
嗯,用户让我总结一篇文章的内容,控制在一百个字以内,而且不需要用“文章内容总结”之类的开头。首先,我需要通读整篇文章,抓住主要信息。 文章讲的是朝鲜黑客组织Konni使用AI生成的PowerShell恶意软件攻击区块链领域的开发者和工程师。他们从2014年开始活跃,主要针对韩国、俄罗斯、乌克兰和欧洲国家。最近的活动集中在亚太地区,包括日本、澳大利亚和印度。 攻击方式是通过Discord链接发送ZIP文件,里面包含PDF诱饵和恶意LNK文件。LNK文件运行PowerShell加载器,释放DOCX文档和CAB存档,里面包含后门、批处理文件和UAC绕过工具。诱饵显示黑客想入侵开发环境,获取敏感资产如API凭证和加密货币。 恶意软件高度混淆,使用算术字符串编码等技术,并且有AI生成的迹象,比如结构化的文档和注释。Check Point研究人员指出这些特征符合AI生成代码的特点,并且提供了IoCs帮助防御。 所以,我需要把这些关键点浓缩到100字以内。确保涵盖Konni组织、目标群体、攻击手段、恶意软件特点以及影响范围。 可能的结构:朝鲜黑客组织Konni利用AI生成的PowerShell恶意软件攻击区块链开发者和工程师。通过Discord链接分发ZIP文件,包含诱饵PDF和恶意LNK文件。该恶意软件旨在入侵开发环境以获取敏感资产,并具有AI生成代码特征。 </think> 朝鲜黑客组织Konni利用AI生成的PowerShell恶意软件攻击区块链开发者和工程师。通过Discord链接分发ZIP文件,包含诱饵PDF和恶意LNK文件。该恶意软件旨在入侵开发环境以获取敏感资产,并具有AI生成代码特征。 2026-1-24 15:30:28 Author: www.bleepingcomputer.com(查看原文) 阅读量:0 收藏

The North Korean hacker group Konni (Opal Sleet, TA406) is using AI-generated PowerShell malware to target developers and engineers in the blockchain sector.
Believed to be associated with APT37 and Kimsuky activity clusters, Konni has been active since at least 2014 and has been seen targeting organizations in South Korea, Russia, Ukraine, and various countries in Europe.
Based on samples analyzed by Check Point researchers, the threat actor's latest campaign focuses on targets in the Asia-Pacific region, as the malware was submitted from Japan, Australia, and India.
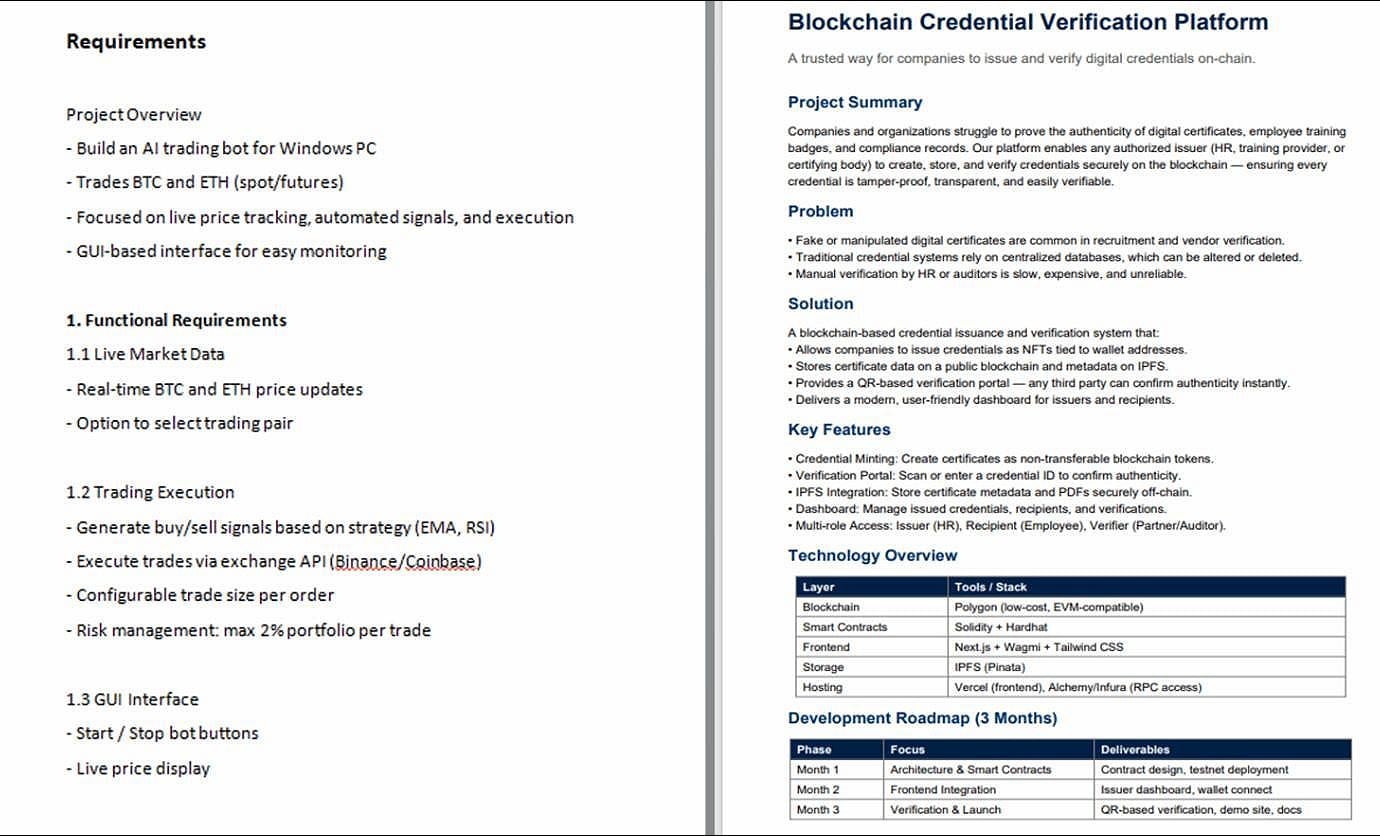
The attack begins with the victim receiving a Discord-hosted link that delivers a ZIP archive containing a PDF lure and a malicious LNK shortcut file.
The LNK runs an embedded PowerShell loader that extracts a DOCX document and a CAB archive containing a PowerShell backdoor, two batch files, and a UAC bypass executable.
Launching the shortcut file causes the DOCX to open and to execute one batch file included in the cabinet file.
Source: Check Point
The lure DOCX document suggests that the hackers want to compromise development environments, which could provide them "access to sensitive assets, including infrastructure, API credentials, wallet access, and ultimately cryptocurrency holdings."
The first batch file creates a staging directory for the backdoor and the second batch file, and creates an hourly scheduled task masquerading as a OneDrive startup task.
This task reads an XOR-encrypted PowerShell script from disk and decrypts it for in-memory execution. Finally, it deletes itself to wipe the signs of infection.
Source: Check Point
AI-generated backdoor
The PowerShell backdoor itself is heavily obfuscated using arithmetic-based string encoding, runtime string reconstruction, and execution of the final logic via ‘Invoke-Expression.’
The researchers say that the PowerShell malware "strongly indicates AI-assisted development rather than traditional operator-authored malware."
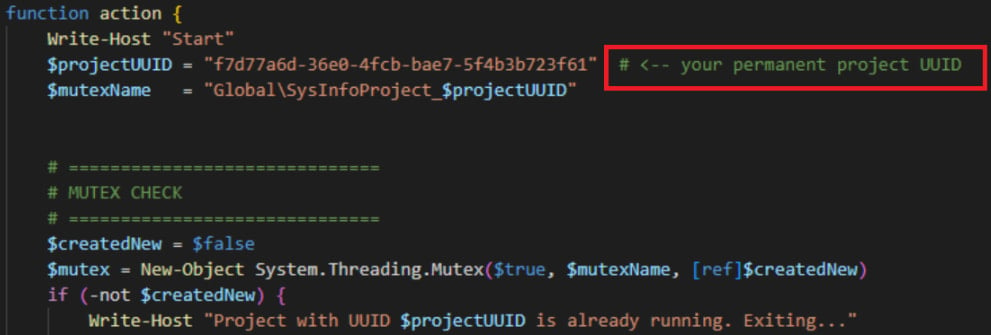
The evidence leading to this conclusion includes the clear, structured documentation at the top of the script, which is unusual for malware development; its modular, clean layout; and the presence of a “# <– your permanent project UUID” comment.
Source: Check Point
"This phrasing is highly characteristic of LLM-generated code, where the model explicitly instructs a human user on how to customize a placeholder value," explains Check Point.
"Such comments are commonly observed in AI-produced scripts and tutorials."
Before execution, the malware performs hardware, software, and user activity checks to ensure it is not running in analysis environments, and then generates a unique host ID.
Next, depending on what execution privileges it has on the compromised host, it follows a separate path of action as shown in the following diagram.
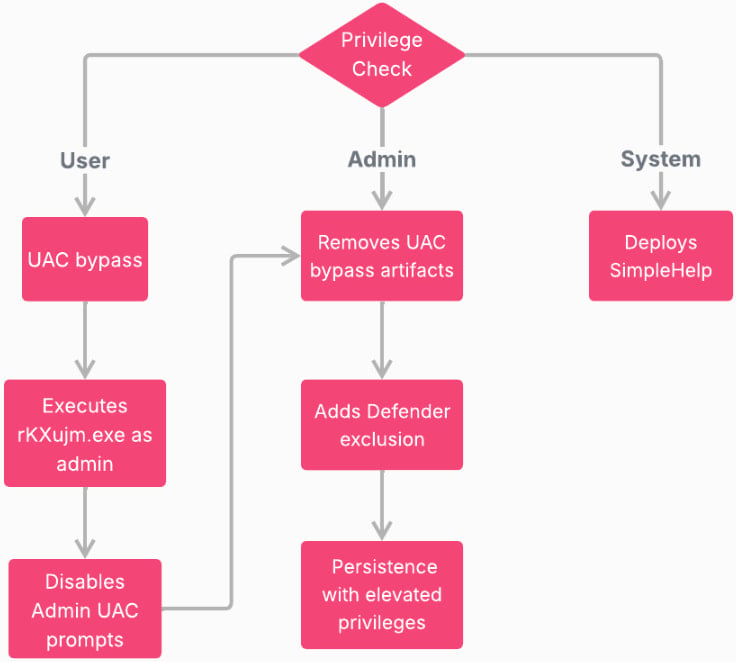
Source: Check Point
Once the backdoor is fully running on the infected device, it periodically contacts the command-and-control (C2) server to send basic host metadata and polls the server at randomized intervals.
If the C2 response contains PowerShell code, it turns it into a script block and executes it asynchronously via background jobs.
Check Point attributes these attacks to the Konni threat actor based on earlier launcher formats, lure filename and script name overlaps, and commonalities in the execution chain structure with earlier attacks.
The researchers have published indicators of compromise (IoCs) associated with this recent campaign to help defenders protect their assets.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
如有侵权请联系:admin#unsafe.sh

