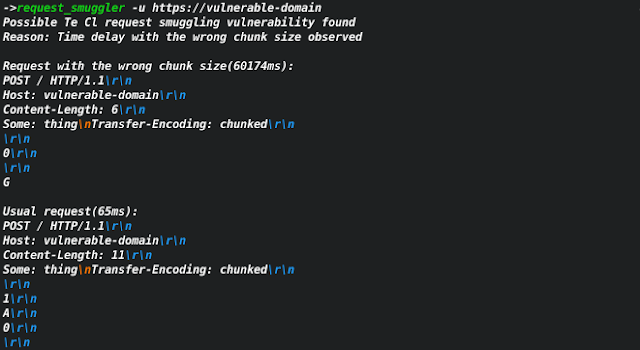
Based on the amazing research by James Kettle. The tool can help to find servers that may be vulnerable to request smuggling vulnerability.
Usage
USAGE:
request_smuggler [OPTIONS] --url <url>FLAGS:
-h, --help Prints help information
-V, --version Prints version information
OPTIONS:
--amount-of-payloads <amount-of-payloads> low/medium/all [default: low]
-t, --attack-types <attack-types>
[ClTeMethod, ClTePath, ClTeTime, TeClMethod, TeClPath, TeClTime] [default: "ClTeTime" "TeClTime"]
--file <file>
send request from a file
you need to explicitly pass \r\n at the end of the lines
-H, --header <headers> Example: -H 'one:one' 'two:two'
-X, --method <method> [default: POST]
-u, --url <url>
-v, --verbose <verbose>
0 - print dete cted cases and errors only,
1 - print first line of server responses
2 - print requests [default: 0]
--verify <verify> how many times verify the vulnerability [default: 2]
Installation
-
Linux
- from releases
- from source code (rust should be installed)
git clone https://github.com/Sh1Yo/request_smuggler
cd request_smuggler
cargo build --release - using cargo install
cargo install request_smuggler --version 0.1.0-alpha.2
-
Mac
- from source code (rust should be installed)
git clone https://github.com/Sh1Yo/request_smuggler
cd request_smuggler
cargo build --release - using cargo install
cargo install request_smuggler --version 0.1.0-alpha.2
- from source code (rust should be installed)
-
Windows
- from releases