SEC Consult SA-20250925-0 :: Multiple Vulnerabilities in iMonitorSoft EAM employee monitoring #CVE-2025-10540 #CVE-2025-10541 #CVE-2025-10542
iMonitorSoft EAM 9.6394 存在三个关键漏洞:未加密通信(CVE-2025-10540)、本地权限提升(CVE-2025-10541)及不安全默认凭证(CVE-2025-10542)。这些漏洞可能导致数据泄露、系统控制被接管及未经授权的操作。厂商未提供修复补丁。 2025-9-25 22:49:49 Author: seclists.org(查看原文) 阅读量:3 收藏
iMonitorSoft EAM 9.6394 存在三个关键漏洞:未加密通信(CVE-2025-10540)、本地权限提升(CVE-2025-10541)及不安全默认凭证(CVE-2025-10542)。这些漏洞可能导致数据泄露、系统控制被接管及未经授权的操作。厂商未提供修复补丁。 2025-9-25 22:49:49 Author: seclists.org(查看原文) 阅读量:3 收藏

Full Disclosure mailing list archives
From: SEC Consult Vulnerability Lab via Fulldisclosure <fulldisclosure () seclists org>
Date: Thu, 25 Sep 2025 11:59:35 +0000
SEC Consult Vulnerability Lab Security Advisory < 20250925-0 >
=======================================================================
title: Multiple Vulnerabilities
product: iMonitorSoft EAM
vulnerable version: iMonitor EAM 9.6394
fixed version: -
CVE number: CVE-2025-10540, CVE-2025-10541, CVE-2025-10542
impact: Critical
homepage: https://www.imonitorsoft.com/employee-monitoring-software.html
found: 2025-05-21
by: Marius Renner (Office Bochum)
Daniel Hirschberger (Office Bochum)
Tobias Niemann (Office Bochum)
Thorger Jansen (Office Bochum)
SEC Consult Vulnerability Lab
An integrated part of SEC Consult, an Eviden business
Europe | Asia
https://www.sec-consult.com
=======================================================================
Vendor description:
-------------------
"iMonitor EAM combines user activity monitoring, behavior analytics and
productivity tools in a single console, Prevent insider threats and increase
productivity"
"Centralized Employee Monitoring Solution: iMonitor EAM is a centralized
employee monitoring solution which able to monitor 1000+ client computers with
1 server. [...]"
Source: https://www.imonitorsoft.com/employee-monitoring-software.html
Business recommendation:
------------------------
The vendor was unresponsive and did not answer to our communication attempts.
Therefore, a patch is not available for these security issues. End users of
this product should contact the vendor and demand a patch.
SEC Consult highly recommends performing a thorough security review of the
product conducted by security professionals to identify and resolve potential
further security issues.
Vulnerability overview/description:
-----------------------------------
1) Unencrypted and Unauthenticated Communication (CVE-2025-10540)
The traffic between the EAM client agent and the EAM server, as well as between
the EAM monitor management software and the server is transmitted in plain
text. This means that neither the confidentiality nor the integrity of the
transmitted data is protected from an attacker with access to network traffic.
As the software captures and transmits highly sensitive data such as keylogger
history (which may include personally identifiable information, passwords, and
other sensitive data) this poses a considerable business risk. Furthermore,
an attacker can modify the command and control traffic to issue arbitrary
commands to agents, including commands to run arbitrary applications on the
agent machine.
2) Local Privilege Escalation (CVE-2025-10541)
An attacker can exploit a built-in update mechanism of the agent component
eamusbsrv64.exe to elevate privileges on the local system to
NT Authority\SYSTEM.
3) Insecure Default Credentials (CVE-2025-10542)
After installing the EAM server, access to the monitor management software is
protected using the insecure default credentials with username 'admin' and a
very weak three-digit password. These default credentials are also listed in
the EAM monitor management software connection dialog for convenience. An
attacker can use these default credentials to connect to the server and
perform arbitrary actions on all agents in case the administrator does not
change the password.
Proof of concept:
-----------------
1) Unencrypted and Unauthenticated Communication (CVE-2025-10540)
The communication between the EAM client agent and the EAM server can be
observed using common package capturing tools such as Wireshark. The following
screenshot shows that the observed traffic is unencrypted and contains
sensitive data, such as passwords captured using the keylogger functionality:
<1_1_plaintext_agent_traffic.png>
The communication between the EAM monitor management software and the server is
also unencrypted. Sensitive data such as the EAM monitor password and all data
captured from the agents (which may include personally identifiable
information, passwords, and other sensitive data) can be found in the plain
text traffic, as the following screenshot shows:
<1_2_plaintext_monitor_traffic.png>
2) Local Privilege Escalation (CVE-2025-10541)
The EAM agent installs a system service the runs the agent component
eamusbsrv64.exe as NT Authority\SYSTEM. This executable contains an update
mechanism to update the agent from files stored in path 'C:\sysupdate'. As any
user can create this directory and write to it, this mechanism can be abused by
a local attacker for privilege escalation.
When eamusbsrv64.exe is started, which happens automatically at system startup,
it tests if the file 'C:\sysupdate\finish.txt' exists. If that file exists, all
other files in that directory are moved to the EAM installation directory at
'C:\Windows\System\sys\syscon'. It is possible for an attacker to leverage this
for arbitrary code exection by writing a DLL file with malicous code that will
be loaded by eamusbsrv64.exe, for example wtsapi32.dll. The following
proof-of-concept C code was used to create the DLL:
-------------------------------------------------------------------------------
[ PoC removed ]
-------------------------------------------------------------------------------
The code can be compiled to a DLL using the following command:
x86_64-w64-mingw32-gcc malicious-dll.c -shared -o wtsapi32.dll
To prepare the exploit, the malicious wtsapi32.dll needs to be copied to
'C:\sysupdate\wtsapi32.dll'. Furthermore, the empty file
'C:\sysupdate\finish.txt' needs to be created. The following screenshot shows
the prepared exploit state:
<2_1_sysupdate_contents.png>
To run the exploit, the eamusbsrv64.exe service must be restarted, which can be
accomplished by restarting the computer. After the restart, the 'C:\sysupdate'
directory is empty again, and the exploit has succeeded. The proof-of-concept
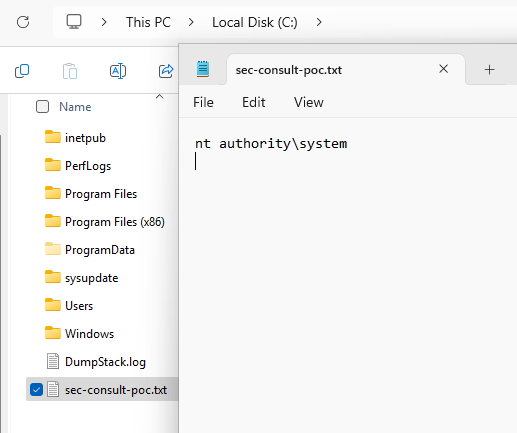
file 'C:\sec-consult-poc.txt' is now present and demonstrates that the exploit
runs with NT Authority\SYSTEM privileges, as the following screenshot shows:
<2_2_proof_of_concept_result.png>
3) Insecure Default Credentials (CVE-2025-10542)
After installing the EAM server, access to the monitor management software is
protected using the insecure default credentials with username 'admin' and
password '000'. These default credentials are also listed in the EAM monitor
management software connection dialog for convenience, as the screenshot below
shows. An attacker can use these default credentials to connect to the server
and perform arbitrary actions on all agents in case the administrator does not
change the password.
<3_1_default_credentials.png>
Vulnerable / tested versions:
-----------------------------
The following version has been tested which was the latest available trial
version at the time of the test:
* iMonitor EAM 9.6394
Vendor contact timeline:
------------------------
2025-07-10: Contacting vendor through support () imonitorsoft com. No response.
2025-07-29: Contacting vendor through support () imonitorsoft com again. No response.
2025-09-16: Trying online support chat form, customer support agent just closed our
chat after asking if we had any questions regarding their product and
answering that we are looking for a security contact.
Sending publication deadline of 25th September to vendor via email.
No response.
2025-09-25: Release of security advisory
Solution:
---------
The vendor was unresponsive and did not answer to our communication attempts.
Therefore, a patch is not available for these security issues. End users of
this product should contact the vendor and demand a patch.
Workaround:
-----------
None
Advisory URL:
-------------
https://sec-consult.com/vulnerability-lab/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
SEC Consult Vulnerability Lab
An integrated part of SEC Consult, an Eviden business
Europe | Asia
About SEC Consult Vulnerability Lab
The SEC Consult Vulnerability Lab is an integrated part of SEC Consult, an
Eviden business. It ensures the continued knowledge gain of SEC Consult in the
field of network and application security to stay ahead of the attacker. The
SEC Consult Vulnerability Lab supports high-quality penetration testing and
the evaluation of new offensive and defensive technologies for our customers.
Hence our customers obtain the most current information about vulnerabilities
and valid recommendation about the risk profile of new technologies.
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Interested to work with the experts of SEC Consult?
Send us your application https://sec-consult.com/career/
Interested in improving your cyber security with the experts of SEC Consult?
Contact our local offices https://sec-consult.com/contact/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Mail: security-research at sec-consult dot com
Web: https://www.sec-consult.com
Blog: https://blog.sec-consult.com
X: https://x.com/sec_consult
EOF Marius Renner, Daniel Hirschberger, Thorger Jansen, Tobias Niemann / @2025
Attachment:
smime.p7s
Description: S/MIME Cryptographic Signature
_______________________________________________ Sent through the Full Disclosure mailing list https://nmap.org/mailman/listinfo/fulldisclosure Web Archives & RSS: https://seclists.org/fulldisclosure/
Current thread:
- SEC Consult SA-20250925-0 :: Multiple Vulnerabilities in iMonitorSoft EAM employee monitoring #CVE-2025-10540 #CVE-2025-10541 #CVE-2025-10542 SEC Consult Vulnerability Lab via Fulldisclosure (Sep 25)
文章来源: https://seclists.org/fulldisclosure/2025/Sep/72
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh




