0x1 fuzzing
看了几篇afdko漏洞分析的文章xinali、project-zero。
了解了afdko一些基础用法,而且afdko核心功能用C写的,如果我要运气好能fuzz出几个漏洞,也搞几个cve岂不美滋滋。
我也试着用afl对afdko进行fuzz。一晚上之后,没有发现crash,倒是有一个hang。

0x2 hang分析
我简单分析了一下hang产生的原因:
函数buildGIDNames, 变量i的类型unsigned short, unsigned short的最大值为65535. 如果numGlyphs比65535大,程序就会一直在此处循环。
1906 static void buildGIDNames(cfrCtx h) {
1907 char *p;
1908 long length;
1909 long numGlyphs = h->glyphs.cnt;
1910 unsigned short i;
1911
1912 if (numGlyphs <= 0)
1913 fatal(h, cfrErrNoGlyph);
1914 dnaSET_CNT(h->post.fmt2.glyphNameIndex, numGlyphs);
1915 for (i = 0; i < numGlyphs; i++) {
1916 h->post.fmt2.glyphNameIndex.array[i] = i;
1917 }例如
0x0000555555604929 in buildGIDNames (h=0x62a000000200) at /home/test/github/afdko/c/public/lib/source/cffread/cffread.c:1916
1916 h->post.fmt2.glyphNameIndex.array[i] = i;
gdb-peda$ p /d numGlyphs
$5 = 66950
gdb-peda$ p /d i
$6 = 114990x3 漏洞修复
我把漏洞报送给[email protected],很快漏洞就修复了。根据邮件回复,看起来这种问题只能算bug,不算security bug,就算我fuzz到afdko内存破坏类漏洞,Adobe也不为AFDKO申请CVE。

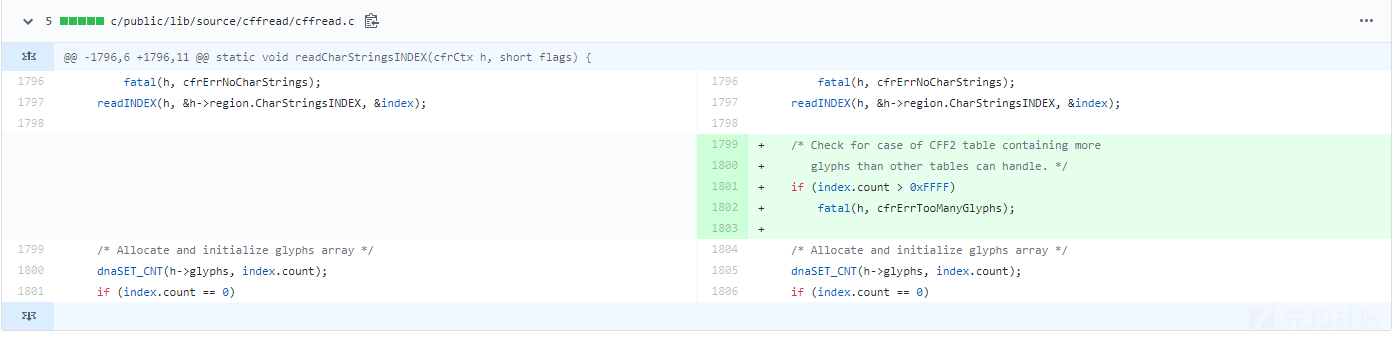
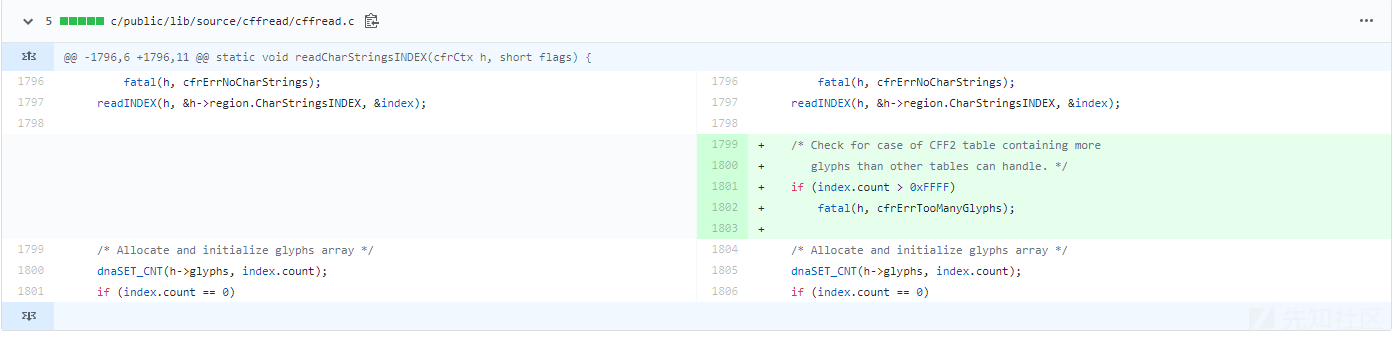
github修复commit
https://github.com/adobe-type-tools/afdko/commit/e4c023d4b31515d7f8d0a73b2326d3a043e8668c
截图
回过头重新看project-zero的文章。
0x4 回头重看利用
两个CVE cve-2019-8017、cve-2019-1117 。两个产品。
1、cve-2019-8017
Adobe Acrobat的漏洞
For example, it is possible to execute the AFDKO copy in CoolType.dll by opening a PDF file with an embedded font, and exporting it to a PostScript (.ps) or Encapsulated PostScript (.eps) document
The proof of concept is a PDF file with an embedded Type 1 font, which includes an extra "/FDArray 0" operator to set the length of FDArray to 0, as described above.
When the poc.pdf file is opened with Adobe Acrobat Pro and converted to a PostScript document via "File > Export To > (Encapsulated) PostScript", the following crash occurs in Acrobat.exe:
简单理解
Adobe Acrobat Pro打开构造的pdf文件,导出成PostScript,Adobe Acrobat崩溃。2、cve-2019-1117
Microsoft DirectWrite的漏洞
Microsoft's DirectWrite library includes parts of AFDKO。
One example of a client application which uses Direct2D printing is Microsoft Edge. If a user opens a specially crafted website with an embedded OpenType variable font and decides to print it (to PDF, XPS, or another physical or virtual printer), the AFDKO code will execute with the attacker's font file as input.
简单理解
Microsoft Edge 支持Direct2D printing.Microsoft Edge打开嵌入了OpenType字体的网页,然后打印网页成PDF、 XPS,AFDKO就会运行嵌入的字体。poc.html
<html>
<head>
<style>
@font-face { font-family: custom_font; font-weight: 1000; src: url('poc.otf'); }
h1 {
font-family: custom_font
}
</style>
</head>
<body>
<h1>The quick brown fox jumps over the lazy dog.</h1>
</body>
</html>我按照上面的方式进行试验,没有发现任何异常,对afdko的应用理解还不是很深入,无法完成利用。。。。。。。
最后能利用的洞才是好洞。。。。
文章来源: http://xz.aliyun.com/t/6334
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh