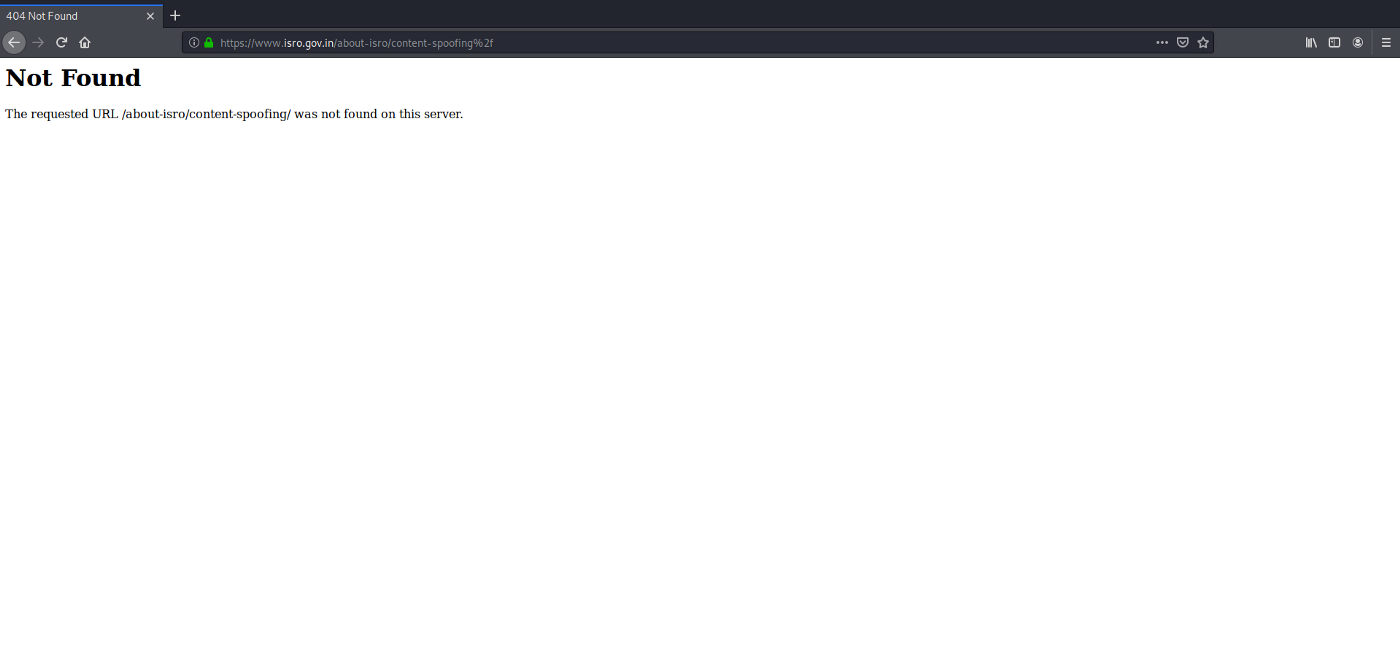
If you research little more to understand why it is happening and what is the issue here. You will get an answer for ‘what is the issue’ that the application is giving a default error page.
For ‘why it is happening’, we know the answer, right?
Anyway, the answer is user input via parameter or directly in the URL is reflected in the page response.
Error Page
URL- https://www.isro.gov.in/

Modified Error Page

This attack is typically used as, or in conjunction with, social engineering because the attack is exploiting a code-based vulnerability and a user’s trust. As a side note, this attack is widely misunderstood as a kind of bug that brings no impact.
The application should only accept the values and types that are defined for parameters and should be checked at the server-side whether there is change content, if there is change, then the application should reject that request. Also, never construct and send messages via URL in the page response. Prefer using messages predefined in a property file.
For Default Error pages
The application configuration should specify a default error page in order to guarantee that the application will never leak error messages to an attacker. Handling standard HTTP error codes is user-friendly in addition to being a good security practice, and can be done by specifying custom error pages for error codes like 404, 403, 500, etc.
From Infosec Writeups: A lot is coming up in the Infosec every day that it’s hard to keep up with. Join our weekly newsletter to get all the latest Infosec trends in the form of 5 articles, 4 Threads, 3 videos, 2 Github Repos and tools, and 1 job alert for FREE! https://weekly.infosecwriteups.com/
如有侵权请联系:admin#unsafe.sh