嗯,用户让我总结一下这篇文章的内容,控制在100个字以内,而且不需要特定的开头。首先,我得仔细阅读文章内容。 文章主要讲的是网络扫描活动,从2026年1月13日开始,用户传感器在21号开始检测到扫描。攻击者在寻找特定的目录和文件,比如.env、terraform.tfstate这些。还提到了使用Gephi和Kibana ES|QL进行分析,并列出了两个IP地址作为指标。最后还邀请反馈工具信息。 接下来,我需要把这些关键点浓缩到100字以内。确保涵盖时间、扫描目标、分析工具和IP地址,以及反馈部分。这样用户就能快速了解文章的核心内容了。 </think> 文章描述了网络扫描活动的时间线、目标目录及文件模式,并通过Gephi和Kibana分析展示了相关IP地址的扫描行为。涉及的关键文件包括.env系列、terraform.tfstate等敏感配置文件。 2026-1-26 00:59:32 Author: isc.sans.edu(查看原文) 阅读量:7 收藏
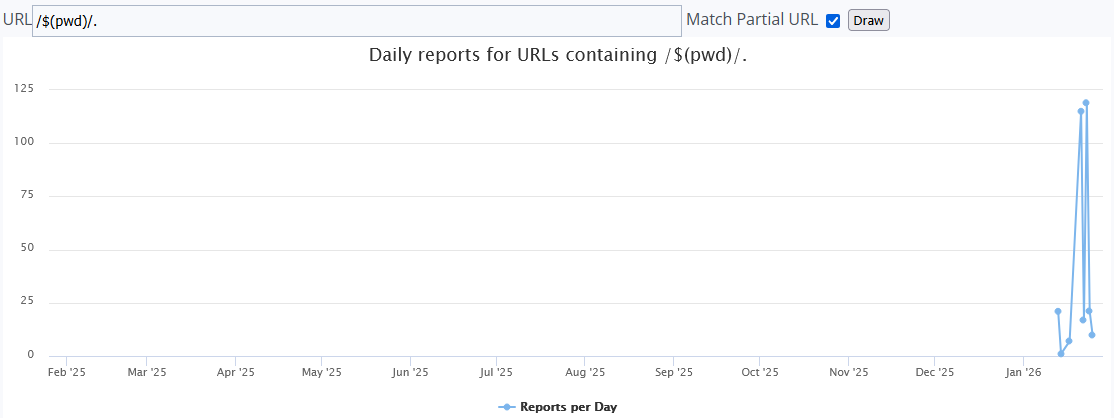
Based on the sensors reporting to ISC, this activity started on the 13 Jan 2026. My own sensor started seeing the first scan on the 21 Jan 2026 with limited probes. So far, this activity has been limited to a few scans based on the reports available in ISC [5] (select Match Partial URL and Draw):
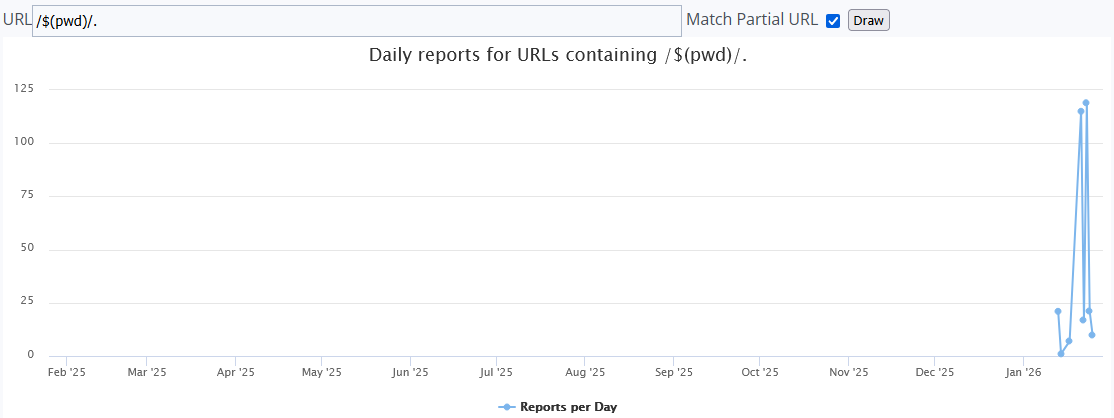
This is a sample list of the directories actors are scanning for using the following patterns:
/$(pwd)/.env.staging
/$(pwd)/.env.development
/$(pwd)/.env.production
/$(pwd)/.env.local
/$(pwd)/.env
$(pwd)/terraform.tfstate
/$(pwd)/docker-compose.yml
/$(pwd)/netlify.toml
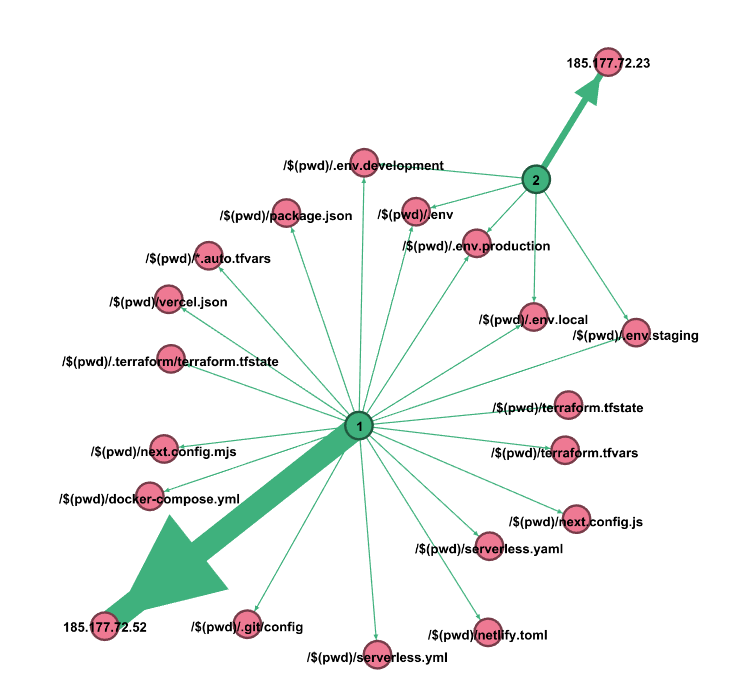
This Gephi graph shows the relationship of each probed URL by the two IP addresses:
Kibana ES|QL Query
FROM cowrie*
| WHERE event.reference == "no match"
| KEEP related.ip,http.request.body.content
| WHERE http.request.body.content IS NOT NULL
| WHERE http.request.body.content RLIKE ".*\\/\\$\\(pwd\\).*"
| STATS COUNT(http.request.body.content) BY related.ip, http.request.body.content
Indicators
By selecting one of these two indicators, it shows their scanning activity for the /$(pwd)/ pattern in the ISC web logs.
We also appreciate feedback and suggestions about what tool is used to perform these scans. Please use our contact page to provide feedback.
[1] https://www.elastic.co/guide/en/elasticsearch/reference/8.19/esql-using.html
[2] https://gephi.org/
[3] https://isc.sans.edu/weblogs/sourcedetails.html?date=2026-01-21&ip=185.177.72.52
[4] https://isc.sans.edu/weblogs/sourcedetails.html?date=2026-01-25&ip=185.177.72.23
[5] https://isc.sans.edu/weblogs/urlhistory.html?url=LyQocHdkKS8uCg==
-----------
Guy Bruneau IPSS Inc.
My GitHub Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
如有侵权请联系:admin#unsafe.sh