好的,我现在需要帮用户总结这篇文章的内容,控制在100个字以内。首先,我得通读整篇文章,抓住主要信息。 文章讲的是Check Point发现了一个网络钓鱼活动,这个活动与朝鲜相关的KONNI组织有关。他们主要针对软件开发者,尤其是区块链领域的。攻击手段是用假的区块链项目文档作为诱饵,通过Discord分发ZIP文件,里面包含PDF和LNK文件。LNK文件启动了一个PowerShell加载器,下载更多的恶意软件组件。 特别值得注意的是,这次攻击中使用了AI生成的PowerShell后门程序。这个后门程序有清晰的文档、模块化结构和注释,这些都是AI生成代码的特征。此外,恶意软件还具备反分析、沙盒逃避等高级功能。 文章还提到KONNI组织过去常用的战术在这次活动中也有体现,比如使用武器化的LNK文件和多阶段执行链。但这次活动扩展了地理目标范围,并且引入了AI工具,显示了威胁行为体技术的进步。 总结一下关键点:KONNI组织利用AI生成的恶意软件进行网络钓鱼攻击,目标是区块链开发人员,通过Discord分发恶意文件,并且具备高级功能。 现在需要把这些信息浓缩到100字以内。要确保包括攻击者(KONNI)、目标(区块链开发者)、手段(AI生成PowerShell)、传播方式(Discord)以及攻击特点(多阶段、反分析)。 可能的结构:Check Point发现朝鲜关联的KONNI组织利用AI生成PowerShell后门进行钓鱼攻击,目标为区块链开发者,通过Discord分发恶意文件,并具备反分析等功能。 检查字数是否合适,并调整用词使其更简洁。 </think> Check Point发现朝鲜关联的KONNI组织利用AI生成PowerShell后门进行钓鱼攻击,目标为区块链开发者。该活动通过Discord分发ZIP文件中的PDF和LNK诱饵启动恶意载荷,并具备反分析和沙盒逃避功能。 2026-1-26 10:47:25 Author: securityaffairs.com(查看原文) 阅读量:0 收藏
North Korea–linked KONNI uses AI to build stealthy malware tooling

Check Point links an active phishing campaign to North Korea–aligned KONNI, targeting developers with fake blockchain project docs and using an AI-written PowerShell backdoor.
Check Point Research uncovered an active phishing campaign attributed to the North Korea–linked KONNI group (aka Kimsuky, Earth Imp, TA406, Thallium, Vedalia, and Velvet Chollima). The operation targets software developers and engineers using fake project documentation tied to blockchain and crypto initiatives. While consistent with KONNI’s known spear-phishing tactics, the campaign shows broader APAC targeting and features an AI-written PowerShell backdoor, highlighting evolving threat actor tradecraft.
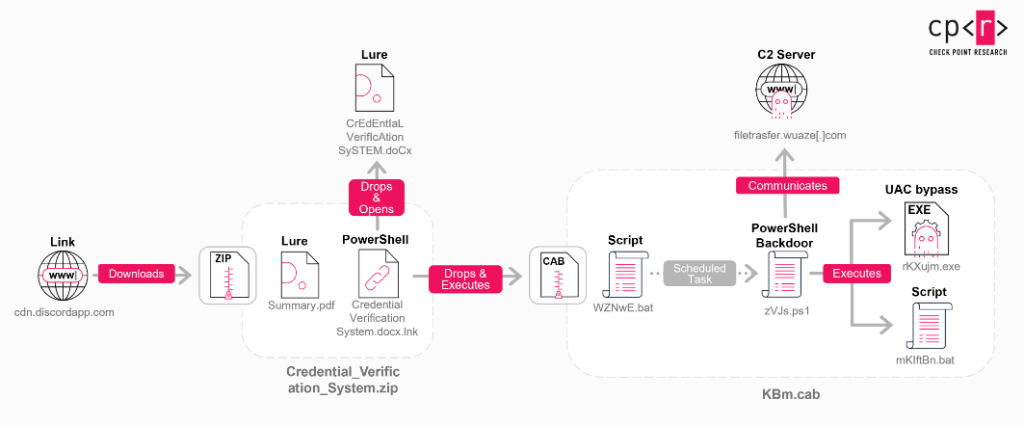
The campaign shows expanded geographic reach beyond South Korea, with samples linked to Japan, Australia, and India. It targets engineering teams, especially those working on blockchain technologies, using lure documents disguised as legitimate project materials. These lures aim to compromise development environments and access sensitive assets such as infrastructure, credentials, wallets, and cryptocurrency. The infection chain uses a Discord-hosted ZIP containing a PDF and LNK file, which launches an obfuscated PowerShell loader.
“The infection chain starts with a Discord-hosted link that downloads a ZIP archive via an unknown vector. The ZIP contains two files: a PDF lure document and a Windows shortcut (LNK) file.” reads the report published by CheckPoint. “The LNK launches an embedded PowerShell loader which extracts two additional files: a DOCX lure document and a CAB archive, both embedded within the LNK and XOR-encoded using a single-byte key.”
The malware establishes persistence via a scheduled task masquerading as OneDrive and deploys a heavily obfuscated PowerShell backdoor executed in memory.

The PowerShell backdoor shows strong signs of AI-assisted development rather than traditional APT tooling. The script features unusually clear documentation, modular structure, and instructional comments such as “your permanent project UUID,” a hallmark of LLM-generated code.
“This phrasing is highly characteristic of LLM-generated code, where the model explicitly instructs a human user on how to customize a placeholder value. Such comments are commonly observed in AI-produced scripts and tutorials.” reads the report. “The verbose documentation, modular layout, and instructional placeholder comments all strongly suggest that the PowerShell backdoor was generated using an AI system, marking a notable shift in KONNI APT’s tooling development.”
Beyond its AI-like coding style, the backdoor includes robust anti-analysis checks, sandbox evasion, user-interaction validation, and single-instance enforcement via a global mutex. The malicious code fingerprints hosts for C2 tracking, adapts execution based on privilege level, performs UAC bypass and Defender evasion, and can deploy legitimate RMM software for persistence. C2 access is achieved by emulating JavaScript challenges to bypass browser-only protections, enabling ongoing command execution and data exfiltration.
Earlier samples uploaded to VirusTotal in October 2025 show an older version of the infection chain. This version starts with an obfuscated PowerShell script that downloads several components, including batch files, VBScript launchers, a PowerShell backdoor, and PE files such as uc.exe for UAC bypass and OneDriveUpdater.exe. The OneDriveUpdater tool installs a SimpleHelp client to give attackers remote access.
Execution starts with start.vbs, which launches simi.bat. This script creates a staging folder in C:\ProgramData, moves the downloaded files there, runs OneDriveUpdater.exe, and then starts schedule1.bat. The final script sets up persistence by creating a scheduled task that runs the PowerShell backdoor. Unlike later samples, this variant splits tasks across multiple scripts instead of using a single batch file.
Check Point states that the campaign’s TTPs closely match those of the North Korea–linked KONNI APT group. It begins with a weaponized LNK file that mirrors KONNI launchers seen in earlier reports, including reuse of a known lure filename. The execution chain follows KONNI’s typical modular, multi-stage design using VBS and multiple BAT scripts, each with a specific role. Earlier variants also reuse script names and code patterns tied to past KONNI activity, reinforcing attribution to the group.
“This campaign highlights the evolution of the KONNI APT group. The delivery and staging remain aligned with previously documented KONNI tradecraft, including the use of weaponized LNK shortcuts and a modular, multi-stage execution chain built from narrowly scoped script components.” concludes the report. “At the same time, the targeting reflects a notable shift in behavior.” “Finally, this campaign is notable for its apparent use of an AI-written PowerShell backdoor. “
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, KONNI)
如有侵权请联系:admin#unsafe.sh