2020-10-21 15:55:08 Author: blog.elcomsoft.com(查看原文) 阅读量:303 收藏
We have plugged the last gap in the range of iOS builds supported on the iPhone 5s and 6. The full file system extraction and keychain decryption is now possible on these devices regardless of the version of iOS they are running – at least if that’s iOS 9 or newer. For all other iOS devices up to and including the iPhone 11 Pro Max, we can extract them without a jailbreak if they are running iOS 9 through 13.5 without exceptions. Read how we made this possible.
The iOS 12 conundrum
iOS 12 is somewhat unusual. It’s the last version of iOS available for some devices such as the iPhone 5s, 6, and 6 Plus. At the same time, it was available on newer devices as well, starting with the iPhone 6s all the way up to the iPhone 11 Pro Max.
Once iOS 13 was made available for supported devices (in this case, it was the iPhone 6s and newer), Apple stopped updating iOS 12 for these devices. In the end, the last version of iOS available for the iPhone 6 through iPhone 11 range was iOS 12.4.1.
On the other hand, the iPhone 5s and 6 range was not upgraded to iOS 13, so Apple continued maintaining iOS 12 on these devices for some time longer. As a result, we’ve seen releases in the range of 12.4.2 through 12.4.8 made exclusively for the iPhone 5s, 6, and 6 Plus range, iOS 12.4.8 being the current and actively signed system version for these devices.
There is another thing interesting about iOS 12. The iOS 12.0 – 12.2 range had a vulnerability that was exploited by jailbreakers. Apple patched the vulnerability in iOS 12.3, but in an unprecedented move unpatched it in iOS 12.4, then patched it back in iOS 12.4.1.
All this conundrum made experts struggled to extract these devices. As the jailbreaking community moved on and concentrated their efforts on newer devices and iOS 13, the newly discovered universal exploit for all versions of iOS 12 all devices was never utilized on older devices (the exploit itself had never worked reliably to start with).
Then another universal exploit had appeared, this time covering the whole range of systems from iOS 9 through 13.4.1. This exploit, however, could not be used to obtain root access. Instead, injected code was executed under the user “mobile”. This user had the right to access the file system (which we did when we implemented support for it), but not the keychain. We ended up with a halfway solution: for some versions of iOS we could extract the file system and decrypt the keychain; for others, it was just the file system. All this was utterly confusing for our customers; we even had to create (and update, and update again and again) the complex infographics to show which way it was for a given OS.
As new exploits kept creeping up, we finally caught one for iOS 12.3 to 12.4.8. Implementing this exploit was neither easy nor direct, as Apple used a vastly different memory architecture in the iPhone 6s onwards.
Long story short, we implemented the exploit in our extraction agent. Today, we are proud to announce two major achievements.
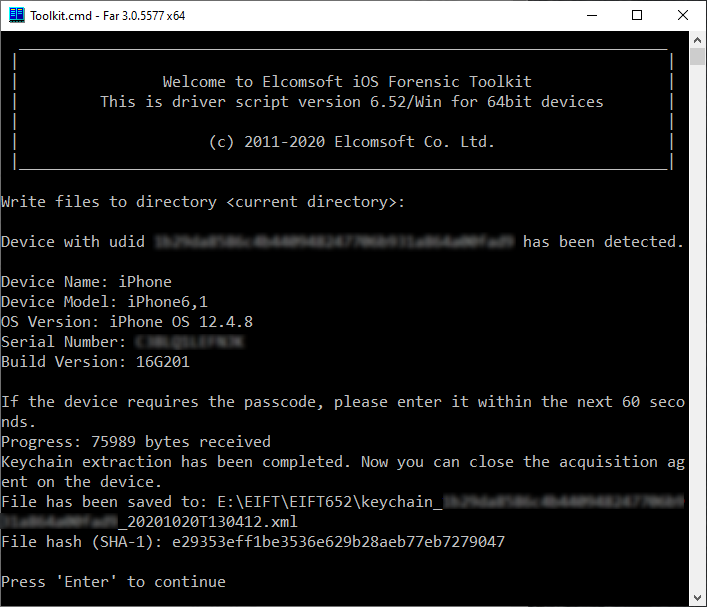
Starting today, users of iOS Forensic Toolkit 6.52 and newer will be able to perform the complete extraction (file system and keychain) of the iPhone 5s, 6 and 6 Plus devices running all versions of iOS starting with iOS 9.0 up to the currently signed version 12.4.8.
In addition, you’ll be able to extract the file system and decrypt the keychain from all other iOS devices in the iPhone 6s through iPhone 11 Pro Max range running all versions of iOS 9.0 through 13.5 with no gaps or exceptions.
Complex infographics is no longer required, so here we are with the simple one:
Steps to extract the file system and decrypt the keychain
To extract the file system and decrypt the keychain from an iOS device without a jailbreak, follow these steps.
- Launch iOS Forensic Toolkit 6.52 or newer.
- Press 1 to sideload the agent onto the device
- Press 2 to extract and decrypt the keychain
- Press 3 or 4 to extract the file system image
- Press 5 to remove the extraction agent from the device
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh