Do you have to know which SoC a certain Apple devic 2022-2-11 15:10:8 Author: blog.elcomsoft.com(查看原文) 阅读量:32 收藏
Do you have to know which SoC a certain Apple device is based on? If you are working in mobile forensics, the answer is positive. Along with the version of iOS/watchOS/iPadOS, the SoC is one of the deciding factors that affects the data extraction paths available in each case. Read this article to better understand your options for each generation of Apple platforms.
It’s been more than a year since we compiled essential information on Apple mobile devices into a single easy-to-use table; see Apple Mobile Devices Cheat Sheet. There have been several updates since then, and we added more information on the available acquisition methods.
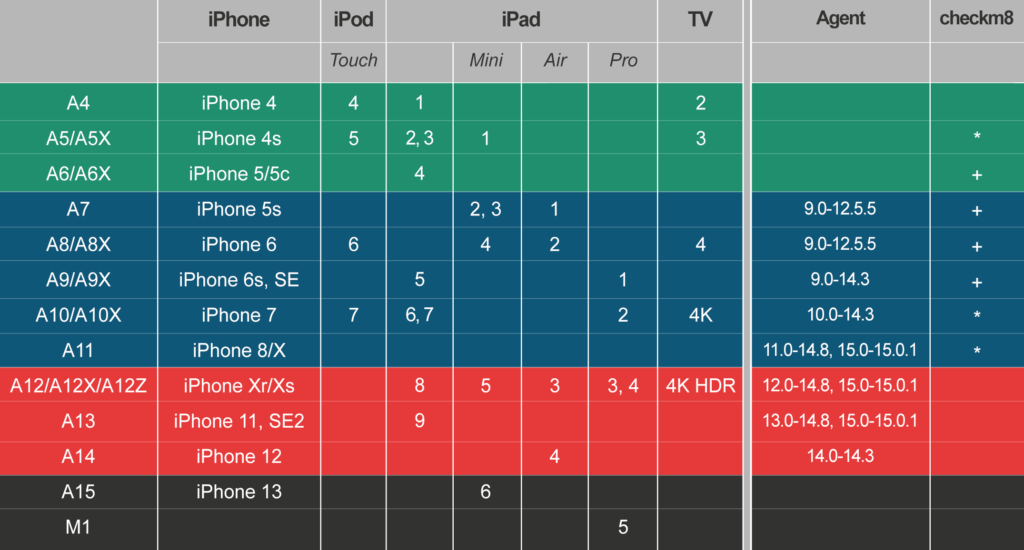
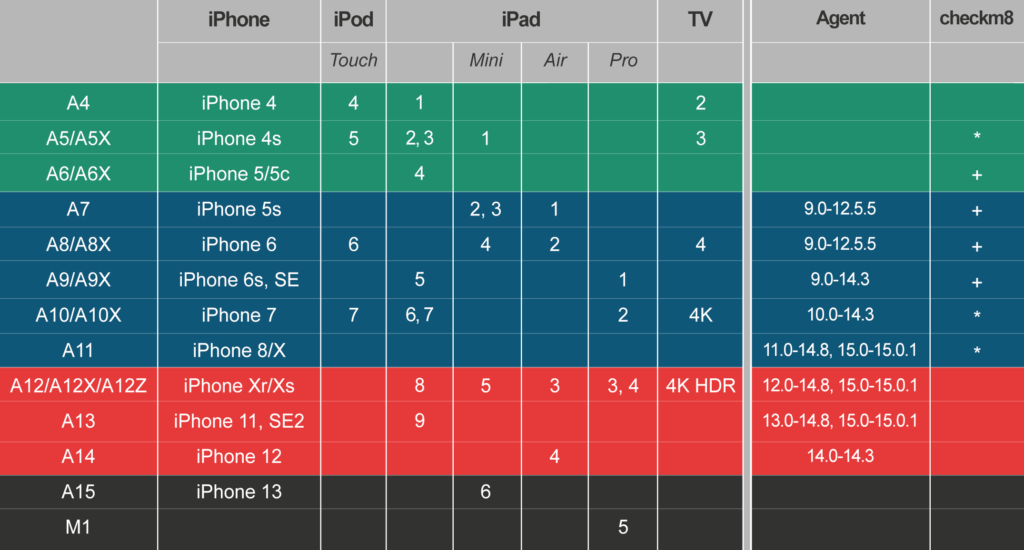
We covered the possible acquisition scenarios in iPhone Acquisition Methods Compared, but that article is slightly outdated too. The compatibility matrix currently looks as follows:
What do the colors mean?
- Green: you can do almost everything, including passcode cracking.
- Blue: devices vulnerable to the checkm8 exploit. It means that BFU (Before First Unlock) is possible regardless of iOS version. For unlocked devices acquisition options are wide enough.
- Red: you cannot extract a locked device. For unlocked devices, keychain and file system image can be extracted for the listed iOS versions.
- Black: only logical and iCloud acquisition methods are available for now.
checkm8 acquisition is something very special. Our tools support it for iPhones up to and including the iPhone X. At this time, the following devices are not supported even if their SoC has the bootloader vulnerability exploited by checkm8:
- iPhone 4s. Despite the age of this device, it’s really hard to work with; a reliable checkm8 implementation exists for Arduino only.
- iPads (all models). Noted the ‘X’ in SoC names? Processors like A12X and A12Z are not really different from A12, yet the checkm8 implementation needs some changes. It may or may not work, but no official support.
- Apple TV. The 3rd model is similar to the iPhone 4s, which is really troublesome (see above); there are some issues with the newer 4 and 4K models as well. The 2021 model is not supported.
On the other side, we do support the Apple Watch Series 3. It does not appear in the table, yet the S3 model is compatible with the checkm8 exploit, and we can extract the keychain and the file system for all watchOS versions. To make it easier, here is the full list of devices with checkm8 support (in fact, iPhone 4 is handled with another bootloader exploit):
- iPhone 4 (iPhone3,1/iPhone3,2/iPhone3,3): A1332, A1349
- iPhone 5 (iPhone5,1): A1428, A1429, A1428
- iPhone 5c (iPhone5,4): A1507, A1526, A1529, A1516
- iPhone 5S (iPhone6,1/iPhone6,2): A1453, A1533, A1457, A1518, A1528, A1530
- iPhone 6 (iPhone7,2): A1549, A1586, A1589
- iPhone 6 Plus (iPhone7,1): A1522, A1524, A1593
- iPhone 6s (iPhone8,1): A1633, A1688, A1691, A1700
- iPhone 6s Plus (iPhone8,2): A1634, A1687, A1690, A1699
- iPhone SE (iPhone8,4): A1662, A1723, A1724
- iPhone 7 (iPhone9,1/iPhone9,3): A1660, A1778, A1779, A1780, A1853, A1866
- iPhone 7 Plus (iPhone9,2/iPhone9,4): A1661, A1784, A1785, A1786
- iPhone 8 (iPhone10,1/iPhone10,4): A1863, A1905, A1906, A1907
- iPhone 8 Plus (iPhone10,2/iPhone10,5): A1864, A1897, A1898, A1899
- iPhone X (iPhone10,3/iPhone10,6): A1865, A1901, A1902, A1903
- iPod touch 6th gen (iPod7,1): A1574
- AppleTV 3 (AppleTV3,2): A1469
- Apple Watch S3 (Watch3,1, Watch3,2, Watch3,3, Watch3,4 ): A1858, A1859, A1860, A1861, A1889, A1890, A1891, A189
Agent acquisition is 100% compatible with all iPod models “corresponding” to the iPhones.
As for the iOS versions, there are some notes too:
- checkm8 works on many devices up to and including the iPhone X, but for iPhone 7, iPhone 8 and iPhone X running iOS 14 and 15 you will need to remove the passcode prior to acquisition. It is sometimes troublesome, and has some consequences, see How to Remove The iPhone Passcode You Cannot Remove for details.
- One of the exploits we use only support devices based on the A11-A13 SoC only.
- For A12 and A13 devices running iOS 14.5+, we cannot decrypt the keychain (only the file system is extracted).
- We do support iOS 15.0 and 15.0.1 on A11-A13 with the agent, as well as iOS 14.8 and lower, but we do NOT support iOS 14.8.1 (the latest available iOS 14 version).
Sounds confusing? With the number of models and OS versions, it is virtually impossible to provide a straightforward roadmap, step by step instructions, or implement a single push button solution.
The software
“We have a tool for that!” For everything low-level, including agent-based and checkm8-based extractions, use Elcomsoft iOS Forensic Toolkit. Note that you’ll need the Mac edition of the tool for checkm8 extractions. Also use the Toolkit for advanced logical extractions as well as file system imaging with jailbreaks. Finally, if you have a legacy 32-bit iPhone protected with an unknown passcode, Elcomsoft iOS Forensic Toolkit is the tool to use to unlock the device.
Use Elcomsoft Phone Breaker for everything cloud related. Cloud backups, iCloud Photos, synchronized data, iCloud Keychain and other end-to-end encrypted data can be extracted with this tool. We are constantly working to keep it up to date with the latest changes in Apple’s communication and encryption protocols.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
![]()
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
如有侵权请联系:admin#unsafe.sh