

A task was assigned to me: hack the phonebook.company.net
so, I started the hacking engine of my mind…
When doing pentest, I always go for the highest impact.
BUT the highest impact will be defined differently based on the business model of the target.
Let me explain.
Let’s say the target is a news website. validity and integrity of the data is the core business model of the target.
so, a bug that enables an attacker to modify the content of the website has a significant impact and destroys the company’s reputation.
for example, consider stored XSS, this bug usually gets ranked as high impact but, in this scenario, it is a critical one.
My target provided technical support to other companies and their team needed to contact the customers in the shortest time possible.
the customer’s contact info was stored in an internal server: phonebook.company.net
So, what is the highest impact here? if you make the phonebook server out of service, the company’s business comes to a halt suddenly and…
gets destroyed, business is merciless.
Part One: DoS It
I started using the web application to understand its workflow.
Let me describe the application.
there were three different access levels:
user: modifying its own contact info
employee: modifying its own contact info, searching contact info
admin: modifying all users’ contact info, searching contact info
The app had three sections:
1. Search page
2. user profile
3. administration section
My test account had user privileges and I could add my own contact info.
the body of the PUT request which modified the user data was like this:
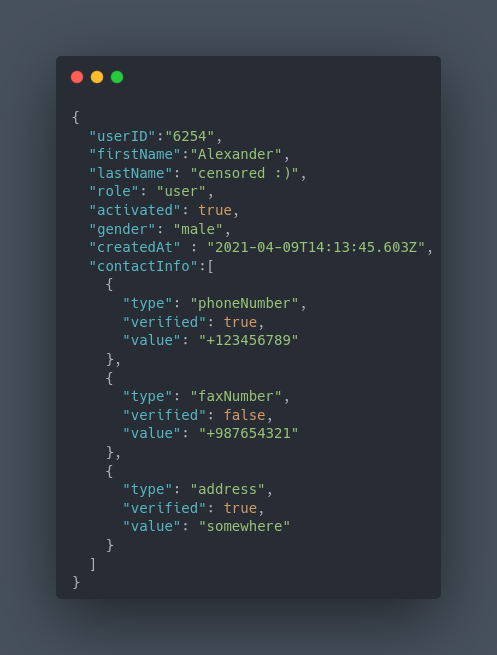
using the GUI, there was a limitation for adding contact info. I could only add up to five records to my contact info section. so, I modified my details, intercepted the request, manually added three more records to the contactInfo array, and sent the request.
the server just simply accepted it and now there were 8 records on my profile page.
ok, but can this simple behavior be useful?
of course, because when I can bypass the client-side limitation and add three more records, it means I can…
add unlimited records to the back-end database,
use up the server’s storage,
increase the time of search processes containing my profile in their results,
increase the amount of RAM storage needed to process my profile.
sounds like a DoS, isn’t it? 🙂
the server running the phonebook app wasn’t that powerful, just a normal machine for handling the internal teams’ requests. so I could confirm the vulnerability faster and with no need to add a lot of records to my profile.
I added a couple of thousand records and the server's response time increased dramatically when I searched for my name. and by adding a few thousand more it didn’t respond even after one minute.
DoS confirmed. 📛
Part Two: DoS It More…
as I mentioned the DoS happened when I searched for my name, but when I searched for someone else’s name the server responded fast.
here’s what I mean:
al… alex… alexan… alexande… alexander…
— the server didn’t respond for any step
but when I searched for my colleague’s name:
Mi… Mich… Michael…
— the server responded fast for every step
which means, the DoS happens only when my account is in the search results.
in other words, employees can’t use the server to look up customers whose name has the same starting letters as mine. that has a limited impact and I don’t want it.
So… let’s DoS it more 😏
I need to do some magic that my account be in the results of any search.
as always, the question is “HOW?”
there was a feature implemented in the search page to make searching easier for employees, so I used that to make searching harder for them 🙃
when you type something in the search box, the application searches in the customer names and also the value of their contact info records — some kind of reverse search:

what a nice feature, thanks dev team :)
so I wrote a small script to generate random combinations of letters and numbers and add them as the value of my contact info. this way, it doesn’t matter what employees search for, my account will be in the results and…
Server Down 💀
Part Three: Not Enough, Go For More!!
what if it was not possible to DoS the server with the straightforward way of just adding more records?
PRO TIP:
learn the JSON structure well.
when you come across JSON data try to change the type of “value”s.
if it’s integer turn it into string, there may be an SQLi.
if it’s a string containing a security token, replace it with null, you maybe find an authentication bypass.
if it's a string containing an OTP turn it into an array, you may be able to brute-force all the possible codes at once.
I used the last trick, but not to brute-force anything, to add data more than normal:

I sent the request and the server accepted it. that means I can add unlimited elements to the array and use up storage and RAM as much as I want.
the same story as before, another DoS :)
this way it is possible to DoS the server even if I don’t be able to add more than five records.
Part Four: Eliminating Your Opponent, Only 49.99$
how can an attacker exploit it while this is an internal server and only employees have access to it?
as I mentioned before, there were three access levels:
user
employee
administrator
employees and admins could directly log in to the server but there was a reverse proxy between accounts with user access level and the server. because the user accounts belonged to customers and their requests to add and modify their contact info were served by an API.
so here’s the attack scenario:
imagine you’re a company competing for the market with my target company. you go to their website, act like someone who wants to support their business, and buy their cheapest service for 49.99$. then you go to your profile and add thousands of contact info records…
because you want to make sure they can get in touch with you if necessary 😏
…and, they lost the market, RIP.
was it helpful?
I don’t ask you to buy me a cup of coffee,
teach me something…
Discord: REDN#9702
如有侵权请联系:admin#unsafe.sh