
Hi folks, welcome back I am here with a pretty cool writeup on IDOR vulnerability. First of all, IDOR means Insecure Direct Object Reference.
This sort of weakness can happen when a web server gets client provided contribution to recover objects (records, information, reports), an excess of trust has been put on the information, and it isn’t approved on the server-side to affirm the mentioned object has a place with the client mentioning it.
Task:
What does IDOR stand for?
Insecure Direct Object Reference
IDOR Example:
Instructions are depicted in the below picture order and shipment details of a particular person.

We have to find the unique id of the particular person who made ordered products. So we have to manually click into the emails whether any details leaked out or not.

Yeah, when I clicked [email protected] which gave me an ordered invoice.
After clicking that invoice which gave a page

I highlighted the number 1234 as the unique id of a particular person we have to change as 1000 in order to acquire other personal details.
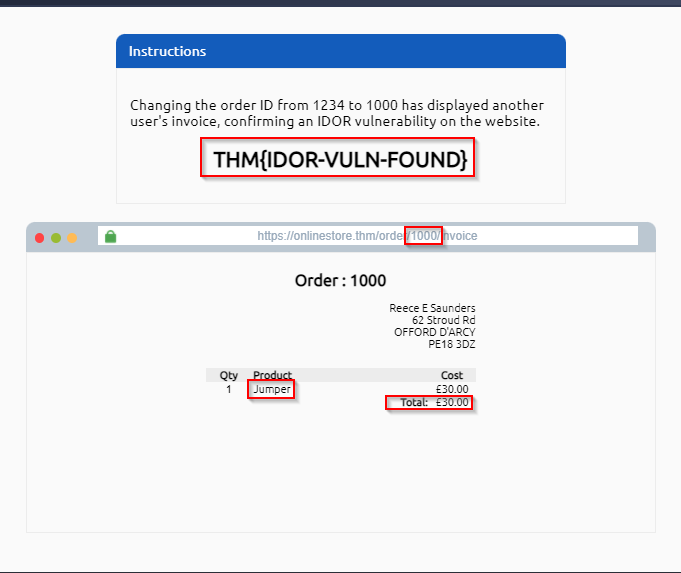
After changing that number we could able to see other personal information.
Finding IDOR in encoded ID’s:
When sending data from one page to another where data includes cookies, post data, and so on. Web developers make use of encoding techniques to hide information from hackers. One of the crucial methods is the base64 encoding technique.
Task:
What is a common type of encoding used by websites?
base64
Finding IDOR’s in Hash id’s
We could decode the hash id and find a unique id with the help of crackstation.net.
hash given is 202cb962ac59075b964b07152d234b70 and it’s format is md5 hash. After decoding the hash we will get the result as 123.
Finding IDOR’s with Unpredictable ID’s
We are not able to find the IDOR on the web application just to create two accounts and swap the IDs that you created to check whether one logged is changed to another if it’s changed then it’s IDOR.
task:
What is the minimum number of accounts you need to create to check for IDORs between accounts?
2
Practical IDOR example: Site for testing the IDOR vulnerability

Manually looking for any endpoints after that I found one.
I found the customer’s login/signup area in that I made signup and logged in.

This is my dashboard where I perform some tasks.

In order to find unique id parameters and values, I use the network tab.

After I changed the value to 1 it would show me the id with username and email id details.

Hope you enjoyed this writeup, in the future, you want to read more writeups like this follow me for updates 😉😉💥💥.
如有侵权请联系:admin#unsafe.sh