
2022-3-16 15:4:19 Author: infosecwriteups.com(查看原文) 阅读量:77 收藏
Reported and Fixed | Bounty Rejected Indirectly.
To know more about me, Ask google assistant “Who is Krishnadev P Melevila” Or search for my name on google.
Let’s get started!!

Vulnerability: OTP Bypass And and Account takeover
Impact: Zero Day
Risks: Patient Sensitive Data
Priority: P0
Scope: Medical Records, Scan reports, Test reports, Other patient sensitive information
Steps to reproduce in attackers point of view:
- Visit https://patientportal.rajagirihospital.com/
- Click on Forgot/New User
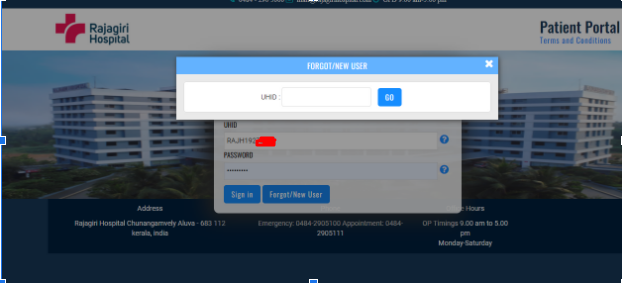
3. Enter any valid UHID for testing I used RAJH192*****

4. It requires the last 4 digits of the mobile number to get OTP. An attacker can also bypass this using response manipulation that Will uses in the coming steps. But here I am going to retrieve the patient’s Mobile number through another method.
5. For that visit https://patientportal.rajagirihospital.com/consumablebilling/consumablebilling and enter the UHID and click ‘GO’and intercept that request on web interception tools like burpsuite

6. After response interception of above request (Intercept every request related to above step), we get a response as below mentioned:
HTTP/1.1 200 OK
Cache-Control: private
Content-Type: text/html; charset=utf-8
Server: Microsoft-IIS/8.5
X-AspNetMvc-Version: 5.2
X-AspNet-Version: 4.0.30319
X-Powered-By: ASP.NET
Date: Tue, 15 Mar 2022 02:45:40 GMT
Connection: close
Content-Length: 125[{"Pcellno":"9447******","PPhone":"","PEMail":"","HSPLocationId":7,"patientNm":"Mr.VARGHESE .","sex":1,"age":63,"Agetype":1}]
7. Here his phone number is clearly mentioned (Here I hide ‘PCellno’ on this writeup because of security issues, But on the actual attack, it is completely visible.), so we can go back to step 3 and enter the last 4 digits.

8. After mobile verification, we will get an interface to enter OTP like below:

9. Here enter any random number like ‘1234’ and intercept the response of that request

HTTP/1.1 200 OK
Cache-Control: private
Content-Type: text/html; charset=utf-8
Server: Microsoft-IIS/8.5
X-AspNetMvc-Version: 5.2
X-AspNet-Version: 4.0.30319
X-Powered-By: ASP.NET
Date: Tue, 15 Mar 2022 02:51:06 GMT
Connection: close
Content-Length: 10
10. Here during the interception of the response, we get a number at the end as ‘0’ , change that to ‘1’ and forward the response to the client. And you will get access to change password.
11. Now set a new password and login directly from the login portal with UHID and password that we set now.


EXTRA: The phone number enumeration is not actually required ( that is step 5 to 6 can be avoided). We can use the same response manipulation technique used in step 9 to bypass mobile verification.
Response from Rajagiri IT team: When I asked that did they provide any bounty for my work, They replied that, They are afraid to report it to the management team as they don’t know how the management team reacts to this report.
Action made by Rajagiri IT Team: Site is closed now and they are on the fix.
So that’s all guys,
Don’t forget to follow me on medium and other social media. Also please give your 50 claps for this write-up and that’s my inspiration to write more!!
My Instagram handle: https://instagram.com/krishnadev_p_melevila
My Twitter handle: https://twitter.com/Krishnadev_P_M
My LinkedIn handle: https://www.linkedin.com/in/krishnadevpmelevila/
My Personnel website: http://krishnadevpmelevila.com/
如有侵权请联系:admin#unsafe.sh