WebARX is a web application firewall where you can protect your website from malicious attac 2019-10-13 07:16:32 Author: osandamalith.com(查看原文) 阅读量:56 收藏
WebARX is a web application firewall where you can protect your website from malicious attacks. As you can see it was mentioned in TheHackerNews as well and has good ratings if you do some Googling.
https://thehackernews.com/2019/09/webarx-web-application-security.html
It was found out that the WebARX WAF could be easily bypassed by passing a whitelist string. As you see the request won’t be processed by the WAF if it detects a whitelist string.
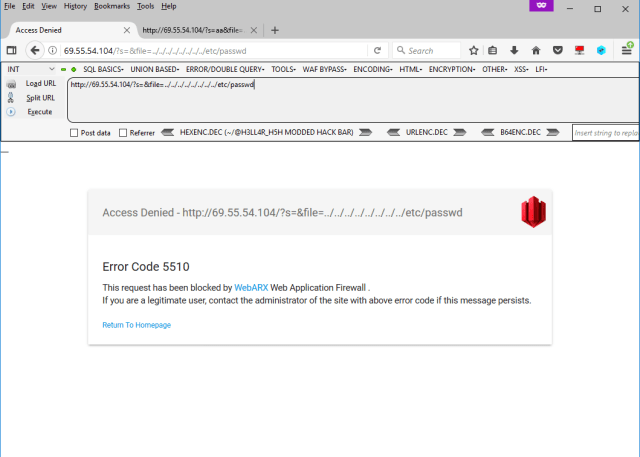
Let’s first try on their own website. This is a simple LFi payload.

Now if I include a whitelist string such as ithemes-sync-request it would be easily bypassed.
XSS PoC
Here’s an XSS PoC where we pass a simple script tag. It detects the raw request when we pass normally.
But if we include ithemes-sync-request parameter which is a whitelist string the script tag will get executed.
LFi PoC
Here’s a normal payload which will block.
Once we apply the whitelist string it’s bypassed.
SQLi PoC
Here’s a normal payload which will block.
Once we apply the whitelist string it’s bypassed.
These whitelist strings are more like a kill switch for this firewall. I’m not quite sure the developers of this project understands the logic behind it. It’s more like coded by an amateur programmer for a university assignment.
Thanks for checking it, we also messaged you, but never heard back. Unfortunately for the sake of balancing false negatives, even more advanced WAFs tend to have ways for bypass (especially with XSS). Thanks for your help and we'll definitely work on improvements!
— WebARX (@webarx_security) October 8, 2019
如有侵权请联系:admin#unsafe.sh







