Here summarized are the main news of this release of Cerbero Suite 5.4 and Cerbero Engine 2.4.
.NET ReadyToRun Format Support
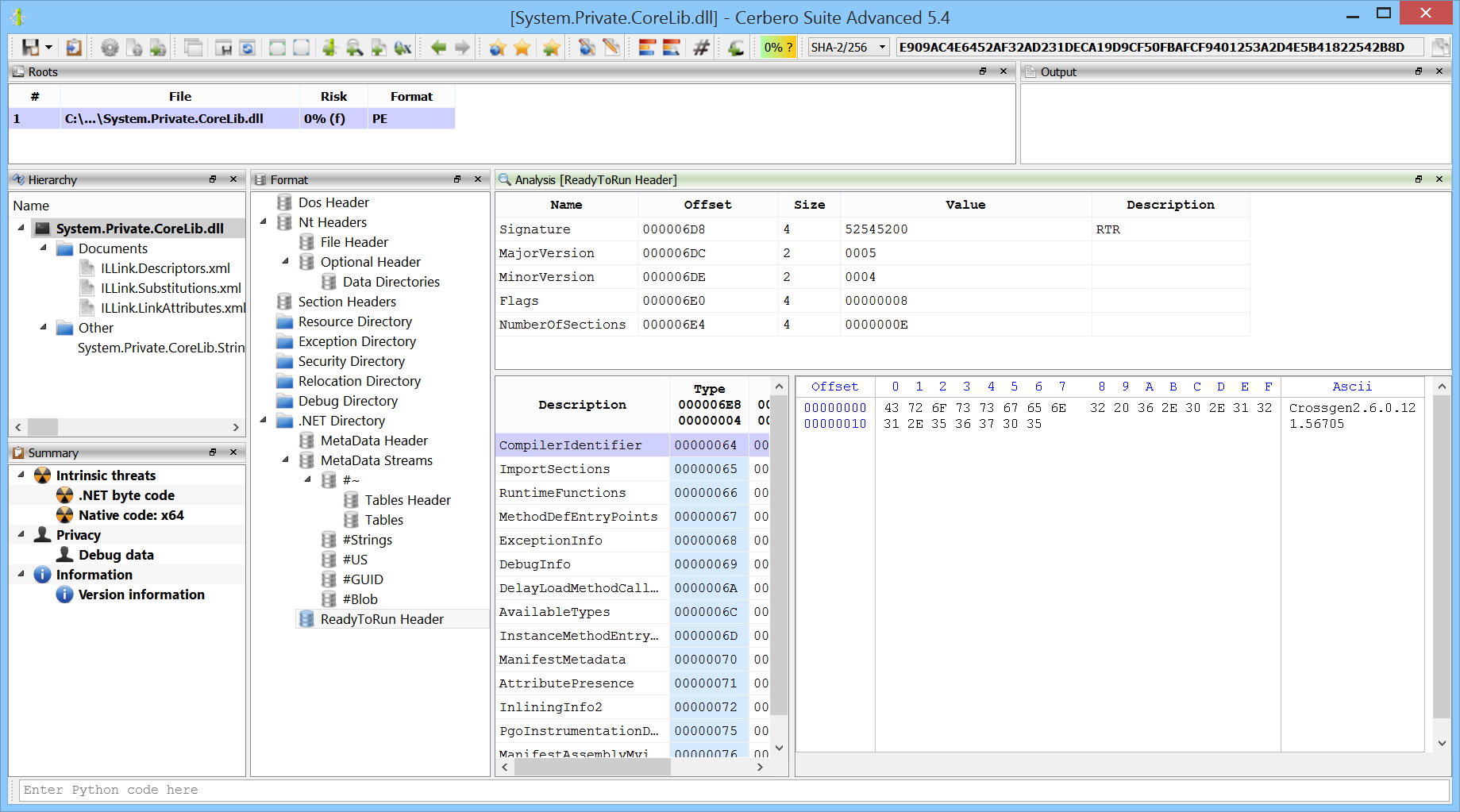
Thanks to one of our customers who reported it to us we have introduced support for the .NET ReadyToRun format.
We already support NGen generated native images and our support for the ReadyToRun format makes sure that it is not mistaken for an NGen generated image.
Hex Editing Processes on Linux
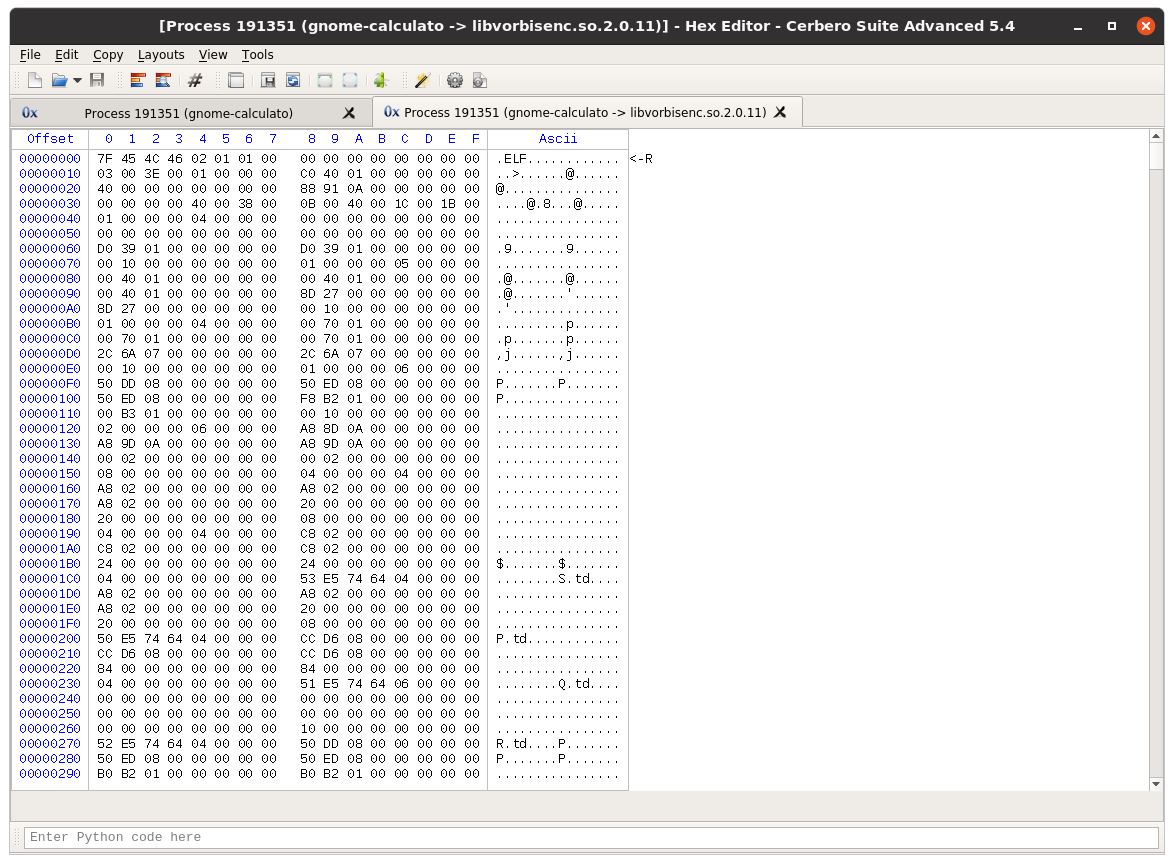
This release of Cerbero Suite introduces the capability to open processes in the hex editor on Linux. Windows has already supported this feature since the introduction of our hex workspace.
You can read more about the topic in our dedicated post.
We have also exposed our process API in the Core module to Python and documented it.
API Solver Package
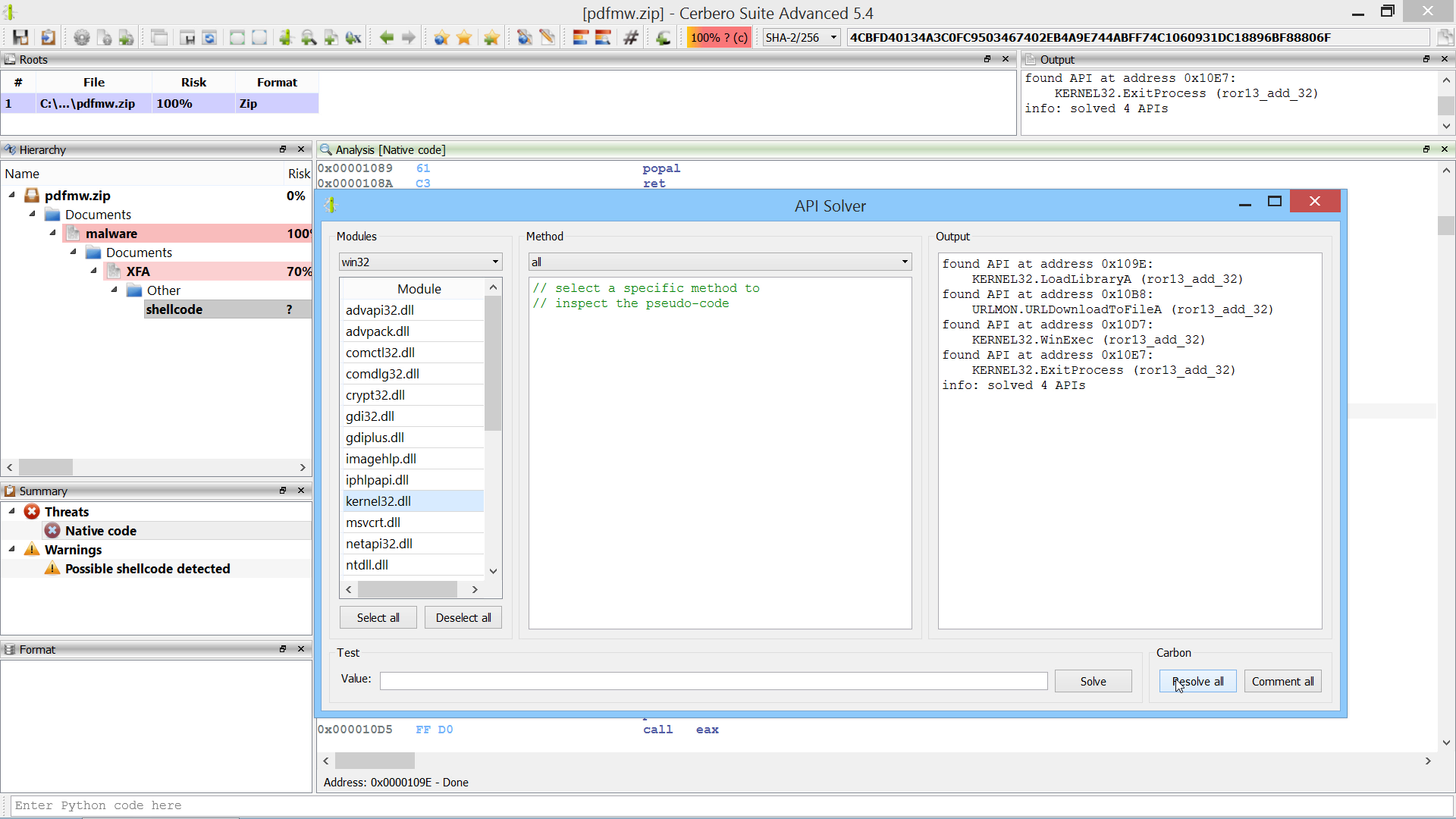
We have released our API Solver package on Cerbero Store for all commercial licenses of Cerbero Suite Advanced. This package is especially useful when analyzing shellcode.
You can read more about the topic in our dedicated post.
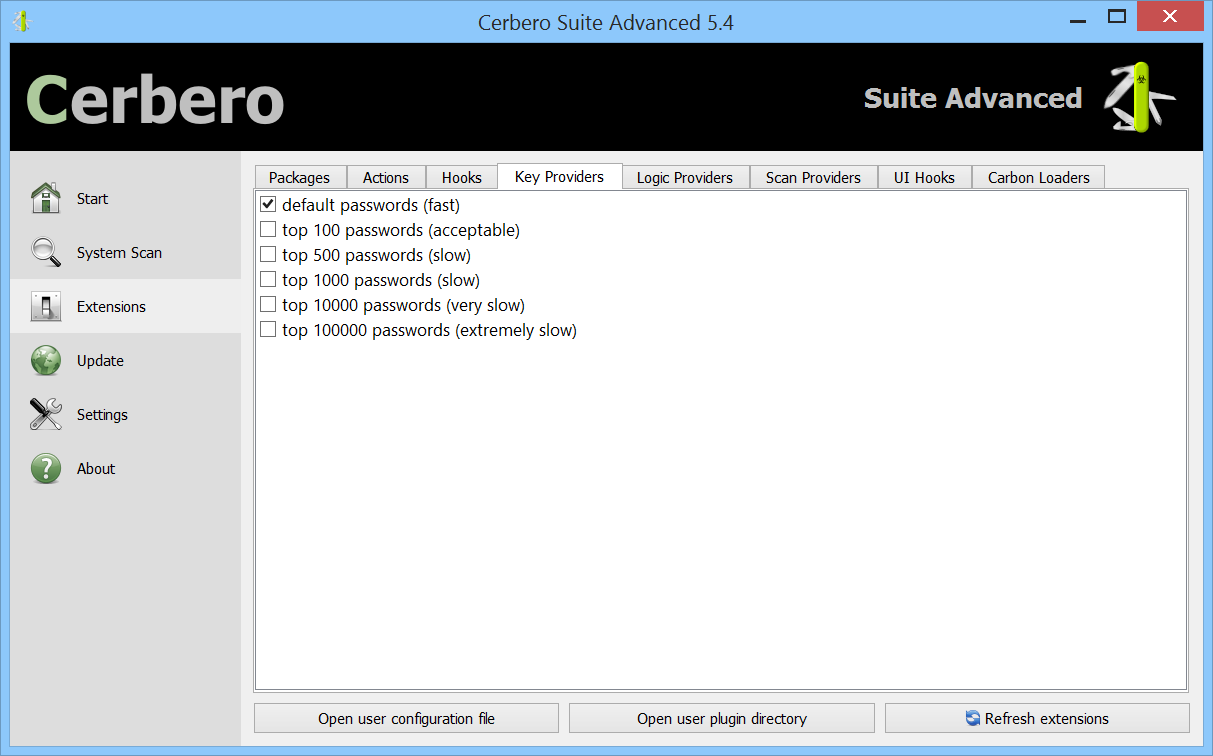
Common Passwords Package
We moved our built-in password brute-forcers to an external package on Cerbero Store called “Common Passwords”. Cerbero Suite Advanced (both commercial and non-commercial) and Cerbero Engine have access to the package.
You can read more about the topic in our dedicated post.
Silicon Spreadsheet Documentation
We have fully documented our Excel macro emulator and spreadsheet visualization module.
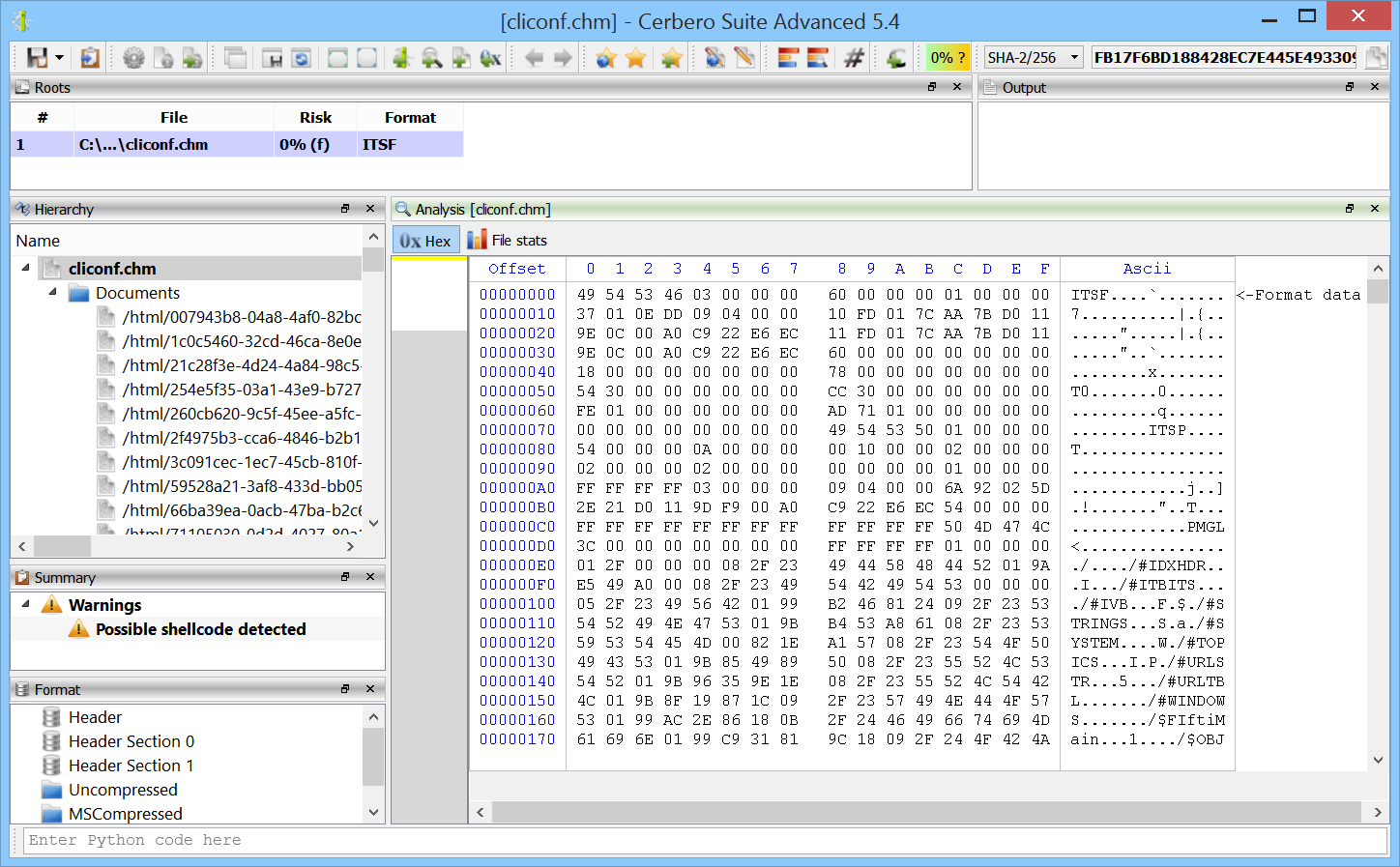
Improved ITSF (CHM) Format Support
We have improved our support for Microsoft’s ITSF (also known as CHM) format and we have exposed the format to our Python SDK.
You can read more about the topic in our dedicated post.
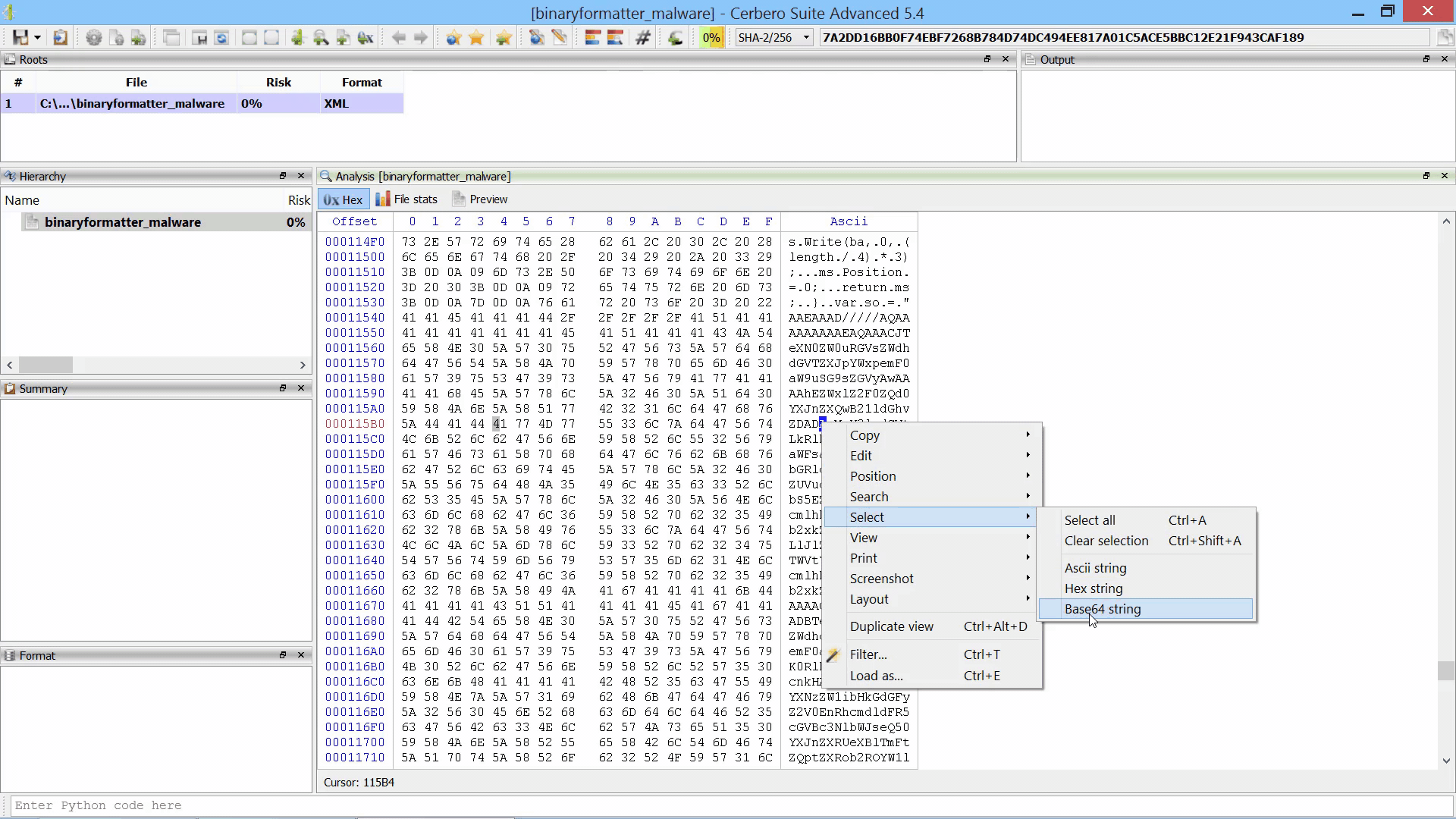
Improved Hex Editor
We made it very easy to select contiguous ASCII, Hex and Base64 strings in the hex editor. This comes very handy when loading embedded files or decoding data.
We have also made other minor improvements and fixed a few bugs.