iOS Forensic Toolkit 7.10 brings low-level file sys 2022-1-13 16:55:40 Author: blog.elcomsoft.com(查看原文) 阅读量:41 收藏
iOS Forensic Toolkit 7.10 brings low-level file system extraction support for a bunch of iOS versions. This includes the entire range of iPhone models based on the A11, A12, and A13 Bionic platforms running iOS 14.4 through 14.8.
Before this update, iOS Forensic Toolkit could perform low-level extraction of all iPhone models running iOS 9 through iOS 14.3 in a truly gapless fashion. With this update, we made it possible to perform full file system and keychain extraction of iOS 14.4-14.8 for select iPhone models.
Benefits of agent-based extraction
There are several extraction methods of varying quality and applicability. Logical acquisition is the most used method, being the most universal and compatible. In many cases, logical acquisition delivers just enough evidence. However, low-level extraction offers tangible extras such as location data, comprehensive device usage stats, as well as all sandboxed app data including the working sets of secure messaging apps (along with decryption keys, if required).
Low-level extraction can be implemented in several vastly different ways. For older devices, the checkm8 extraction delivers the best results; our solution is unrivaled in providing truly forensically sound results (see Forensically Sound checkm8 Based Extraction of iPhone 5s, 6, 6s and SE and Checkm8 Based Extraction of iPhone 7 and iPhone 7 Plus), with support up to the latest iOS 15.2.
This method is not applicable to newer devices. To deliver low-level extraction for the rest of Apple hardware, we developed an in-house extraction agent that comes as close to being forensically sound as possible. This method is highly dependent on kernel exploits, which are extremely difficult to implement. This is why low-level extraction almost never comes to the current, up-to-date and fully patched versions of iOS. For newer models starting with iPhone Xr/Xs, using the extraction agent is the only way to extract the file system and decrypt the keychain.
What is the extraction agent?
When extracting an iOS device, we still need low-level access to the device. For this, we developed our own solution based on the extraction agent, which is an app sideloaded to the iPhone. The extraction agent establishes a communication channel between the device and the computer, escalates privileges, and gains access to the file and the encryption keys required to decrypt the content of the keychain.
In earlier versions of iOS Forensic Toolkit, we supported iOS versions up to and including iOS 14.3. Today, we are extending support all the way up to iOS 14.8. This includes the complete support (file system and keychain) for iPhone 8, 8 Plus and iPhone X devices.
For iPhone Xr, Xs, Xs Max, iPhone SE (2nd gen) and the entire range of iPhone 11 devices, the complete support is only possible for iOS versions prior to iOS 14.5. For newer iOS builds (up to and including iOS 14.8) on these platforms only the file system is extracted, but we are working on keychain extraction too.
Using the extraction agent
You’ll need a supported iPhone or iPad device running a compatible version of iOS. Please refer to the following picture for the matrix of supported device models and iOS versions:
Using an Apple ID registered in Apple’s Developer Program is strongly recommended for installing the agent as it alleviates the need to open Internet access on the device. More about that in Why Mobile Forensic Specialists Need a Developer Account with Apple [article]. A workaround is available to Mac users.
Steps to extract the file system and decrypt the keychain
To extract the file system and decrypt the keychain from an iOS device without a jailbreak, follow these steps.
- Connect the iPhone to your computer. Pair the device (establish trusted relationship) by confirming the prompt on the iPhone and entering the screen lock passcode.
- Launch iOS Forensic Toolkit 7.10 or newer.
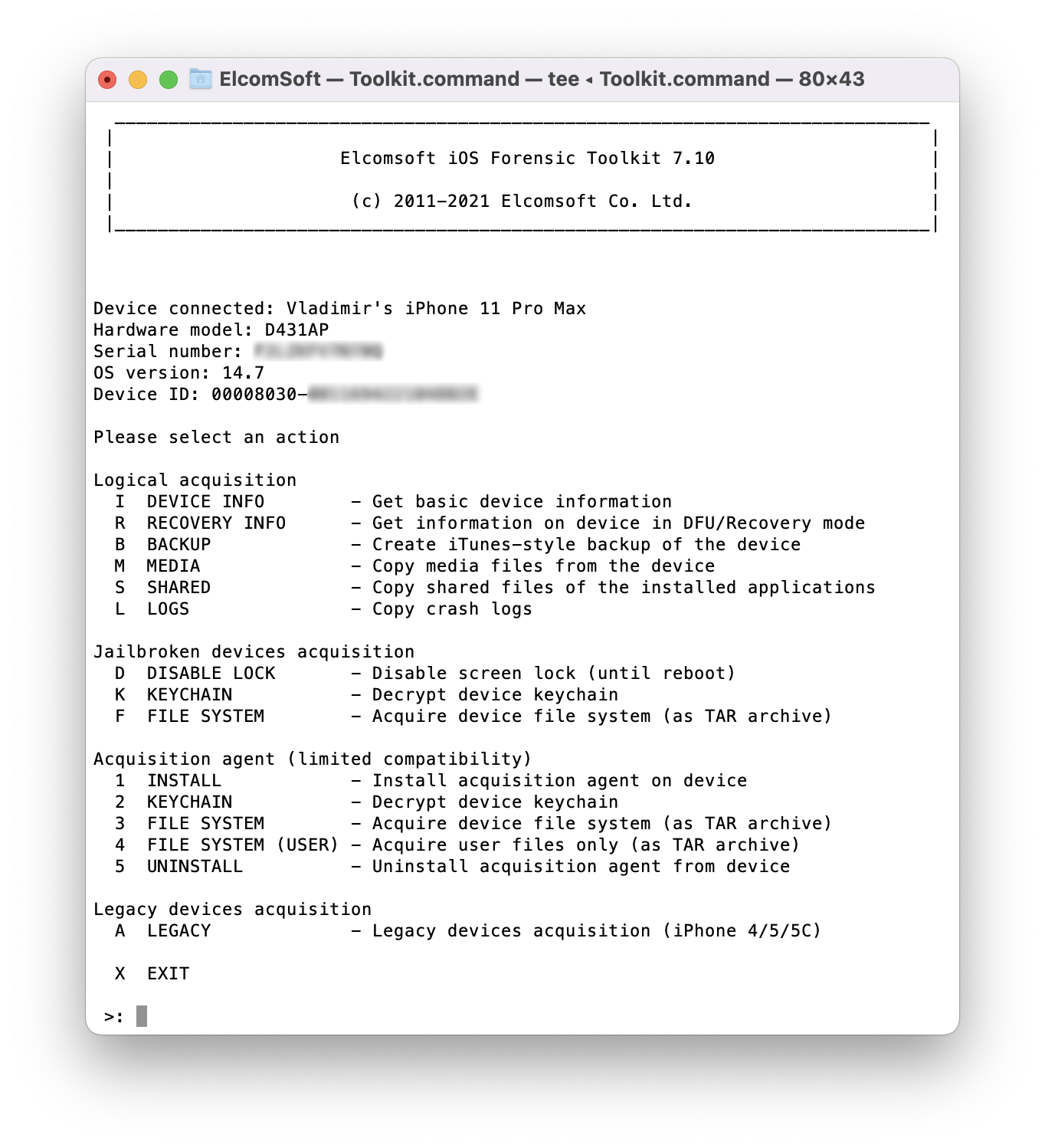
- On the computer, sideload the extraction agent by using the corresponding command in iOS Forensic Toolkit.
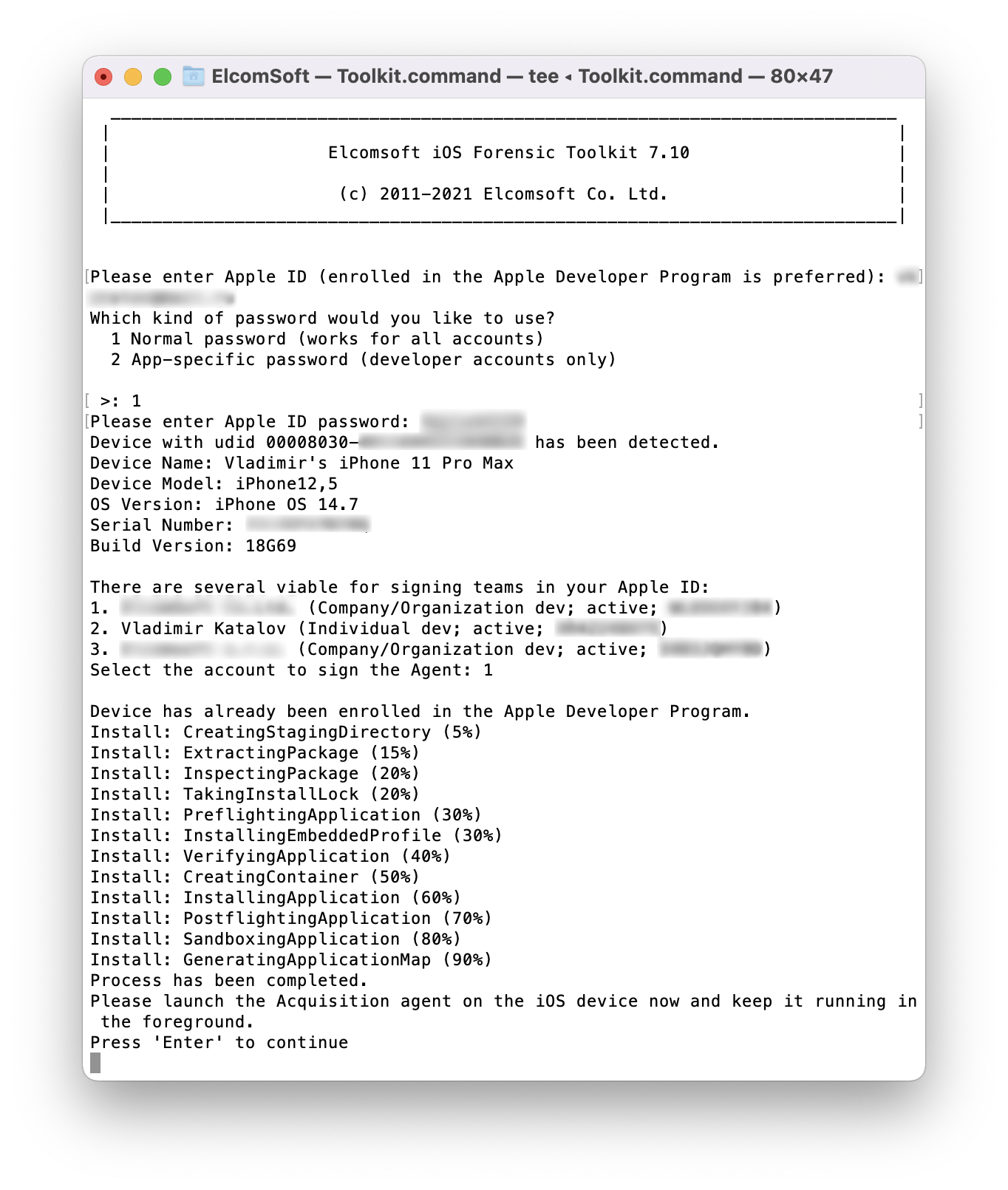
- On the iPhone, launch the extraction agent by tapping its icon.Windows: developer account required. Use app-specific password.
macOS: developer account not required but strongly recommended. For non-developer accounts, use the regular password and pass 2FA. If a non-developer account is used, you will have to trust the certificate in device settings; for this, the device must establish an Internet connection. To avoid this, use developer account. For developer accounts, you can use either the regular password and 2FA, or an app-specific password, which you can specify in the EIFT config file to automate authentication. - If supported, extract the keychain. The keychain can be extracted from all supported devices and iOS versions except A12/A13 devices running iOS 14.5-14.8.
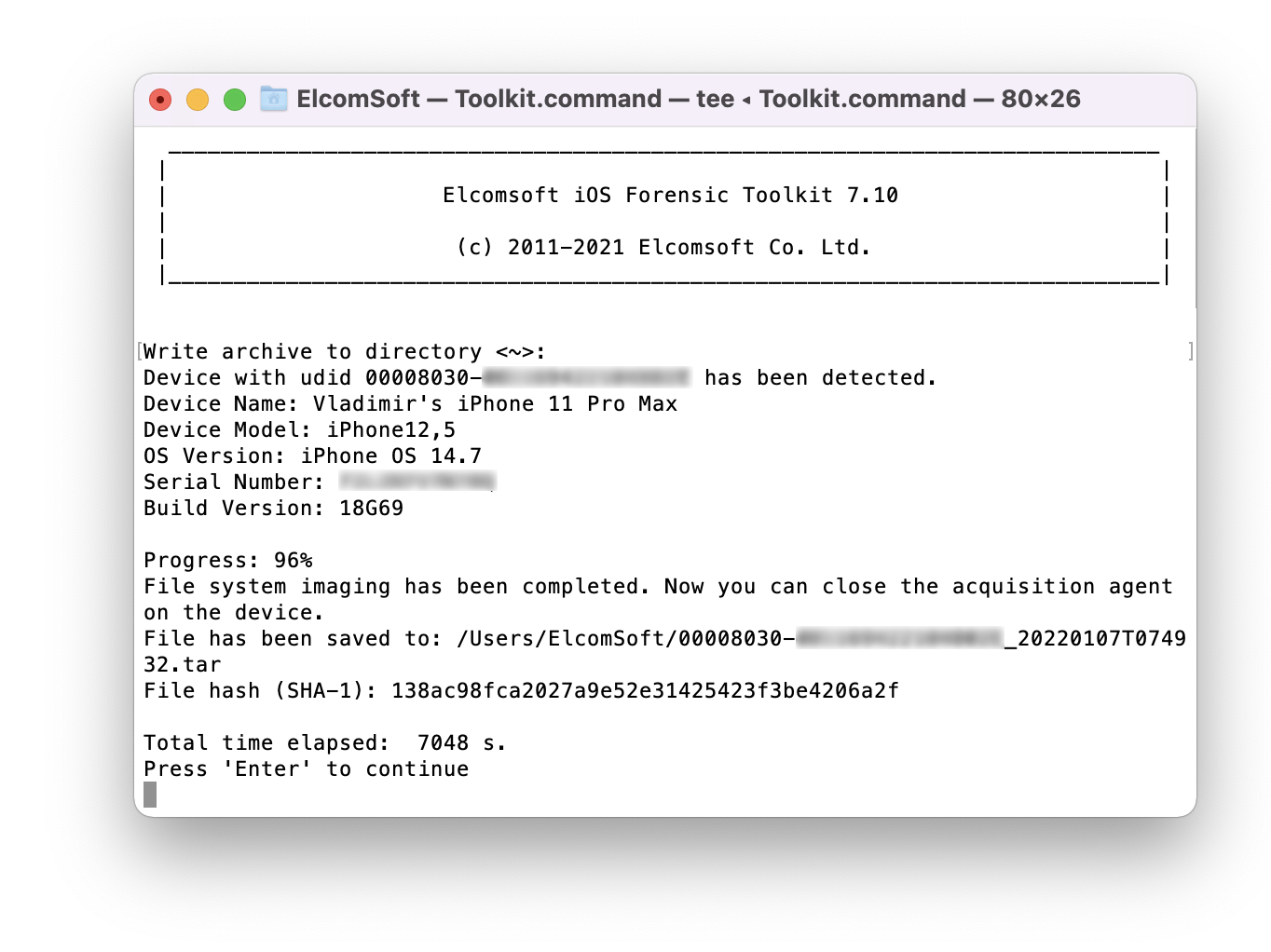
- Extract file system image (full file system or data partition). We recommend extracting the data partition only; the full image may be usable e.g. to check the system partition for persistent malware.
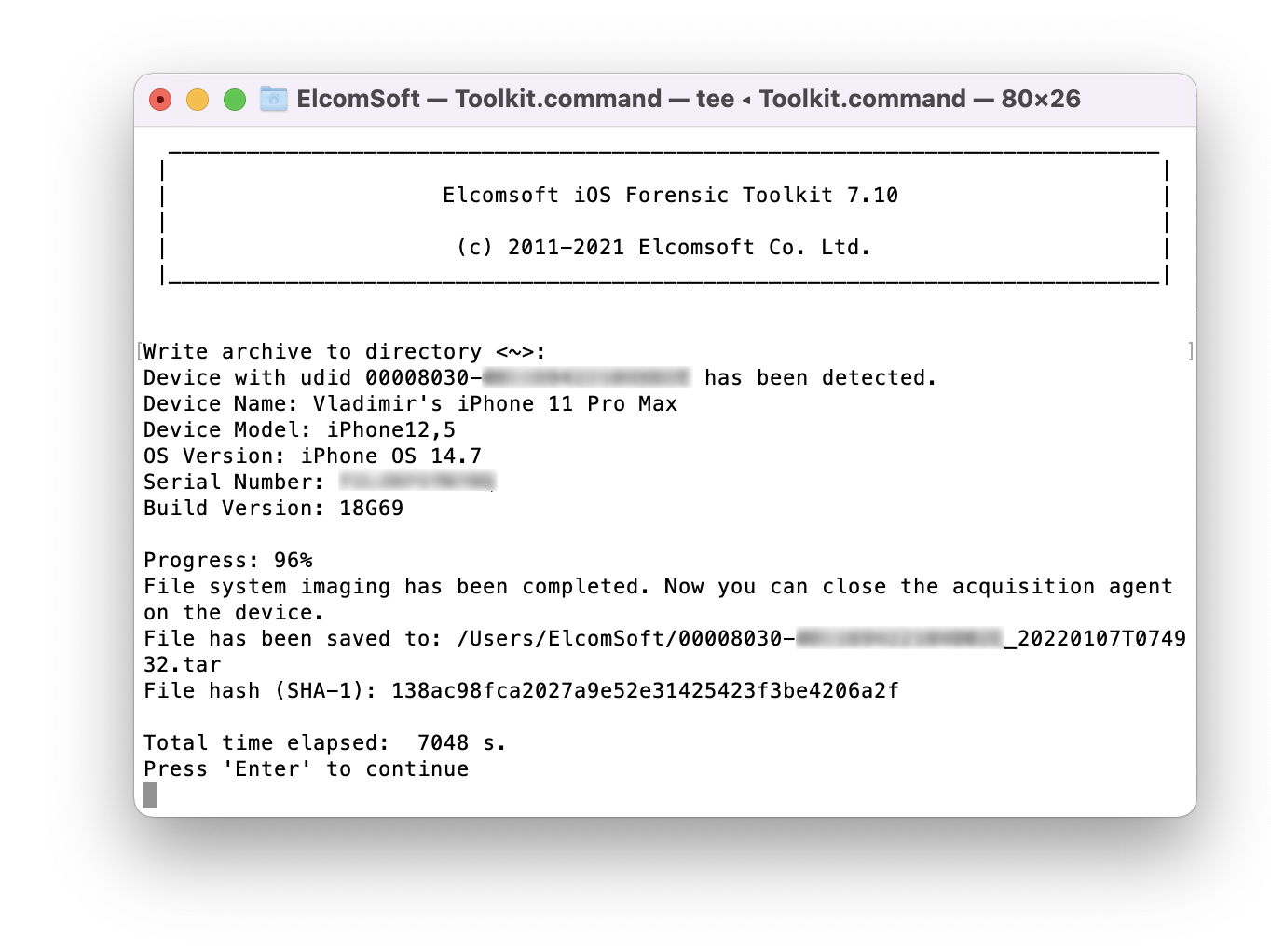
- On the iPhone, uninstall the extraction agent in a regular way.
- You may now disconnect the iPhone and start analyzing the data.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh
