February 20, 2022 in Frida, Malware Analysis 2022-2-21 03:14:44 Author: www.hexacorn.com(查看原文) 阅读量:62 收藏
![]()
February 20, 2022 in Frida, Malware Analysis
In part 1 and part 2 we looked at individual APIs and I hinted we can automate generation of handlers. Today we will do exactly that.
The attached python code (delphi.py) reads PE file and then searches for code patterns that represent a couple of popular Delphi API functions responsible for string operations.
For every occurrence found, we generate a handler & print out the offsets (first offset is file position, and the second number is RVA that we need to pass to frida-trace):
Once handlers are generated, we can run frida-trace:
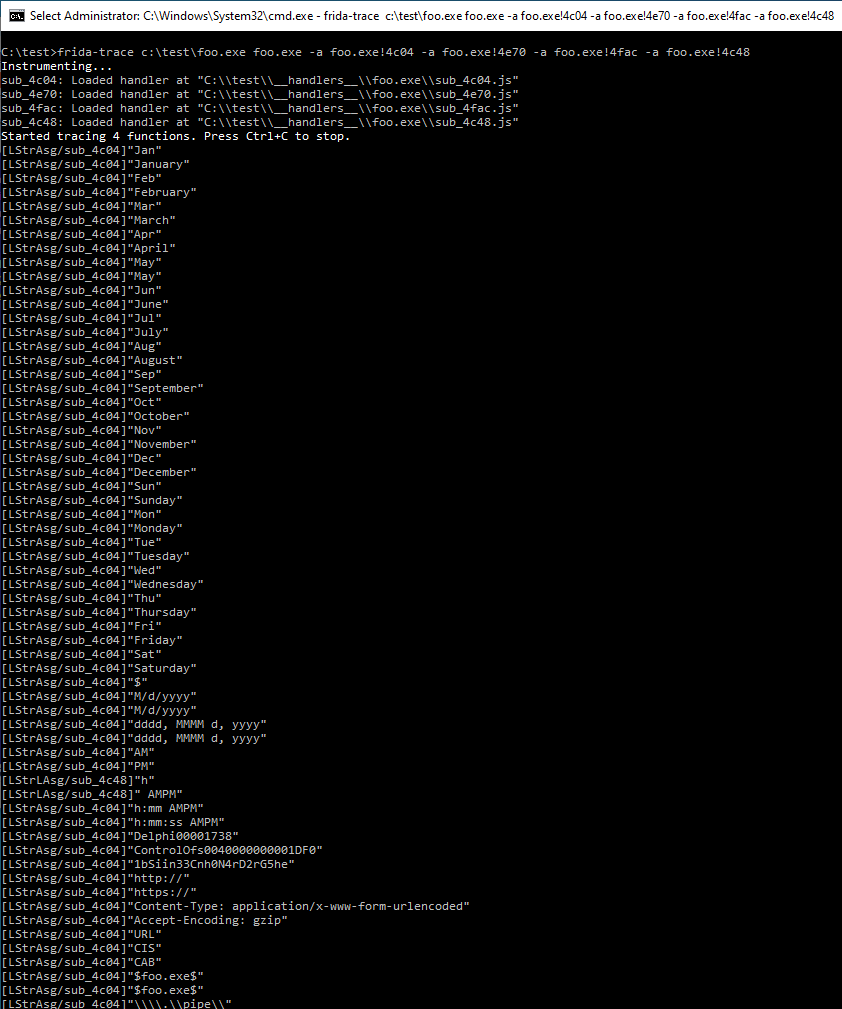
frida-trace c:\test\foo.exe foo.exe -a foo.exe!4c04 -a foo.exe!4e70 -a foo.exe!4fac -a foo.exe!4c48
This is a full log. Lots of string goodness, right? Note the IOCs, and the fact processes seem to be enumerated in order to find if possibly targeted processes are present.
And in case you are wondering the sample in question (foo.exe) is 00008EB74EEAEFFC64E85F8B0978D4EB056FCF390264A0D4C7D4A15ED5356DD3.
如有侵权请联系:admin#unsafe.sh

