2024-7-22 10:37:48 Author: www.tgsoft.it(查看原文) 阅读量:0 收藏
Weekly report by TG Soft's CRAM concerning Italian malspam campaigns.
Below the details of the campaigns massively spread during the week from July 15 to July 21, 2024.
In the week monitored, both global campaigns and Italian written campaigns increased compared to the previous week.
The week was characterized by Password Stealers of the Families: AgentTesla, FormBook, LokiBot, Remcos and SnakeLogger.
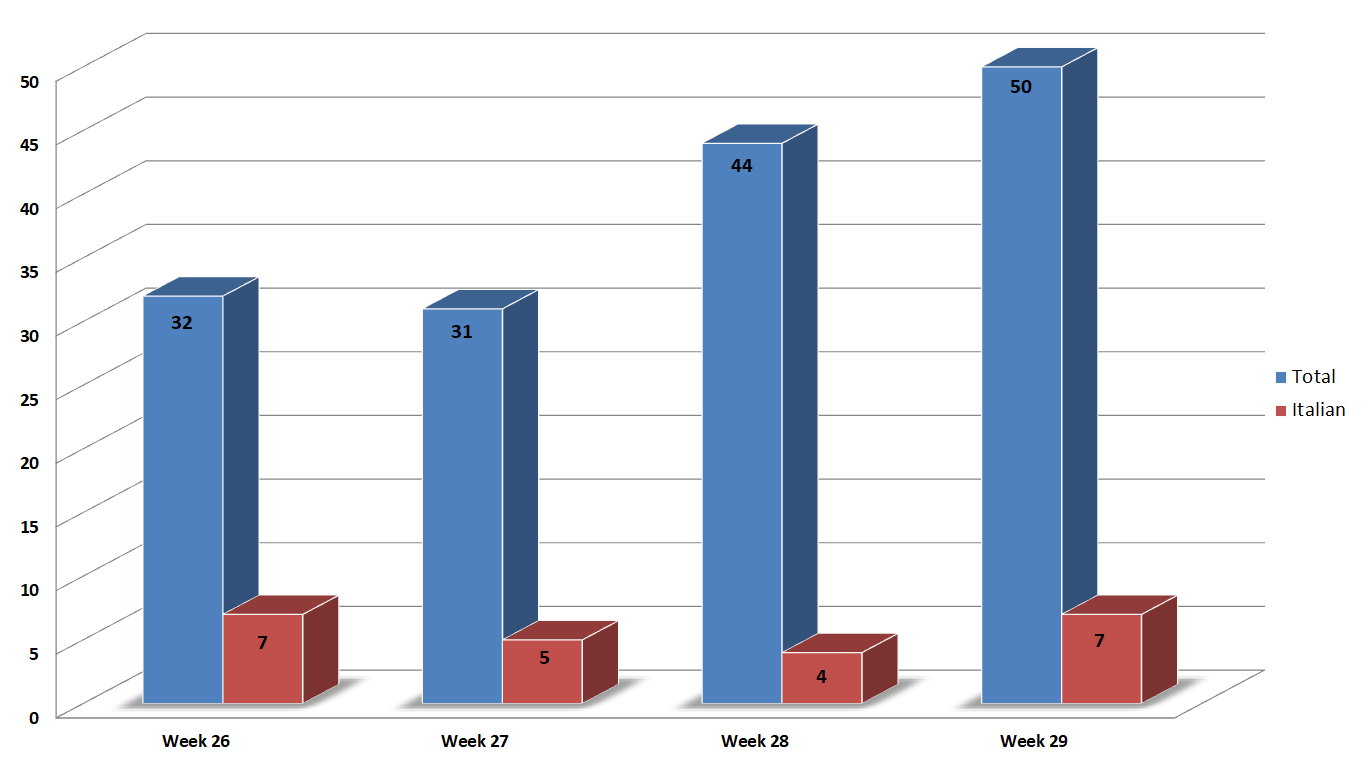
The blue bar indicates the total number of campaigns monitored in Italy in each week, while the red bar concerns campaigns written in Italian (and targeting Italy).
We monitored 50 campaigns during the week, 7 of which used Italian as their language.
In order to understand how the various weeks are divided, below is a small table showing the breakdown of the periods considered:
| Week |
from | to |
| Week_26 | 24/06 | 30/06 |
| Week_27 | 01/07 | 07/07 |
| Week_28 | 08/07 | 14/07 |
| Week_29 | 15/07 | 21/07 |
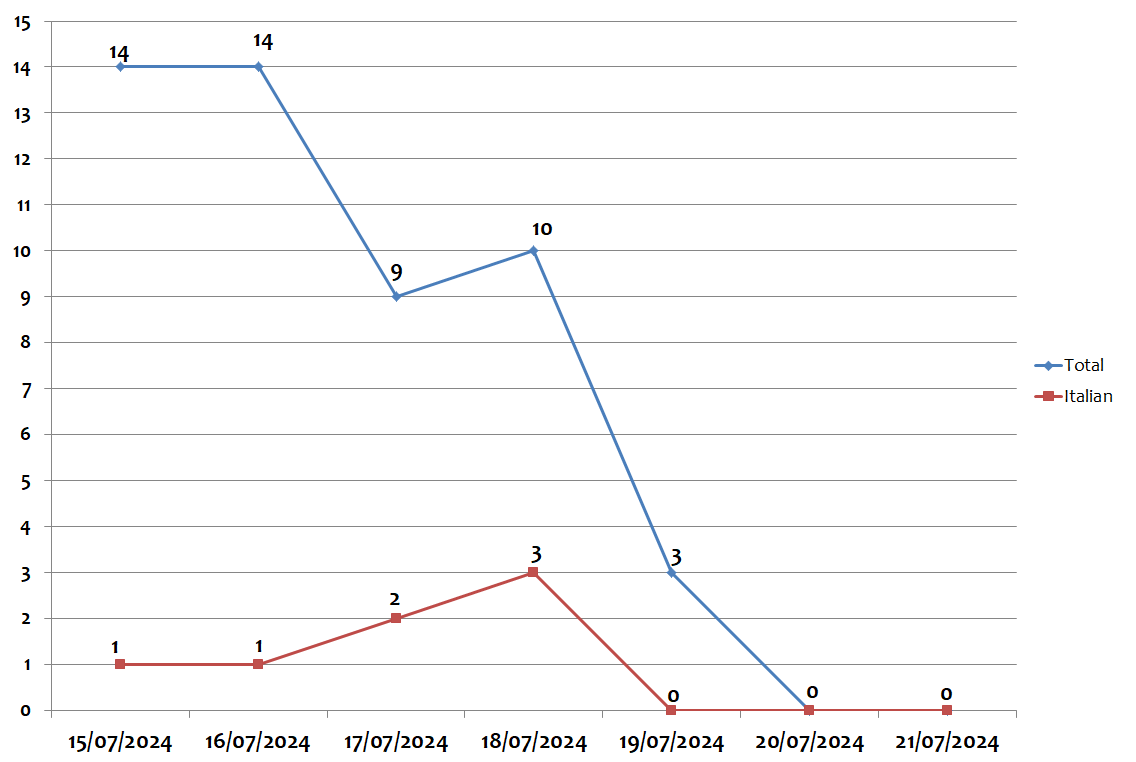
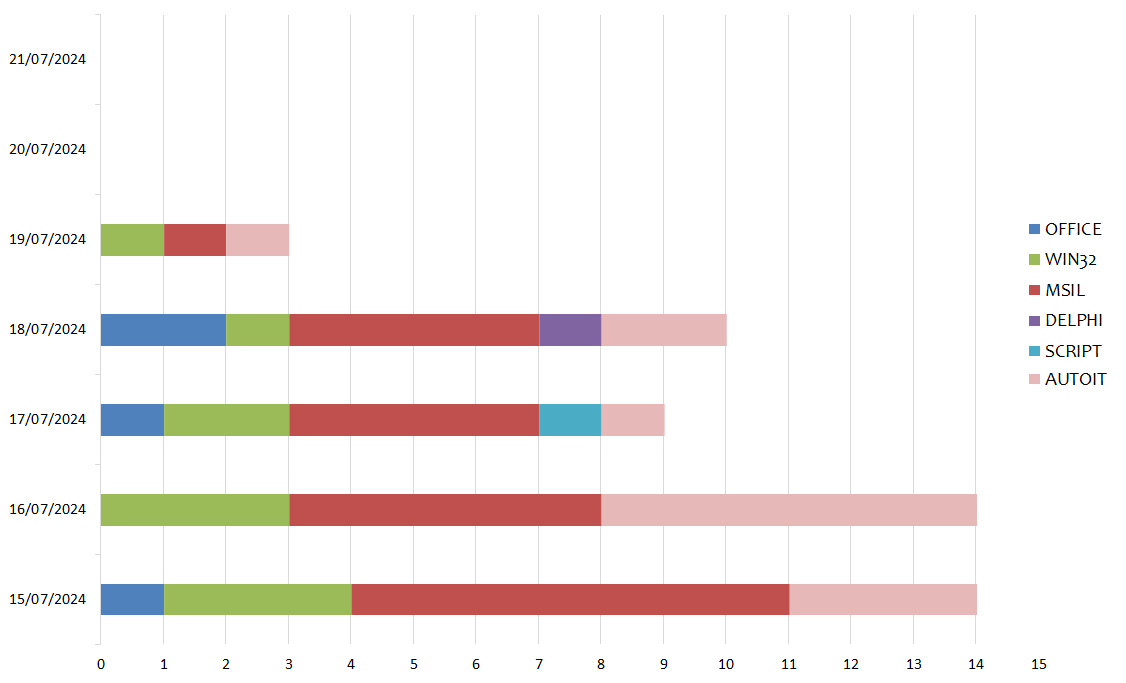
During the week, the peak of global campaigns was found on Monday, July 15 and Tuesday, July 16 with 14 different campaigns per day. The peak of campaigns written in Italian was found on Thursday, July 18 with 3 campaigns per day, as highlighted by the graph below:
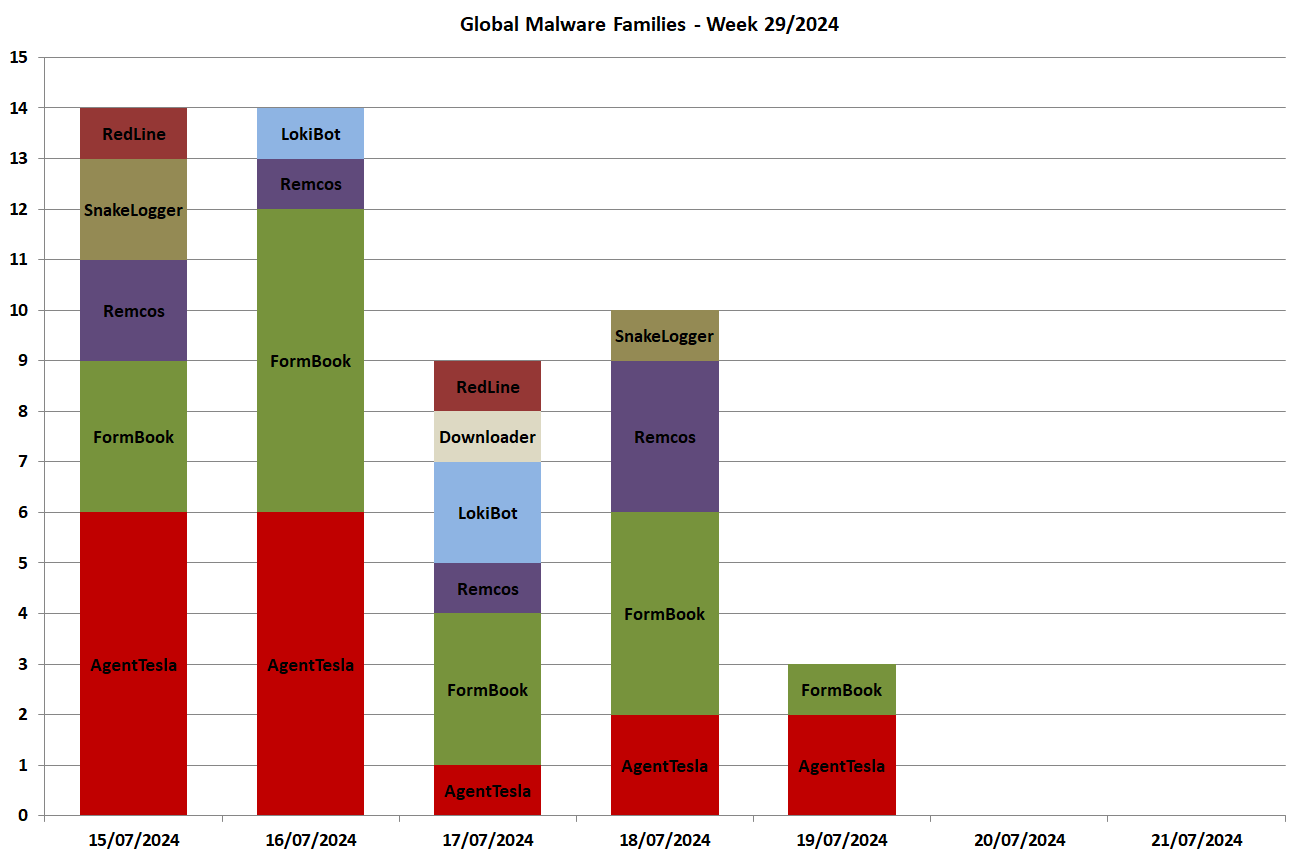
In the following chart we see the malware families spread globally for each day in the week:
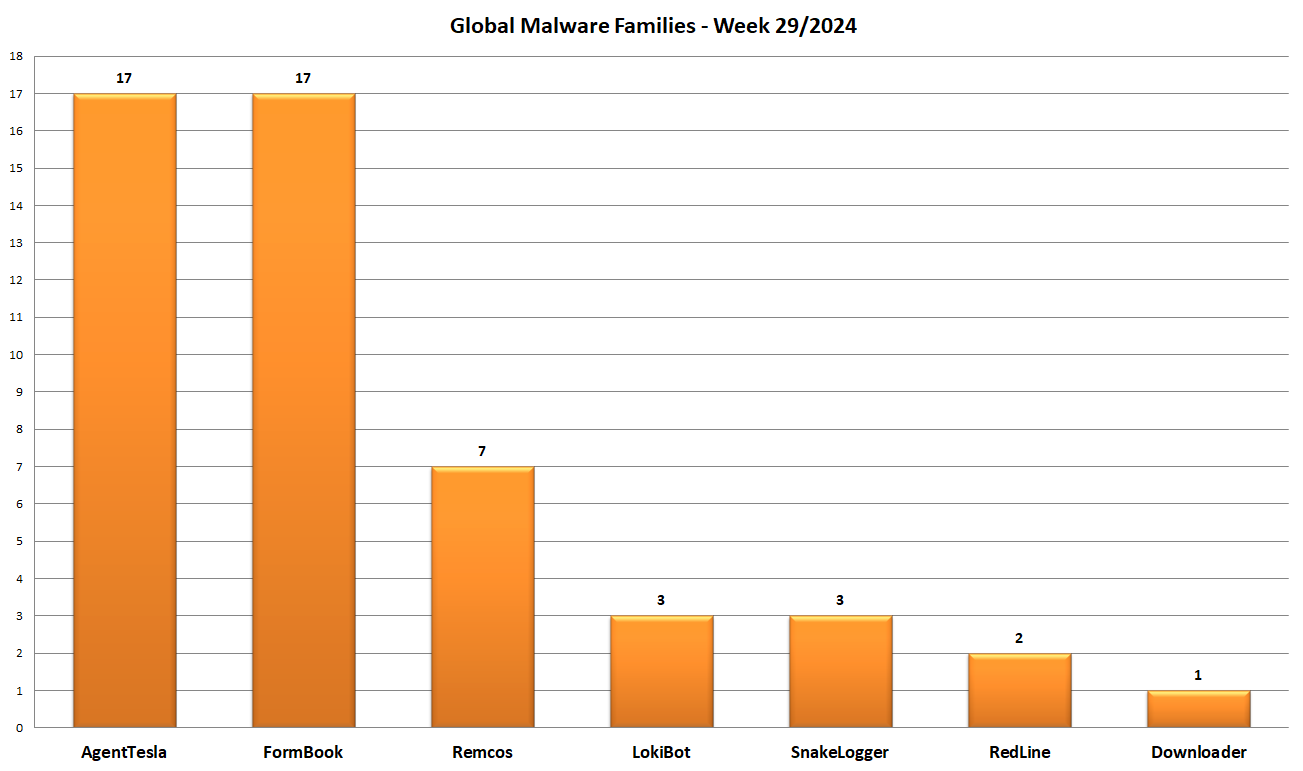
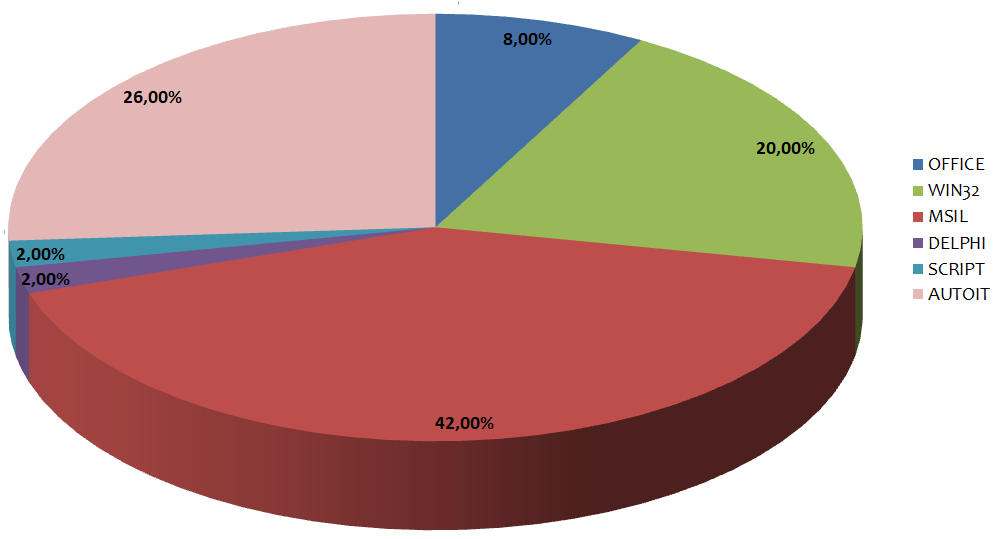
Instead in this graph we see the distribution based on malware family. In the past week 7 different families were detected:
The featured samples this week are MSIL (C#) executibles covering 42% of the malware sent via e-mail.
In second and third place are AutoIT executibles with 26% and WIN32 executable files with 20%.
The 8% of distributed samples are Office documents (Word, Excel, PowerPoint).
In the picture below we can see the various types of language used to develop malware:
In the following graph we see the distribution of the various types of languages divided by day:
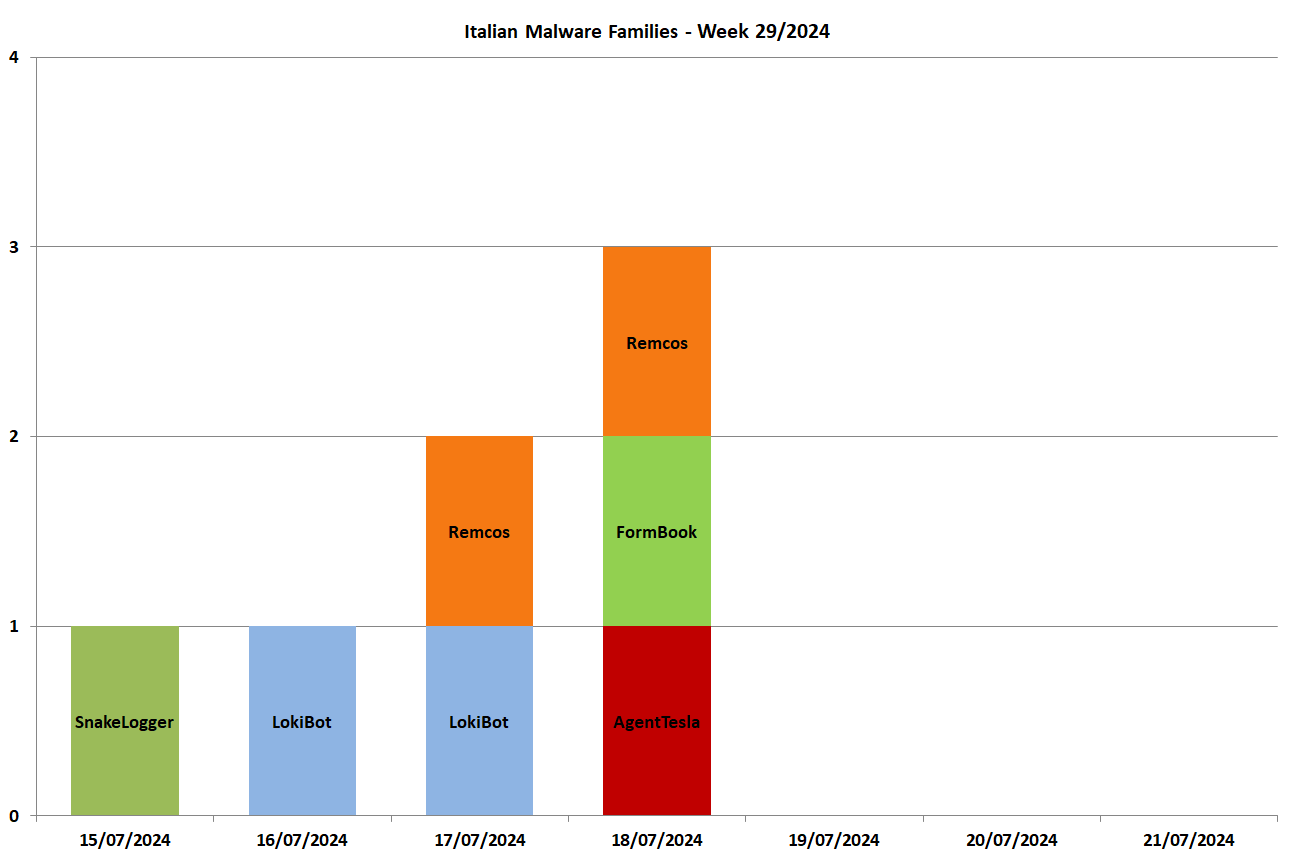
In this graph we can see the malware families spread during the week with target Italy (written in Italian) and composed of 5 different families:
The Italian campaigns analyzed by TG Soft's C.R.A.M. were grouped according to macro categories, obtained from the subject of the email message used for malware distribution (malspam). Below we see the subjects used in the various campaigns divided by day and type of malware
15/07/2024
SnakeLogger - spread through a campaign themed "Invoices".
16/07/2024
LokiBot - spread through a campaign themed "Orders".17/07/2024
LokiBot - spread through a campaign themed "Quotes".
Remcos - spread through a campaign themed "Payments".
18/07/2024
AgentTesla - spread through a campaign themed "Invoices".
FormBook - spread through a campaign themed "Quotes".
Remcos - spread through a campaign themed "Invoices".
EMOTET
In the past week the massive sending of MalSpam emails for the spread of the Emotet malware was not detected.
Find out if you are an Emotet target!
TG Soft, as reported in the information "HAVEiBeenEMOTET portal to find out whether a mailbox has been used in malspam campaigns to spread EMOTET ", has provided and maintained for over a year the HAVEiBeenEMOTET service, that can help you to check if your email addresses or domains are targeted by Emotet.
Using this service you can check for free if your email addresses/domains are involved or are targets of MalSpam by Emotet.
Advanced search features and the IOC feed are available by registering and activating the API service at the link: HAVEiBeenEMOTET - API
Check out the June/July campaigns
Any information published on our site may be used and published on other websites, blogs, forums, facebook and/or in any other form both in paper and electronic form as long as the source is always and in any case cited explicitly “Source: CRAM by TG Soft www.tgsoft.it” with a clickable link to the original information and / or web page from which textual content, ideas and / or images have been extrapolated.
It will be appreciated in case of use of the information of C.R.A.M. by TG Soft www.tgsoft.it in the report of summary articles the following acknowledgment/thanks “Thanks to Anti-Malware Research Center C.R.A.M. by TG Soft of which we point out the direct link to the original information: [direct clickable link]”
如有侵权请联系:admin#unsafe.sh