2024-9-4 17:27:12 Author: www.tgsoft.it(查看原文) 阅读量:0 收藏
PHISHING INDEX
Below are the most common email phishing attempts detected by TG Soft's Anti-Malware Research Center in September 2024:
30/09/2024 => TELEPASS
29/09/2024 => TELEPASS
24/09/2024 => Aruba - Fattura scaduta (Expired invoice)
17/09/2024 => MPS
15/09/2024 => SexTortion
14/09/2024 => Account di Posta (Email Account)
12/09/2024 => Aruba
12/09/2024 => Mooney
11/09/2024 => Poste Italiane
09/09/2024 => Webmail
07/09/2024 => Smishing Istituto Bancario (Bank)
06/09/2024 => Aruba - Accesso non riconosciuto (Unrecognized access)
06/09/2024 => Leroy Merlin
02/09/2024 => Account di Posta (Email Account)
02/09/2024 => Esselunga
These emails are intended to trick some unfortunate person into providing sensitive data - such as bank account information, credit card codes or personal login credentials - with all the possible easily imaginable consequences.
September 29-30, 2024 ==> Phishing TELEPASS
Below we analyze the attempted scam, hidden behind false communications by the well-known Italian company TELEPASS, which is active in urban and suburban mobility services.
The following 2 messages, graphically and textually different, both aim to simulate a real unmissable opportunity. The lucky user has been selected as winner of a fantastic prize, a new "CAR EMERGENCY KIT," which can be claimed by participating in a lottery through a short survey ...or so it seems.
Example No. 1
SUBJECT: <Hai vinto un kit di emergenza per auto ioWSR> (You won an ioWSR car emergency kit)
This phishing is certainly a real decoy for many inexperienced users.
Clearly the well-known company TELEPASS is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance..
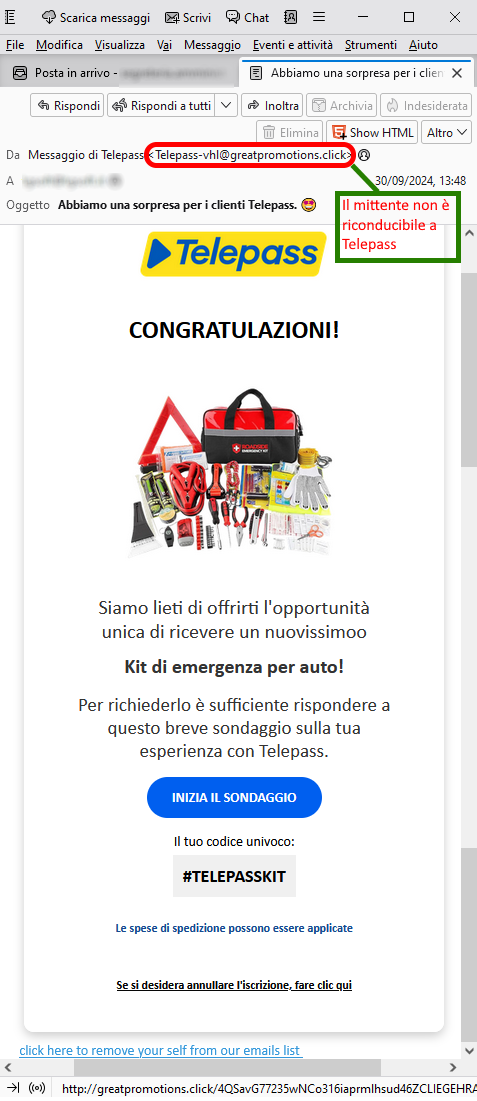
When we analyze the email, we notice that the message comes from an email address <jh532dg[at]fucinalab[dot]it> clearly not traceable to the official domain of TELEPASS . This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the link provided, here is what happens:
we are redirected to a landing page that, although graphically well designed (with misleading images and the authentic logo of TELEPASS), does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following anomalous address/domain:
https[:]//[NomeDominioFake*].info...
which has no connection with TELEPASS.
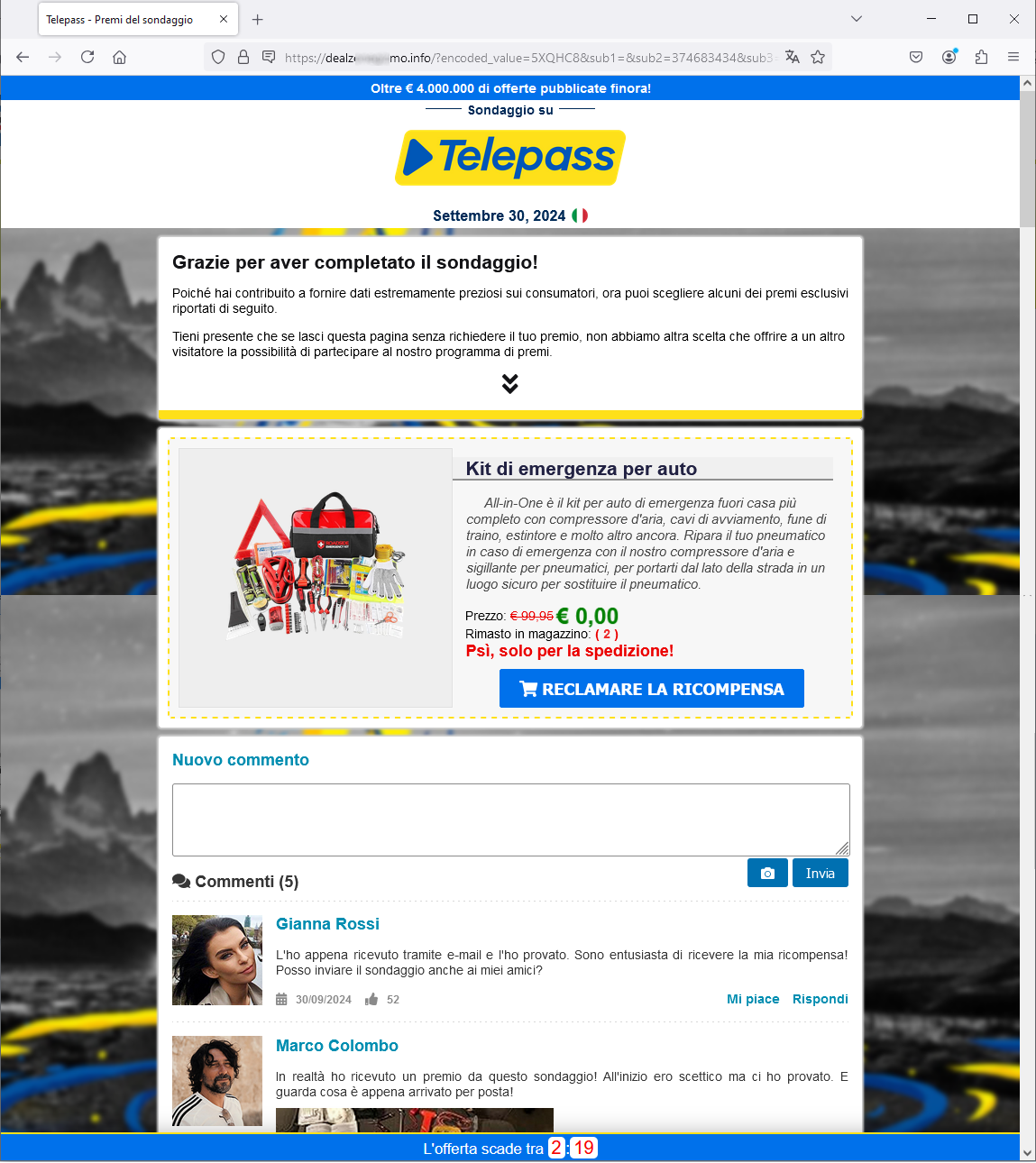
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey, by making him/her believe that only few people can win and that, in addition, the offer expires in the day. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
When we click on INIZIA IL SONDAGGIO (START THE SURVEY), we are taken to the next screens, where we are asked to answer 8 questions.
Here is specifically question 1/8. These are very general questions focused on the degree of satisfaction with the services offered by TELEPASS and about the company's marketing/promotional choices. Here, too, there is a countdown to prompt the user to quickly finish the process for the award.
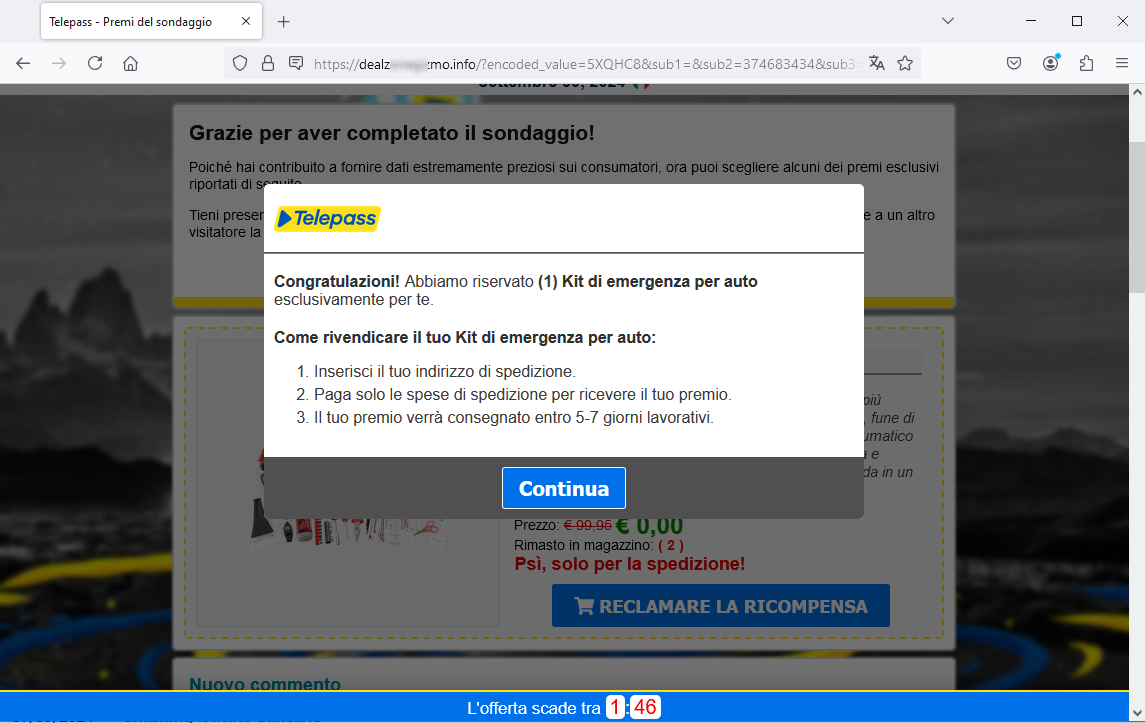
Here we go: in fact, all we need to do is to enter your shipping address and pay the shipping cost, and in 5-7 business days the prize will be delivered....
To add more credibility, many comments from customers, who supposedly participated in the survey, have been reported. These are all confirming testimonials/feedback about the actual delivery of the winnings, ensuring that it is not really a scam.....
Surely if so many users were lucky why not try our luck?!
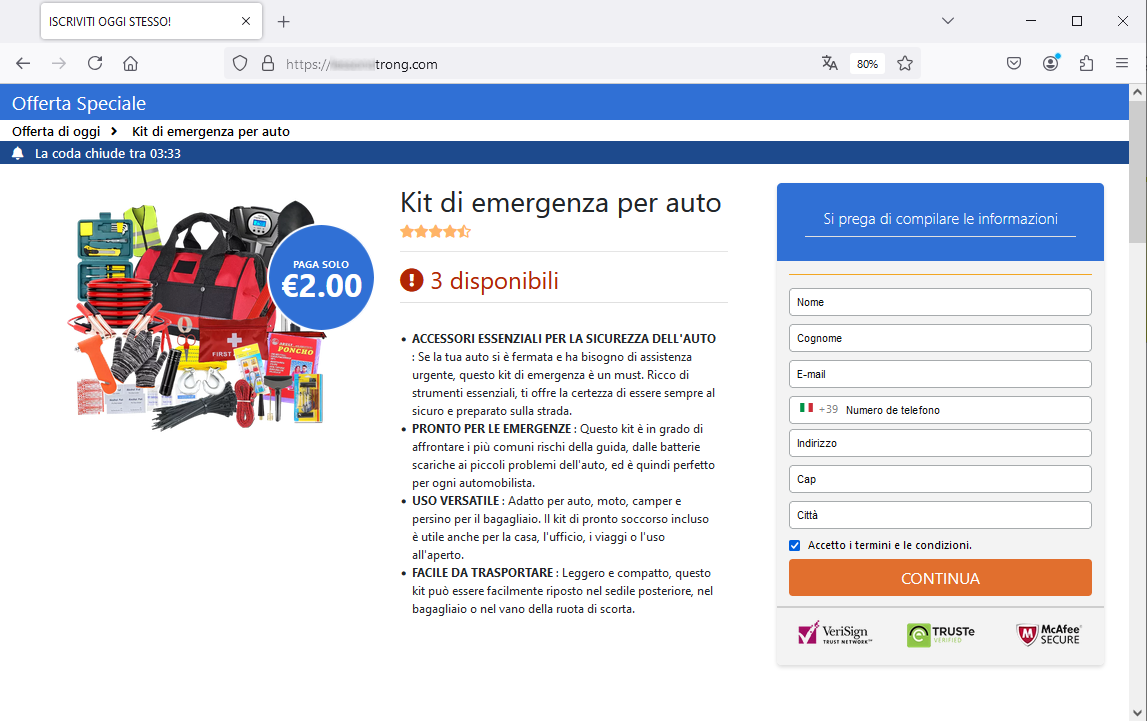
Then, when we click on Continua (Continue), we are sent to a further page to enter our shipping address and pay shipping costs.
As we can see from the image on the side, the cybercriminals try to trick the victim into entering sensitive data to ship the prize. Most likely, credit card information will also be requested later for the payment of shipping costs.
The page where we are redirected, to enter our personal data, is hosted on a new abnormal address/domain, which we report below:
https[:]//[NomeDominioFake*][.]com
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is stolen by cyber crooks, who can use them at will
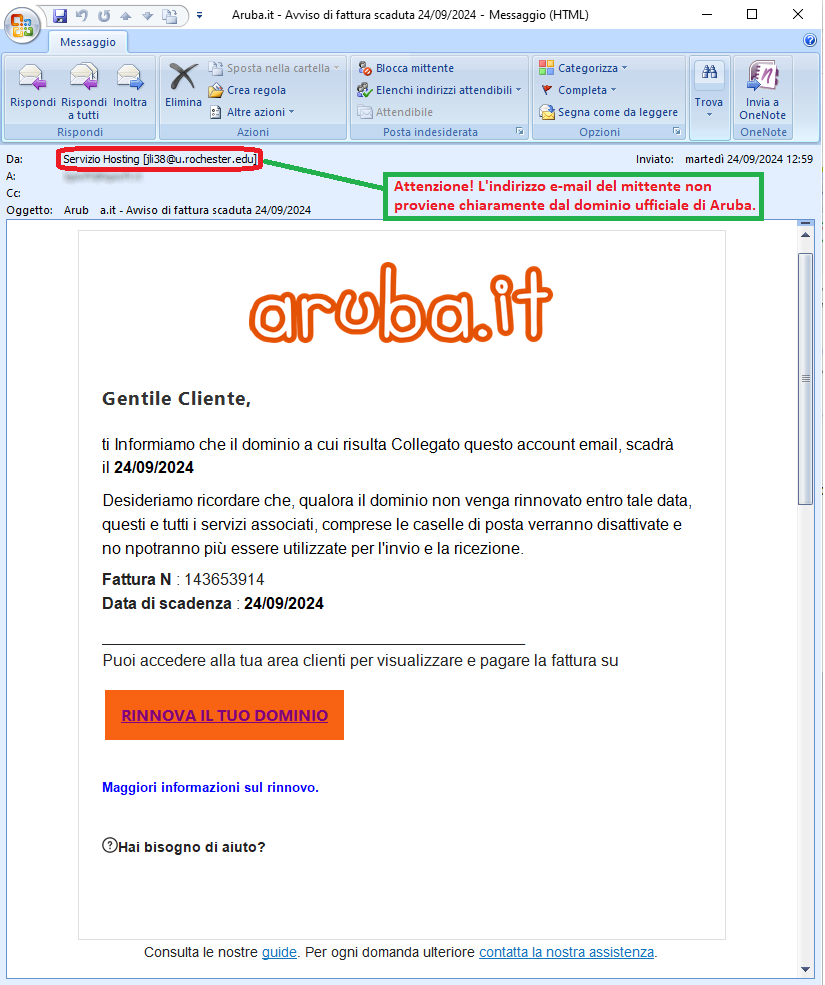
September 24, 2024 ==> Phishing Aruba - Fattura scaduta (Expired invoice)
SUBJECT: <Aruba.it - Avviso di fattura scaduta 24/09/2024> (Aruba. it - Notice of expired invoice 24/09/2024)
We find again this month several phishing attempts pretending to be communications from the Aruba brand.
The message warns the recipient that his/her domain hosted on Aruba linked to his/her e-mail account will expire on 09/24/2024. To renew all his/her services currently in use, he/she must complete the order and choose the most convenient payment method. If he/she fails to pay, all services connected to his/her account will be deactivated, including email accounts. He/she will then no longer be able to receive and send messages.
In order to pay, the user must log in through the following link:
RINNOVA IL TUO DOMINIO (RENEW YOUR DOMAIN)
Clearly, the well-known web hosting, e-mail and domain registration services company, Aruba is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
When we analyze the message, we notice right away that the sender's e-mail address <jli38(at)u(dot)rochester(dot)edu> is not from Aruba's official domain.
To induce the victim to proceed with the renewal of his/her mailbox in a timely manner, the message shows the expiration date of 24/09/2024 and gives the details of the alleged Invoice. Since the email was delivered the same day, there is not much time to renew and prevent the deactivation of services. The criminals specify a deadline for the conclusion of the procedure in order to scare the user with the fear of mailbox deactivation and push him/her to act immediately and without much thought. Anyone who unluckily clicks on the RINNOVA IL TUO DOMINIO (RENEW YOUR DOMAIN) link, will be redirected to the displayed page.
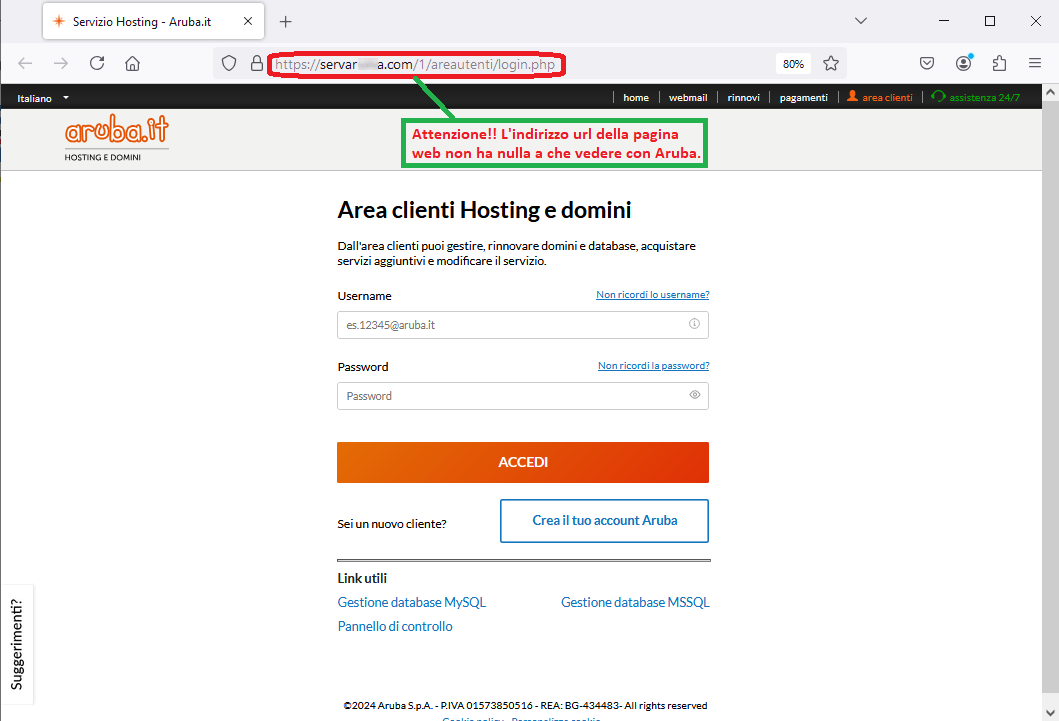
On this page, the user is invited to access his or her client area by entering a login and password to renew the domain and thus avoid the block of services related to it.
Although the site may be misleading in that the familiar Aruba logo has been included, we see that the url address on the broswer bar is anomalous and not traceable to the official domain:
https[:]//servar**a[.]com/1/areautenti/login[.]php
If we enter our data into counterfeit websites, in fact, it will be delivered to the cyber-criminals behind the scam who will use it for criminal purposes. Therefore, we urge you not to be in a hurry and remind you that, in such attempts at cyber fraud, it is necessary to pay attention to every detail, even trivial ones
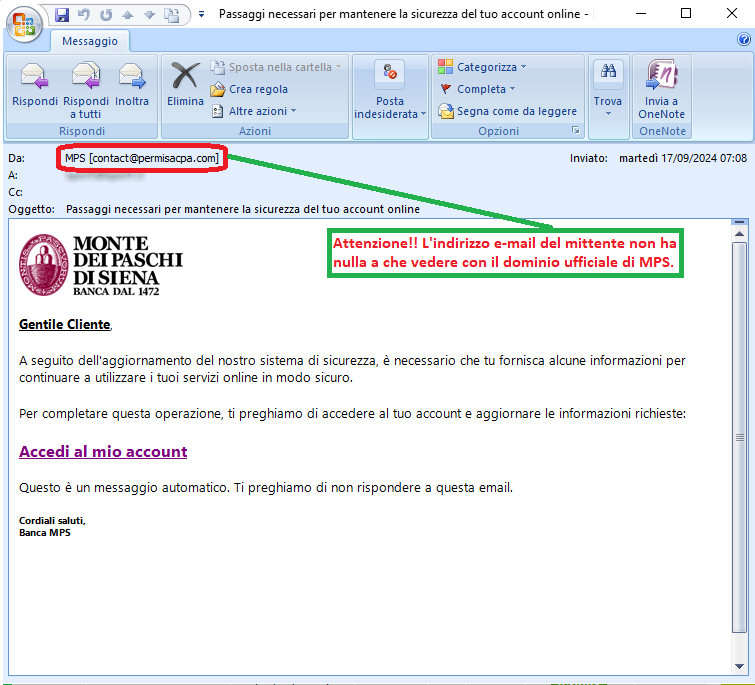
September 17, 2024 ==> Phishing Banca MPS
SUBJECT: <Passaggi necessari per mantenere la sicurezza del tuo account online> (Steps needed to maintain the security of your online account)
The short message, seemingly from Monte dei Paschi di Siena Bank, informs the recipient that following the update of their security system, it is necessary to provide some information in order to continue using online services. To complete this task, the user must log into his/her account and update the required information, by clicking on the following link:
Accedi al mio account (Log in to my account)
Clearly, Monte dei Paschi di Siena Bank is unrelated to the mass sending of these e-mails, which are scams whose goal remains, as always, to steal the home banking login credentials and/or money of the unsuspecting recipient.
Although the cyber-criminal had the foresight to insert graphics stolen from, or similar to the graphics of the well-known Bank, the message comes from an e-mail address <contact[at]permisacpa[dot]com> clearly not from the official domain of Monte dei Paschi di Siena Bank.
In fact, when we analyze the e-mail carefully, we see that the text is generic and gives no clue as to the type of information to be updated. Another anomalous fact is the request for home banking credentials through a link sent via e-mail.
Anyone who unluckily clicks on the Accedi al mio account (Log in to my account) link, will be redirected to an anomalous WEB page, which is unrelated to the Bank's official website, but which has already been reported as a DECEPTIVE WEBSITE/PAGE. In fact, it is run by cyber criminals whose goal is to get hold of your home banking login information in order to use it for criminal purposes and/or to transfer funds.
We always urge you to pay attention to even the smallest details and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as it will be sent to a remote server and used by cyber crooks.
September 15, 2024 ==> SexTortion
This month we analyze a SexTortion-themed SCAM campaign. The sender of this scam email claims to have access to the user's device. The purpose of the message is to blackmail the recipient, demanding the payment of a sum of money, in Bitcoin, in order not to divulge, among his email and social contacts, a private video of him viewing adult sites.
The following is an extract from the text of the email on the side:
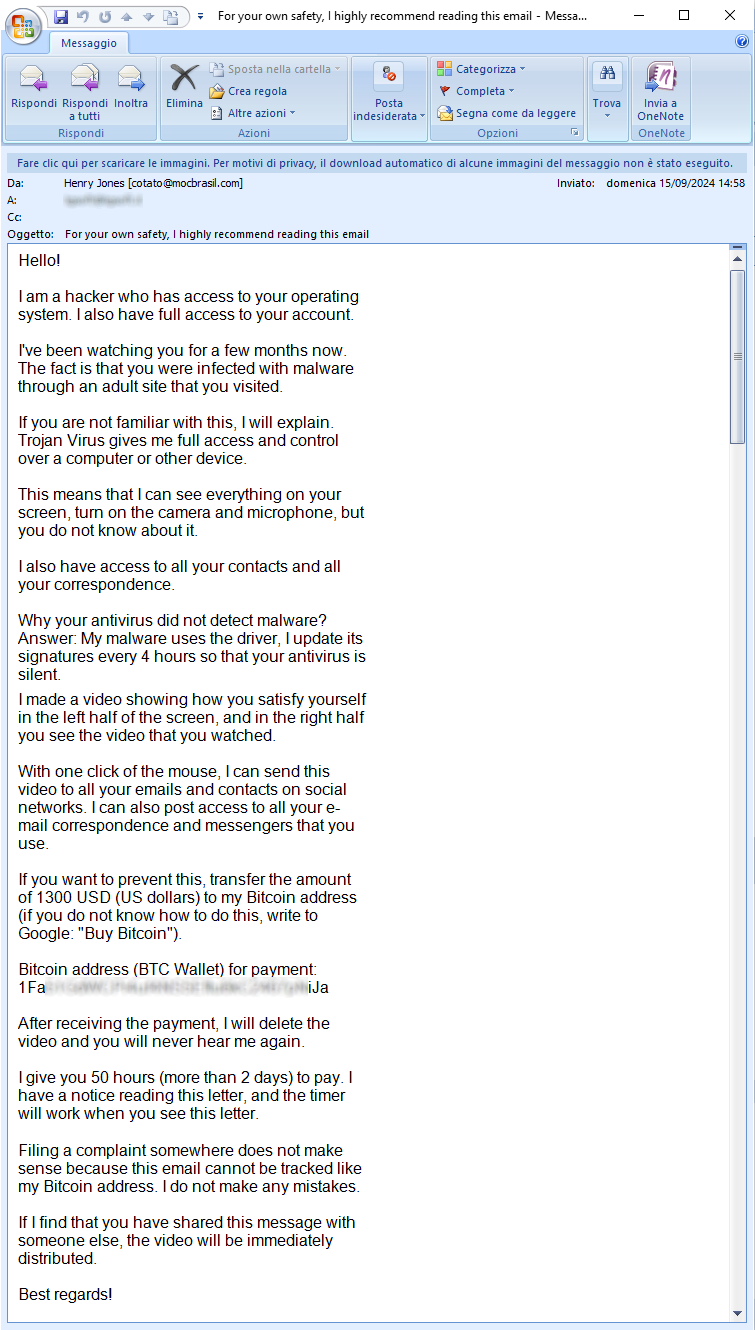 "Hello! I am a hacker who has access to your operating system. I also have full access to your account. I’ve been watching you for a few months now. The fact is that you were infected with malware through an adult site that you visited. If you are not familiar with this, I will explain. Trojan virus gives me full access and control over a computer or other device. This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it. I also have access to all your contacts and all your correspondence. Why your antivirus did not detect malware? Answer: My malware uses the driver, I update its signature every 4 hours so that your antivirus is silent. I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched. With one click of the mouse, I can send this video to all your emails and contacts on social networks. I can also post access to all your email correspondence and messengers that you use.”
"Hello! I am a hacker who has access to your operating system. I also have full access to your account. I’ve been watching you for a few months now. The fact is that you were infected with malware through an adult site that you visited. If you are not familiar with this, I will explain. Trojan virus gives me full access and control over a computer or other device. This means that I can see everything on your screen, turn on the camera and microphone, but you do not know about it. I also have access to all your contacts and all your correspondence. Why your antivirus did not detect malware? Answer: My malware uses the driver, I update its signature every 4 hours so that your antivirus is silent. I made a video showing how you satisfy yourself in the left half of the screen, and in the right half you see the video that you watched. With one click of the mouse, I can send this video to all your emails and contacts on social networks. I can also post access to all your email correspondence and messengers that you use.”
Next the victim is asked to send 1300 USD in Bitcoin to the wallet listed below: "1FaXXXXXXXXXXXXXXXXXXXXXXXiJa'. After receiving the transaction, all data will be deleted, otherwise a video depicting the user, will be sent to all colleagues, friends and relatives. The victim has 50 hours (a little more than 2 days) to make the payment!
We report transactions recorded as of 09/17/2024 on the provided wallet:
Wallet "1FaXXXXXXXXXXXXXXXXXXXXXXXiJa" amount requested 1300 USD => no transactions reported.
In such cases we always invite you:
- not to respond to these kinds of emails and not to open attachments or click unsafe links, and certainly NOT to send any money. You can safely ignore or delete them.
- if the criminal reports an actual user’s password – usually it is a password obtained from public Leaks (compromised data theft) of official sites occurred in the past (e.g., LinkedIn, Yahoo, etc.) - it is recommended to:
- Get experienced personnel to perform checks. Researchers and Analysts from the Anti Malware Research Center #CRAM of TG Soft are available to perform consultative verification activities on potentially compromised PCs / Servers;
- Only after this verification by qualified personnel experienced in spy viruses and/or malware (also new generation malware), and once you have cleaned up the machine, it is absolutely necessary to change the passwords of the web services in use on the pc
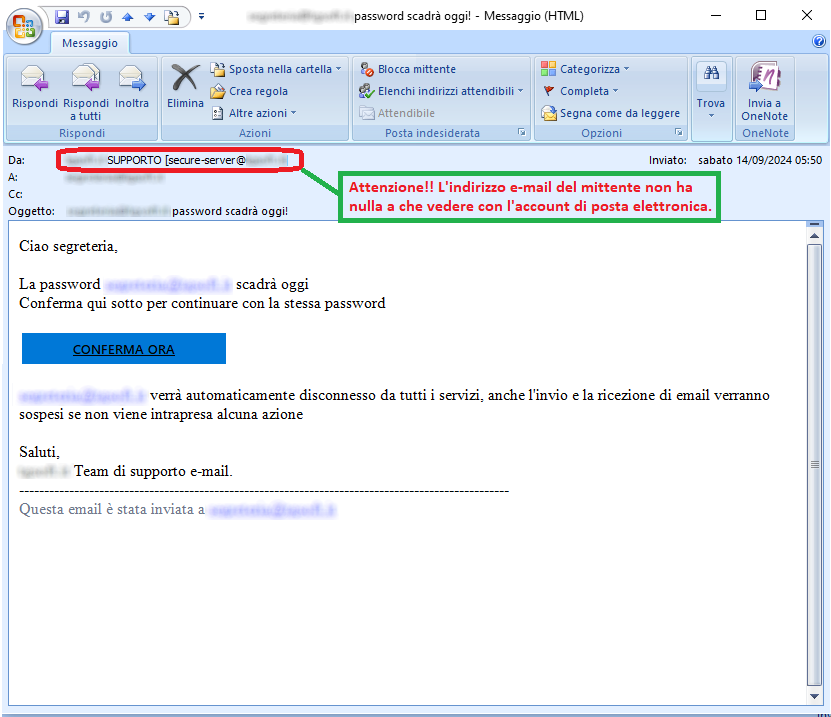
September 14, 2024 ==> Phishing Account Posta Elettronica (Email Account Phishing)
SUBJECT: <**** password scadrà oggi!> (password will expire today!)
We analyze below a new phishing attempt that aims to steal email account login credentials.
The message informs the recipient that his/her e-mail account password will expire today. It then invites him/her to confirm, in order to continue using the same password, via the following link:
CONFERMA ORA (CONFIRM NOW)
When we analyze the message, we notice that it its email address <secure- server(at)*****(dot)it> is not traceable to the domain where the email account is hosted. This is definitely anomalous and should, at the very least, make us suspicious.
Anyone who unluckily clicks on th CONFERMA ORA (CONFIRM NOW) link, will be presented with the screen shown in the side image.
As we can see, the site graphically simulates the Webmail login page, where we are requested to enter login information. However, the address is clearly anomalous.
On the basis of these remarks we warn you to NEVER enter your credentials on sites whose origin you do not know, as they will be sent to a remote server and used by cyber crooks, with all the associated, easily imaginable, risks.
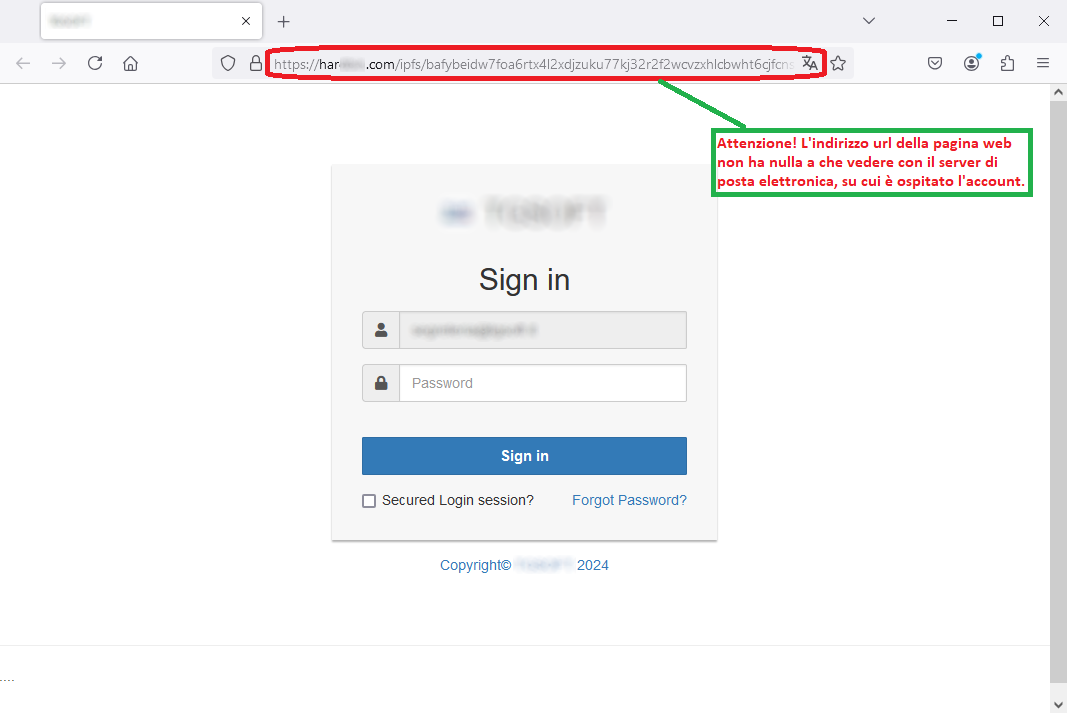
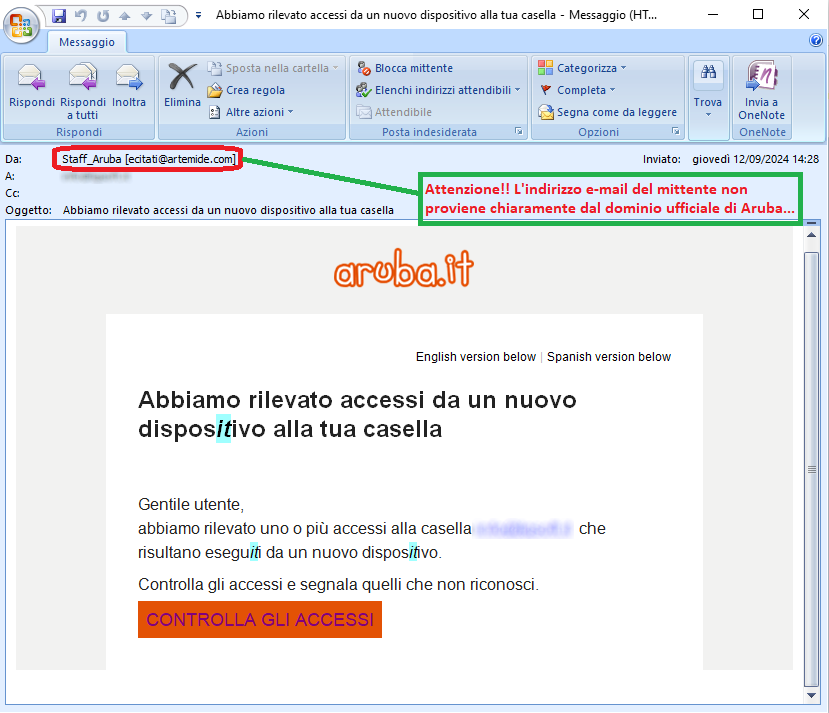
September 12, 2024 ==> Phishing Aruba - Accesso non riconosciuto (Unrecognized Access)
SUBJECT: <Abbiamo rilevato accessi da un nuovo dispositivo alla tua casella>(We detected accesses from a new device to your box)
We find again this month phishing attempts pretending to be communications from the Aruba brand. The message informs the recipient that unknown access from a new device has been detected to his or her e-mail box. He/She is then asked to verify the accesses and report the unknown ones through the following link:
CONTROLLA GLI ACCESSI (CONTROL ACCESS)
Clearly, the well-known web hosting, e-mail and domain registration services company Aruba is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
When we analyze the message, we notice right away that the sender's e-mail address <ecitati[at]artemide[dot].com> is not from Aruba's official domain.
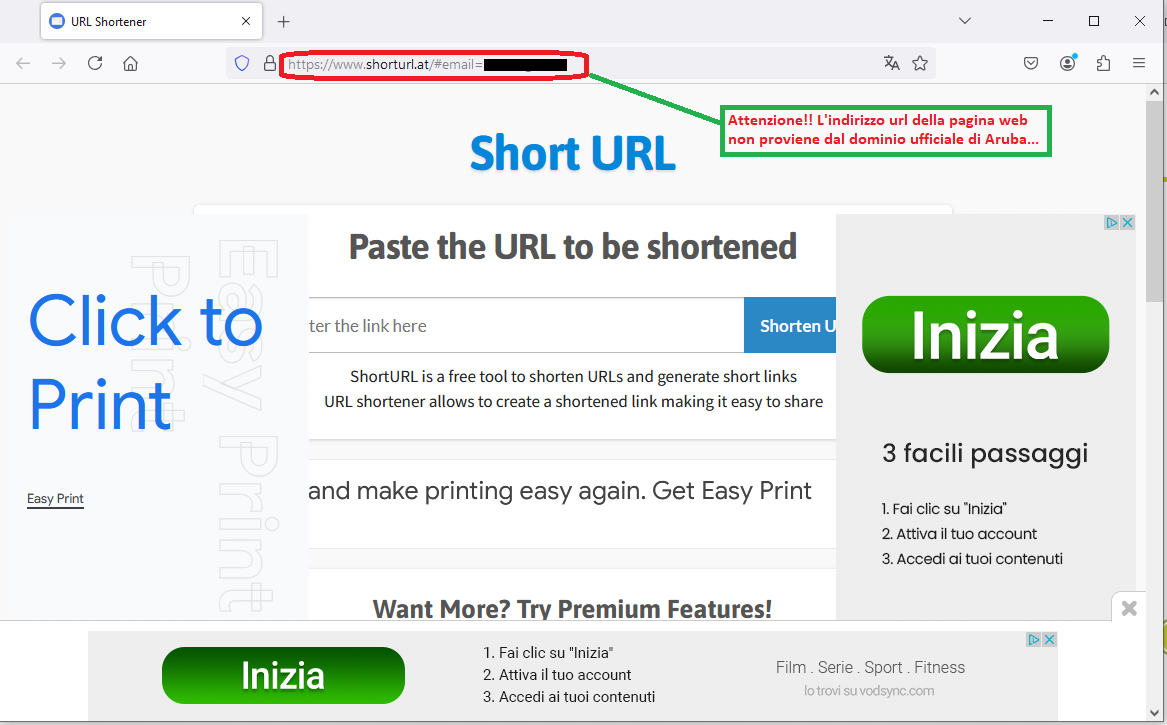
Anyone who unluckily clicks on the CONTROLLA GLI ACCESSI (CONTROL ACCESS) link, will be redirected to the displayed page.
As we can see from the side image we are redirected to a web page unrelated to the site of Aruba. The url address on the broswer bar is anomalous and not traceable to the official domain:
https[:]//www.shorturl[.]at/#google_vignette...If we enter our data into counterfeit websites, in fact, it will be delivered to the cyber-criminals creators of the scam who will use it for malicious purposes. Therefore, we urge you not to rush and remember that in case of these cyber fraud attempts, we must pay attention to every detail, even trivial ones.
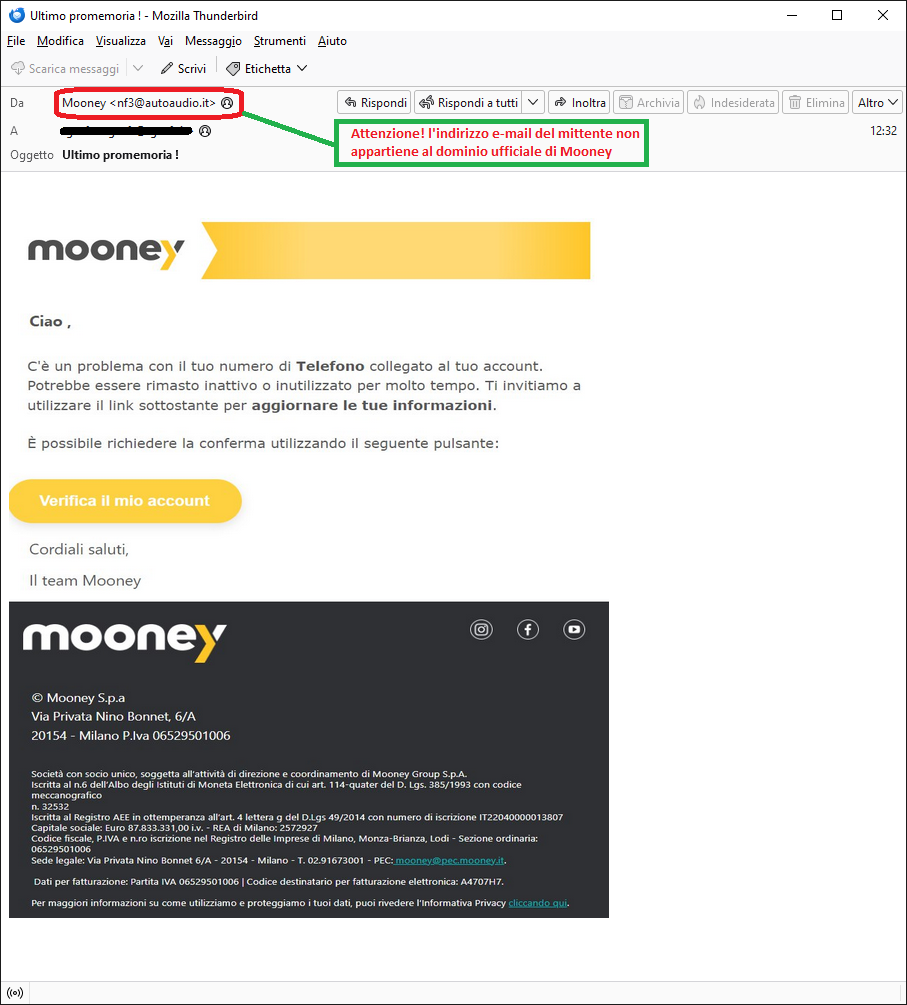
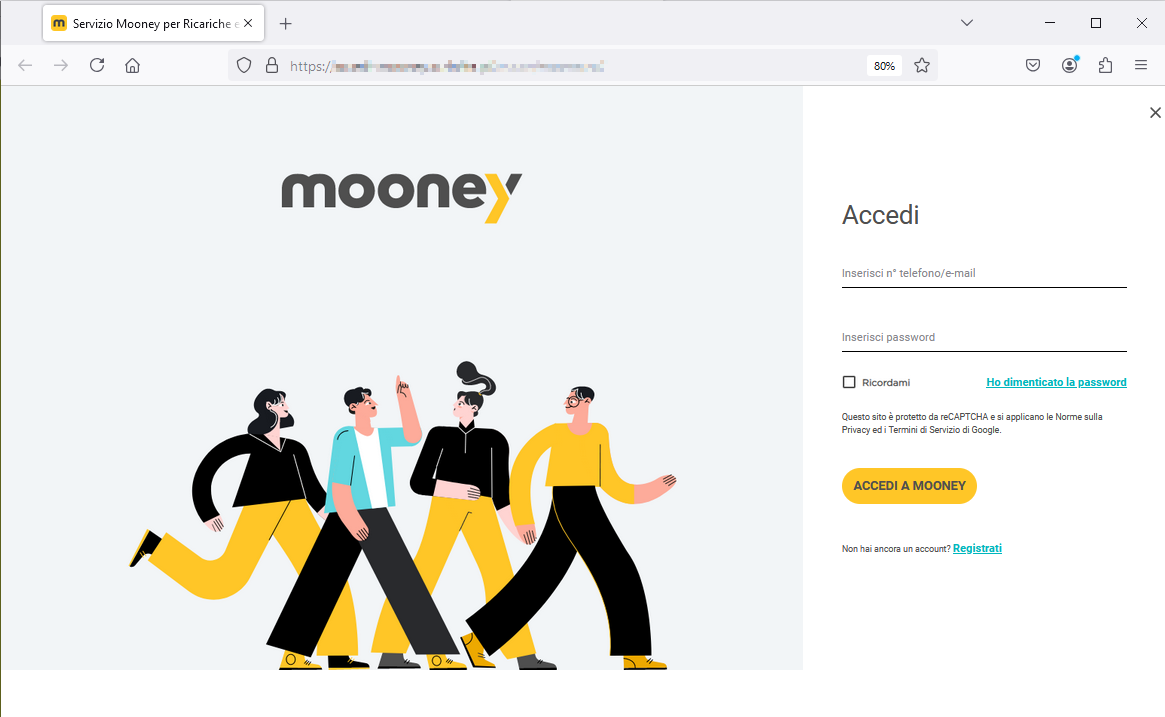
September 12, 2024 ==> Phishing Mooney
SUBJECT: <Ultimo promemoria!> (Last reminder!)
We analyze below a phishing attempt pretending to be a communication from Mooney, a well-known Italian Proximity Banking & Payments company. The message informs the recipient that there is a problem with the phone number linked to his or her account because it may not have been used for a long time, and so it is necessary to update the information.
The user is then invited to use the following link:
Verifica il mio account (Verify my account)
Clearly, the well-known Italian online payment company Mooney, is unrelated to the mass sending of these emails, which are real scams whose goal remains, as always, to steal the sensitive data of the unsuspecting recipient.
Although the cyber crook used graphics similar to or stolen from Mooney's, and took care to include the real company's data - so as to fool an unwary user - we should always exercise caution before clicking on suspicious links.
In fact, when we analyze the message, we immediately notice that the sender's e-mail address cannot be traced back to Mooney's official domain. Another anomalous fact is the request to update account data through a link sent by e-mail.
Anyone who unluckily clicks on the Verifica il mio account (Verify my account) link, will be redirected to an anomalous WEB page unrelated to Mooney's official site.
On this page, the user is prompted to log in to their restricted area by entering their account login and password.
Although the site may be misleading because of its Mooney-like graphics, the url address on the browser bar is anomalous and not traceable to the official domain.
Therefore, we urge you to always pay close attention, even to the smallest details, and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as it will be sent to a remote server and used by cyber crooks.
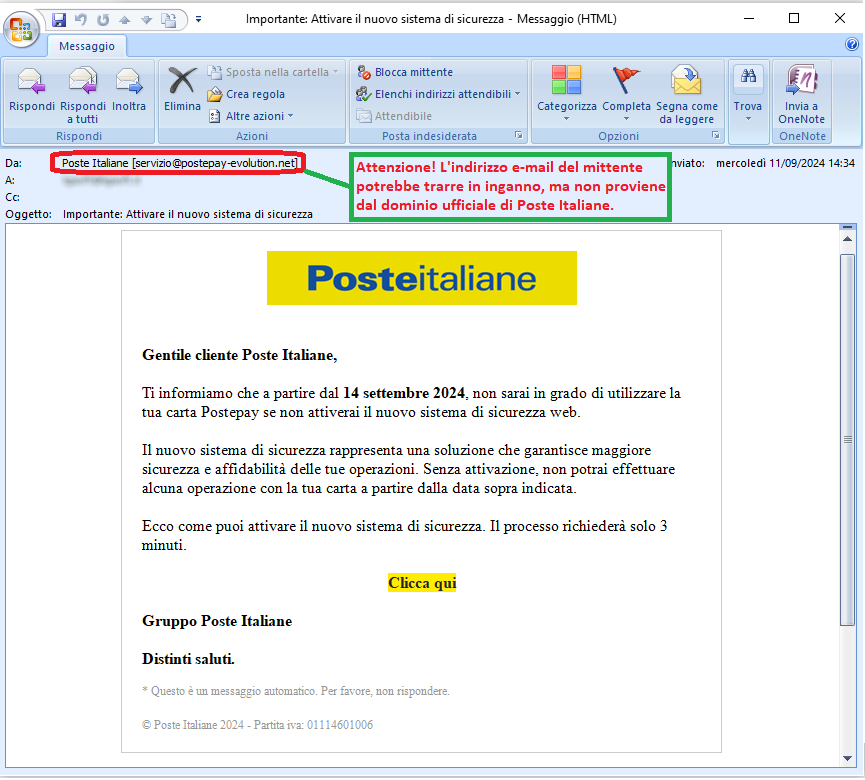
September 11, 2024 ==> Phishing PosteItaliane
SUBJECT: <Importante: Attivare il nuovo sistema di sicurezza> (Important: Enable the new security system)
We find again this month the phishing attempt behind a false message from PosteItaliane, concerning the notification of a new security system.
The message, which we reproduce on the side, is addressed to PosteItaliane customers owning Postepay cards, and requires them to activate the new web security system by September 14, 2024 for greater security and reliability in transactions. Without activation of the security system, users will not be able to use their card. Activation takes only 3 minutes using the following link:
Clicca qui (Click here)
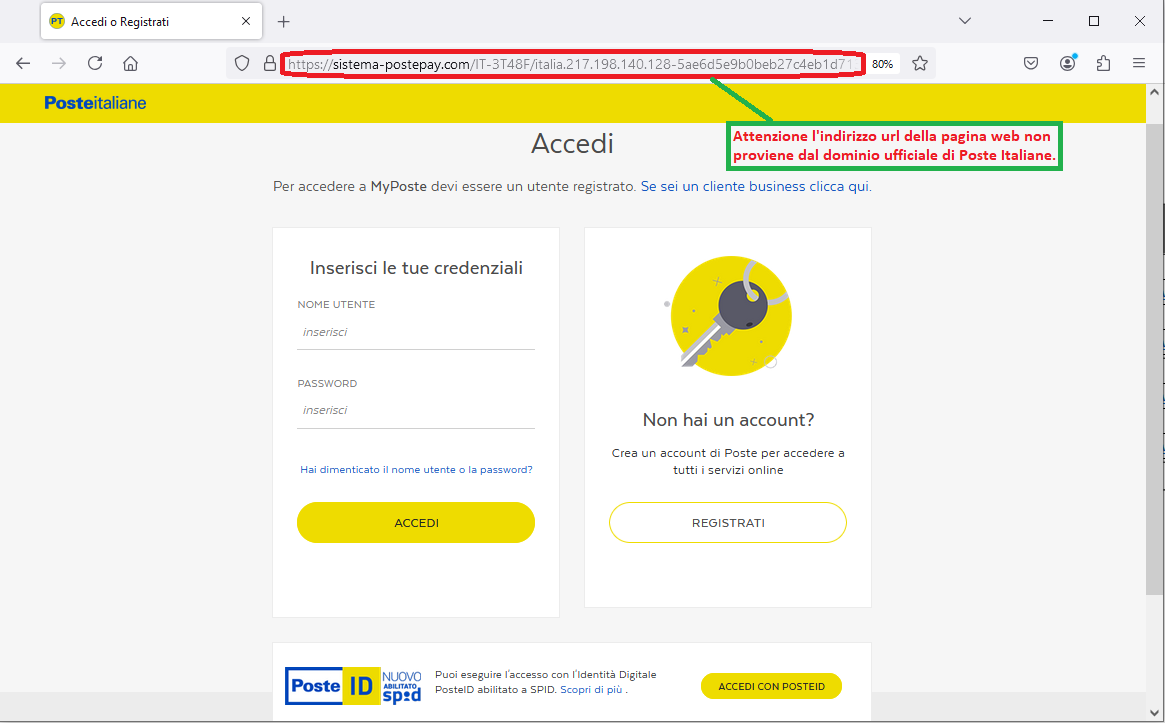
The message seems to come from PosteItaliane but the email is rather generic and addresses an unspecified Gentile cliente (Dear Customer). In addition, it comes from an e-mail address <service[at]postepay-evolution[dot]net> that is clearly not from the official domain of PosteItaliane. The purpose is obviously to lead the user to click on the provided link, which redirects to a web page requesting customer data
The link sends us to a web page that is supposed to simulate the official site of PosteItaliane. Although the site may be misleading due to the presence of the well-known PosteItaliane logo, we notice that the url address on the broswer bar is anomalous and not traceable to PosteItaliane:<<https[:]//sistema-*****[.]com/IT-3T48F/italia.217.198.14...>>
To conclude, we always urge you to be wary of any email that asks you to enter confidential data, and avoid clicking on suspicious links, which could lead to a counterfeit site difficult to distinguish from the original one. In fact in this way cyber crooks can steal your most valuable data use it at will.
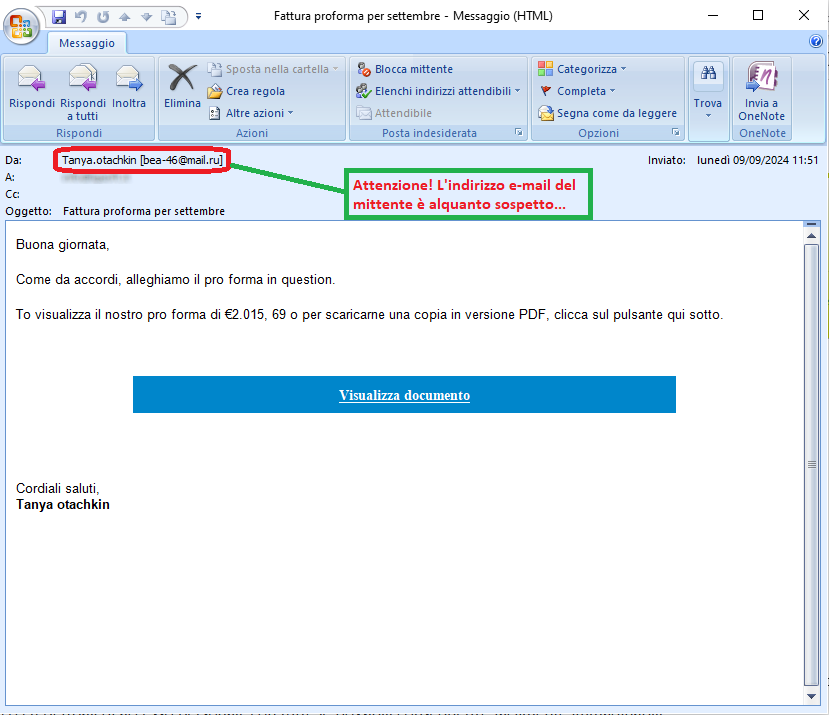
September 09, 2024 ==> Phishing Webmail
SUBJECT: <Fattura proforma per settembre> (Proforma invoice for September)
We analyze below a phishing attempt concerning a fake sales invoice from an unidentified supplier.
The message informs the recipient that the proforma he or she was waiting for - concerning an alleged order in the amount of 2,015.69 Euros - is available, and he or she can download it in pdf format by clicking on the following link:
Visualizza documento (View document)
When we analyze the email, we notice that the message contains several grammatical and lexical errors and is very generic. In the signature, the name of a certain "Tanya otachkin" is mentioned.
In these cases we can easily realize that it’s a scam message, as we have no relation to the person in the signature. If we are not waiting for proforma invoices of unmade orders, we should always be careful and pay attention to the other alarm bells of these scam attempts, including - as already reported - syntax/lexical errors, suspicious sender's e-mail address and generic e-mails.
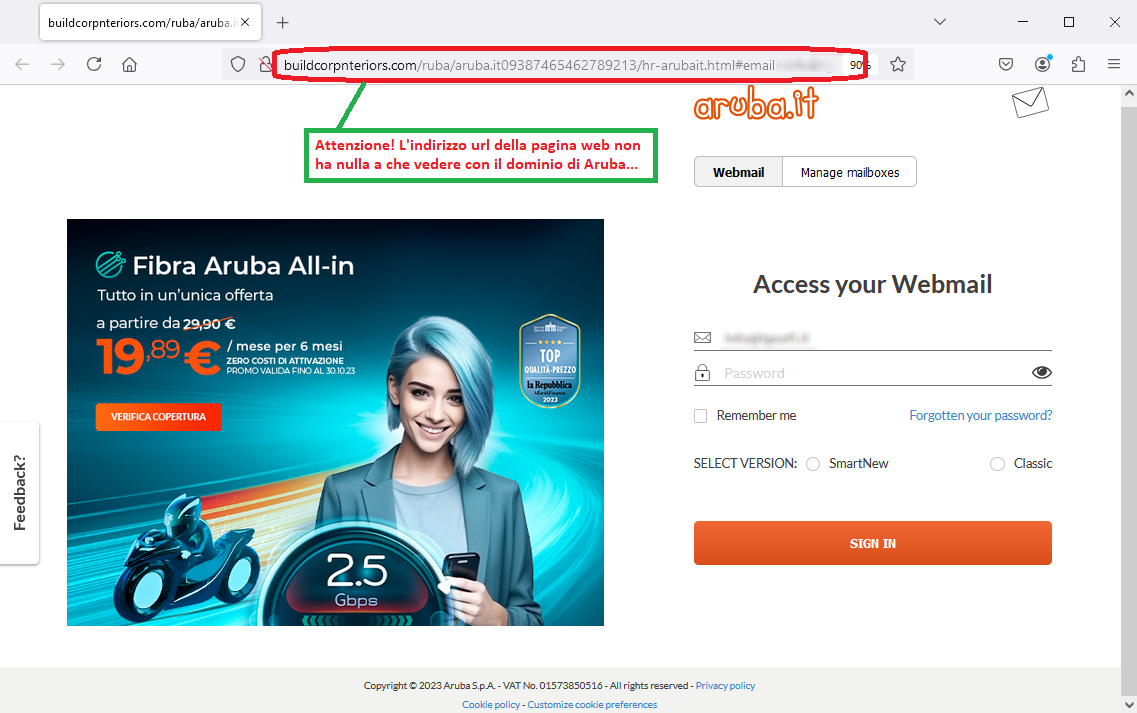
Anyone who unluckily clicks on the Visualizza documento (View document) link, will be redirected to an anomalous WEB page, which simulates the official website of Aruba.
On this page, the user is invited to log into his or her account by entering a login and password, to download the alleged proforma submitted.
However, the page for Aruba credentials entry is hosted on an anomalous address/domain, which we report below:
https[:]//buildcorpnteriors[.]com/ruba/aruba[.]it09387465462789213....
We always urge you to pay attention to every detail, even trivial ones, and not to enter your personal data and/or passwords on forms hosted on counterfeit web pages, as it will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
September 07, 2024 ==> Smishing Istituto Bancario (BANK)
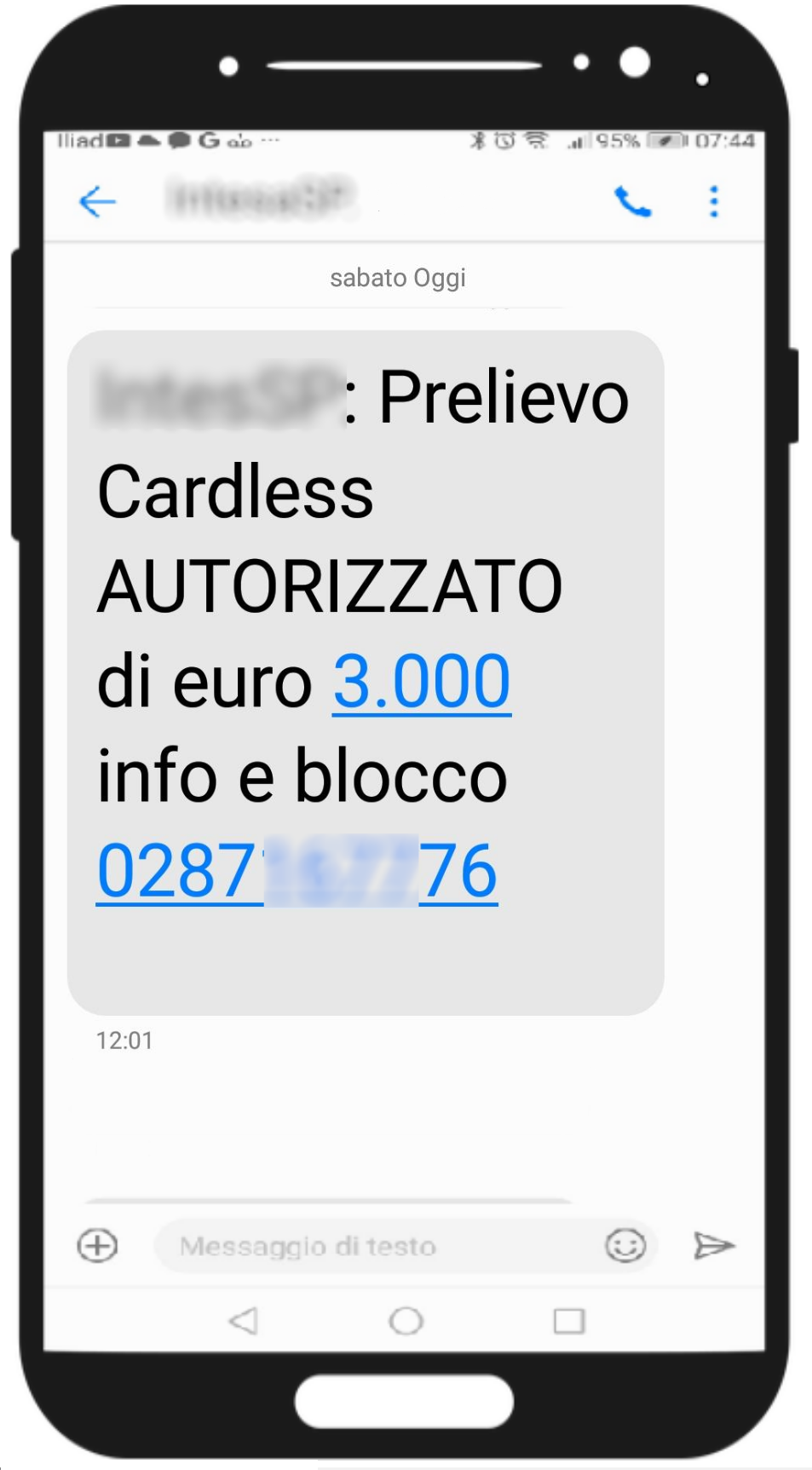
We analyze below a false communication from a well-known Bank spread through sms (smishing), a type of phishing that uses cell phones instead of email.
The message notifies the recipient of an authorized cardless withdrawal of Euro 3,000.00. A telephone number is then given for information about the transaction and the block of the operation.
Clearly, if the recipient of the text message is not actually a customer of the Bank, the anomaly of the message is more obvious. In any case, we remind you that under no circumstances Banks require customers to provide personal data - especially home banking login credentials - via SMS and e-mail.
The purpose of the message is to lead the user, alarmed by the report of the unknown withdrawal, to promptly call the given number 0287****76.
The scammer's goal is to get the victim to contact him or her by phone and, posing as the bank operator, issue instructions in order to steal the victim's bank account and/or credit card information.To conclude, we always urge you to be wary of any message (via e-mail or text message) asking to click on suspicious links or call phone numbers. In case of doubt we recommend you to contact the official numbers/channels of your bank.
It is crucial to remember not to provide or even enter your bank account login information, credit card information or other personal data for any reason unless you are certain of the website's origin. Otherwise you deliver your most valuable data to cyber crooks who can use it at will.
September 06, 2024 ==> Phishing Aruba - Accesso non riconosciuto (Unrecognized Access)
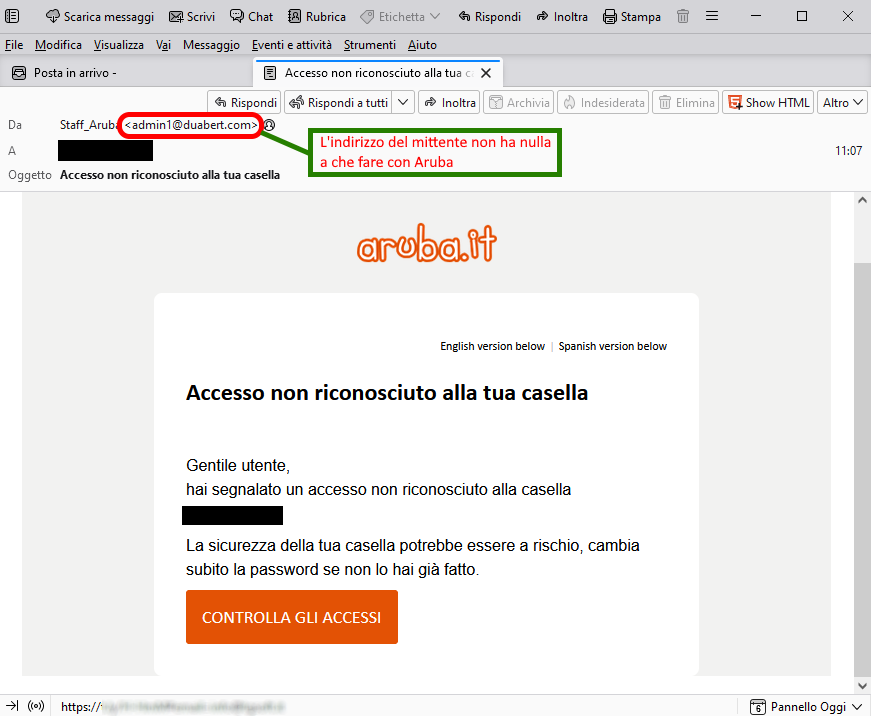
SUBJECT: <Accesso non riconosciuto alla tua casella> (Unrecognized access to your mailbox)
We find again this month several phishing attempts pretending to be communications from the Aruba brand.
The message informs the recipient that unknown access has been detected to his or her email box (supposedly on Aruba) and that the security of the box may be at risk. It therefore seems necessary to change the password promptly.
The user is thus asked to change his/her password, via the following link:
CONTROLLA GLI ACCESSI (Control Access)
Clearly, the well-known web hosting, e-mail and domain registration services company Aruba is unrelated to the mass sending of these e-mails, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient.
When we analyze the message, we notice right away that the sender's e-mail address <admin1[at]duabert[dot].com> is not from Aruba's official domain.
Anyone who unluckily clicks on the CONTROLLA GLI ACCESSI (Control Access) link, will be redirected to the displayed page.
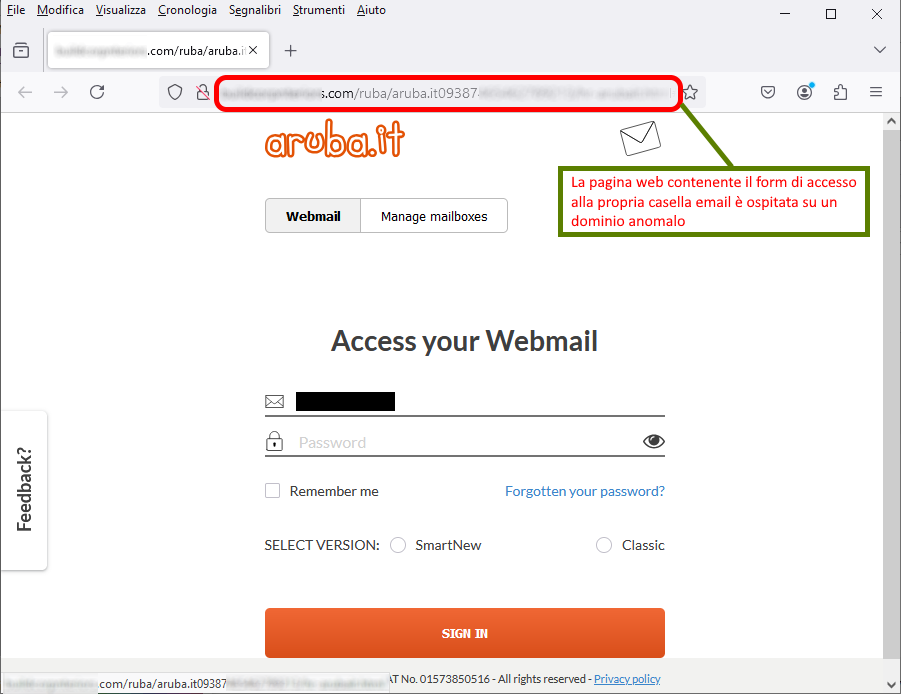
On this page the user is asked to log in to his or her client area by entering, most importantly, the password. Then we expect that by clicking SIGN IN we will be able to change the current password as requested in the initial message.
Although the site may be misleading in that the well-known Aruba logo has been included, the url address on the broswer bar is anomalous and not traceable to the official domain:
[NomeDominioFake*]...*FakeDomainName is a domain that simulates a known brand domain or is a randomly named domain.
If you enter your data into counterfeit websites, it will be delivered to the cyber-criminals creators of the scam, who will use it for criminal purposes. Therefore, we urge you not to rush and we to pay attention to every detail, even trivial ones, to avoid such attempts at cyber fraud.
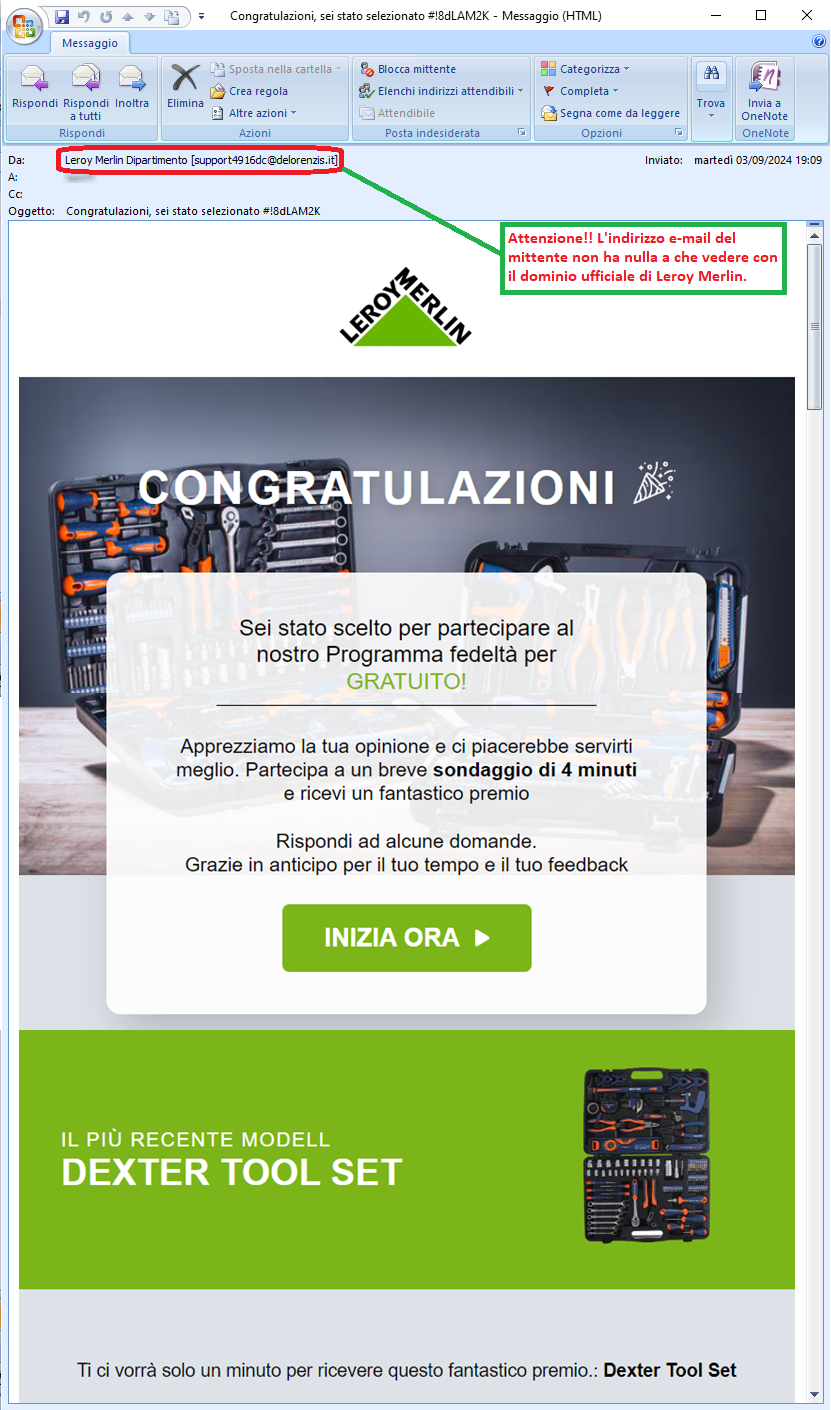
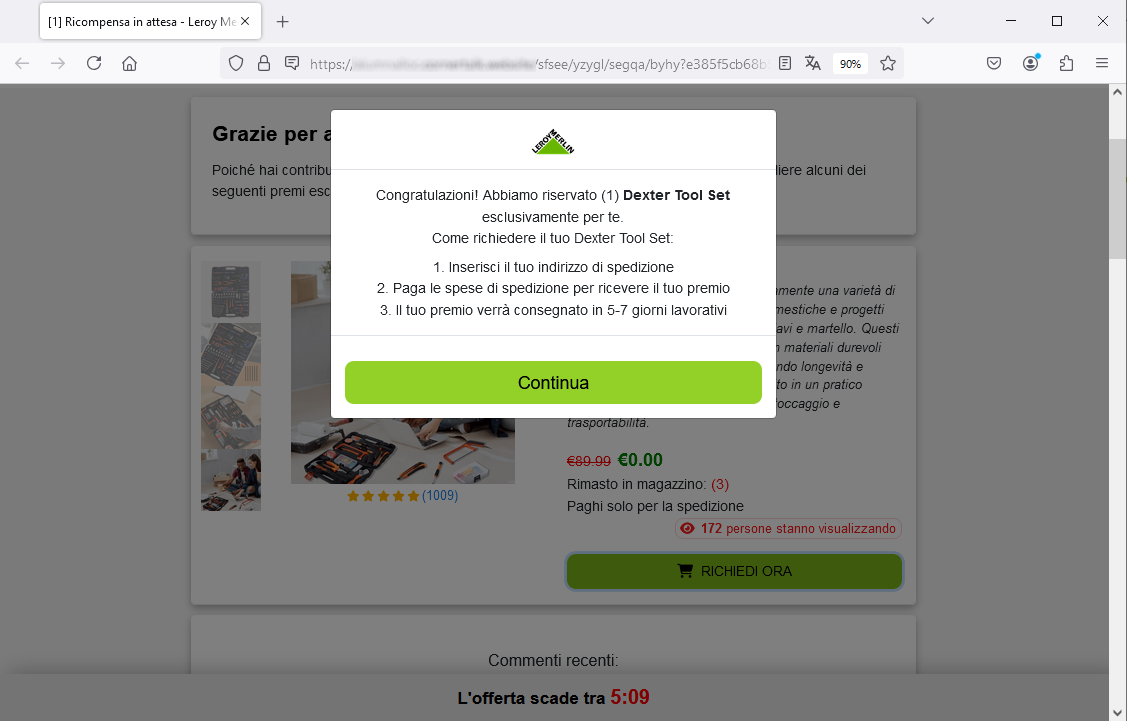
September 06, 2024 ==> Phishing Leroy Merlin
SUBJECT: <Congratulazioni, sei stato selezionato #!8dLAM2K> (Congratulations, you have been selected #!8dLAM2K)
Below we analyze the following scam attempt hidden behind a false communication from Leroy Merlin, the well-known large distribution company.
This is a promotional message that seems to propose an unmissable opportunity. The lucky user has been selected to participate in a free loyalty program through a survey that will allow him or her to win a prize: a Dexter Tool Set...or so it seems.
Certainly behind this phishing there is a real decoy for many inexperienced users.
Clearly Leroy Merlin is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient. So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
When we analyze the email, we notice that the message comes from an email address <support4916dc[at]delorenzis[dot]it> not traceable to the official domain of Leroy Merlin. This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the link provided, here is what happens:
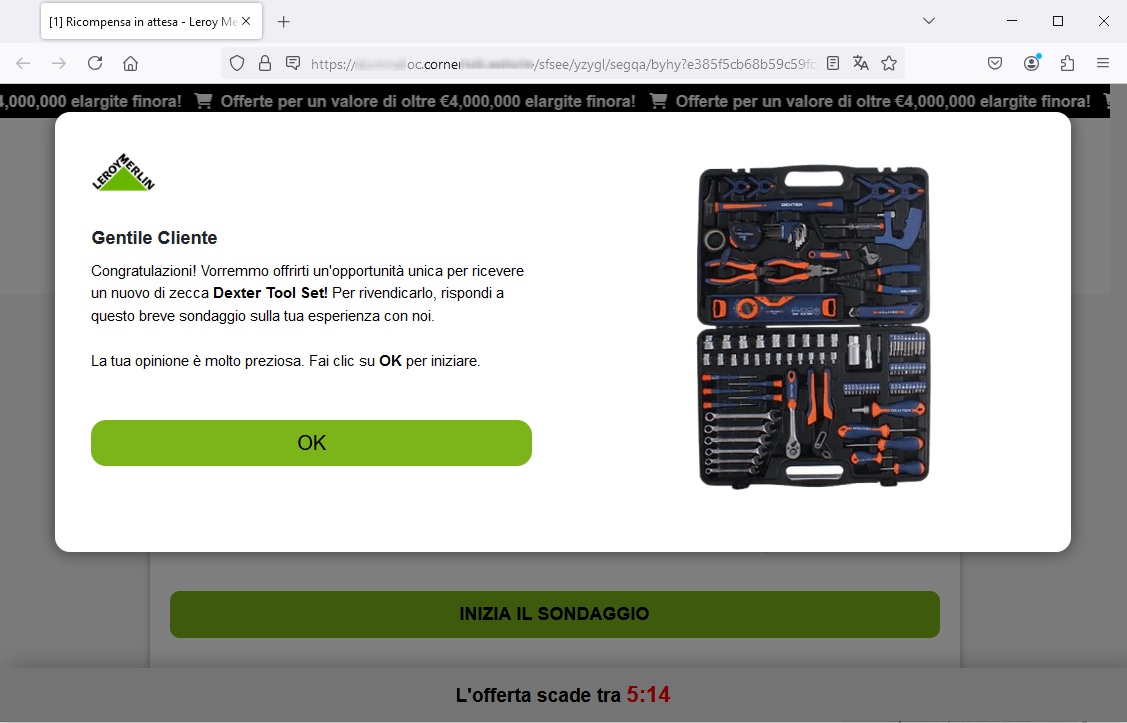
we are redirected to a landing page that, although graphically well designed (with misleading images and the authentic logo of Leroy Merlin) does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on the following anomalous address/domain:
[NomeDominioFake*]...
*FakeDomainName is a domain that simulates a known brand domain or is a randomly named domain.
which has no connection with Leroy Merlin.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey, by making him/her believe that only few people can win, and the offer expires in the day. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
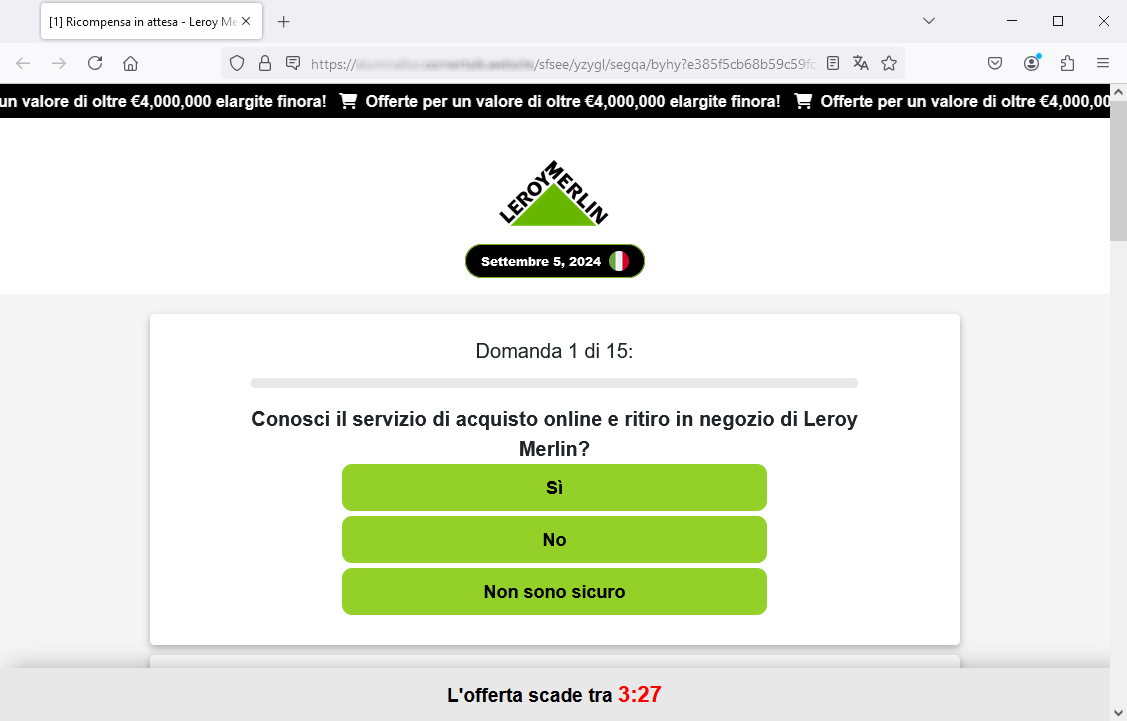
When we click on OK, we are taken to the next screens, where we are asked to answer 15 questions.
Here is specifically question 1/8. These are very general questions focused on the degree of satisfaction with the services offered by Leroy Merlin and on the daily habits of consumers. Here, too, there is a countdown to prompt the user to quickly finish the process for the award.
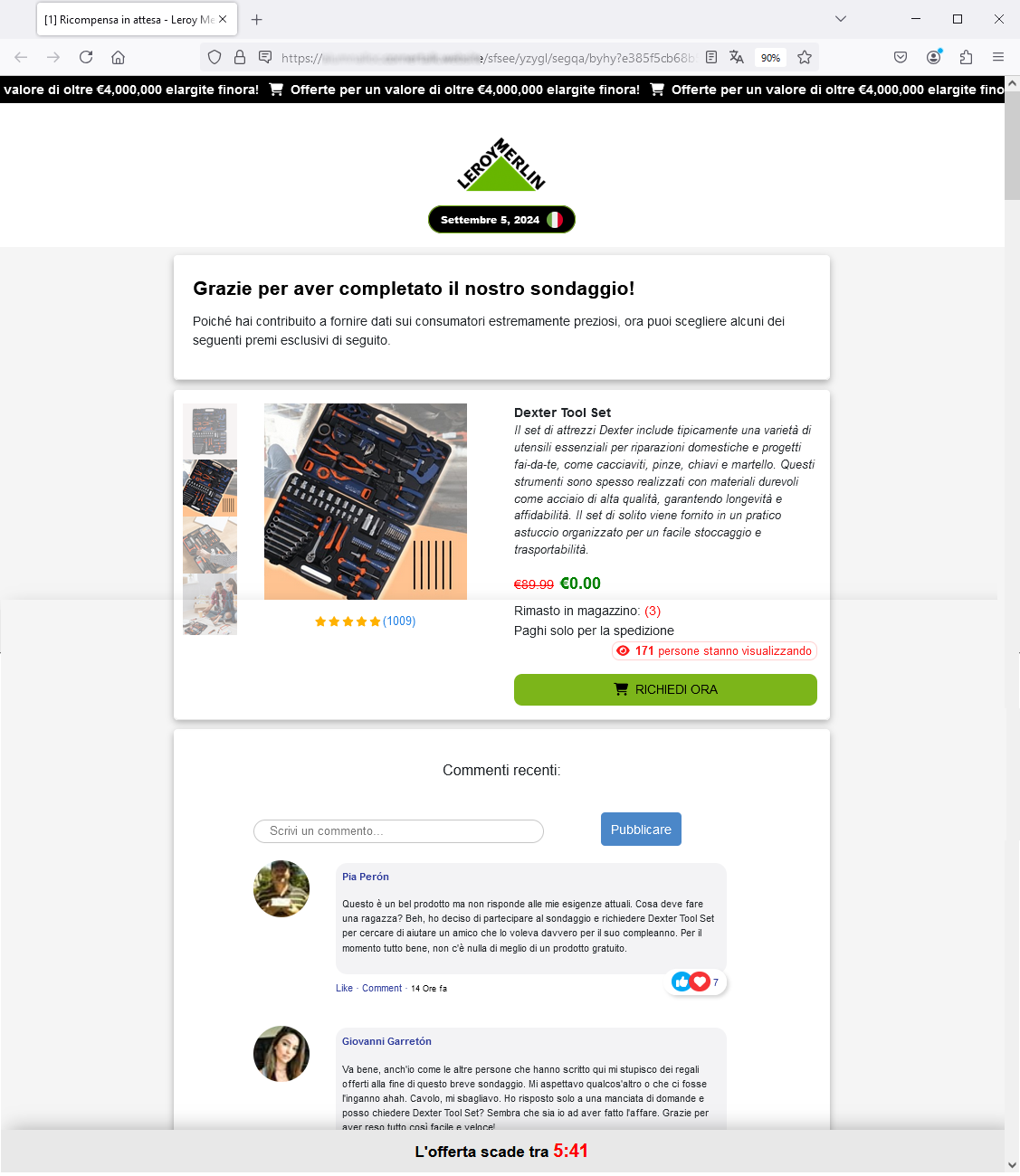
Here we go: in fact, all we need to do is to enter our shipping address and pay the shipping cost, and in 5-7 business days the prize will be delivered....
To make the scam more trustworthy, several comments have been reported from customers who seem to have already participated in the survey. These are all reassuring testimonials/feedback about the actual delivery of the winnings and thus on the reliability of the message.
Certainly if so many users were lucky why not try your luck?!
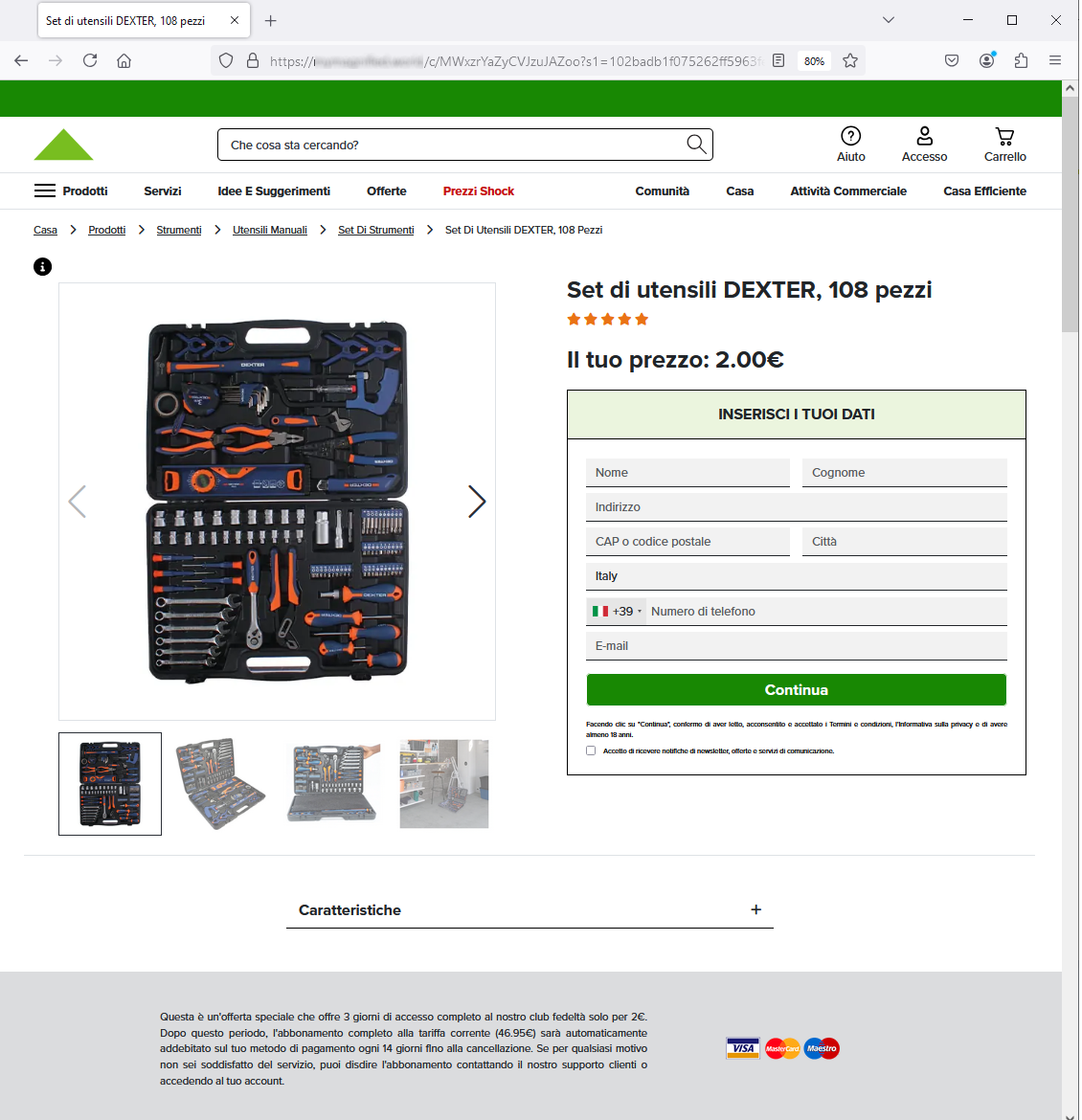
Then, when we click on Continua (Continue), we are sent to a further page to enter our shipping address and pay shipping costs.
As we can see from the image on the side, the cybercriminals try to trick the victim into entering sensitive data to ship the prize. Most likely, credit card information will also be requested later for the payment of shipping costs.
The page where we are redirected, to enter our personal data, is hosted on a new abnormal address/domain, which we report below:
[NomeDominioFake*]
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data is placed in the hands of cyber crooks who can use it at will.
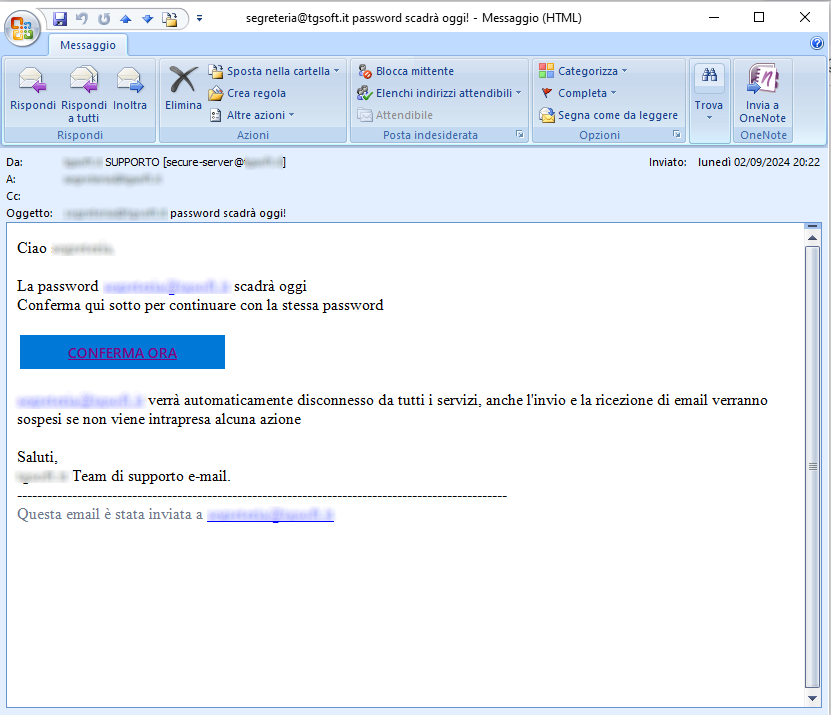
September 02, 2024 ==> Phishing Account Posta Elettronica (Phishing Email Account)
SUBJECT: <**** password scadrà oggi!> (**** password will expire today!)
We analyze below a new phishing attempt that aims to steal email account login credentials.
The message informs the recipient that his e-mail account password will expire today. It then invites him/her to confirm his/her password to continue using the same password, through the following link:
CONFERMA ORA (CONFIRM NOW)
When we analyze the email, we see that the message comes from an email address <secure-server(at)*****(dot)it> not traceable to the domain of the email account. This is definitely anomalous and should, at the very least, make us suspicious.
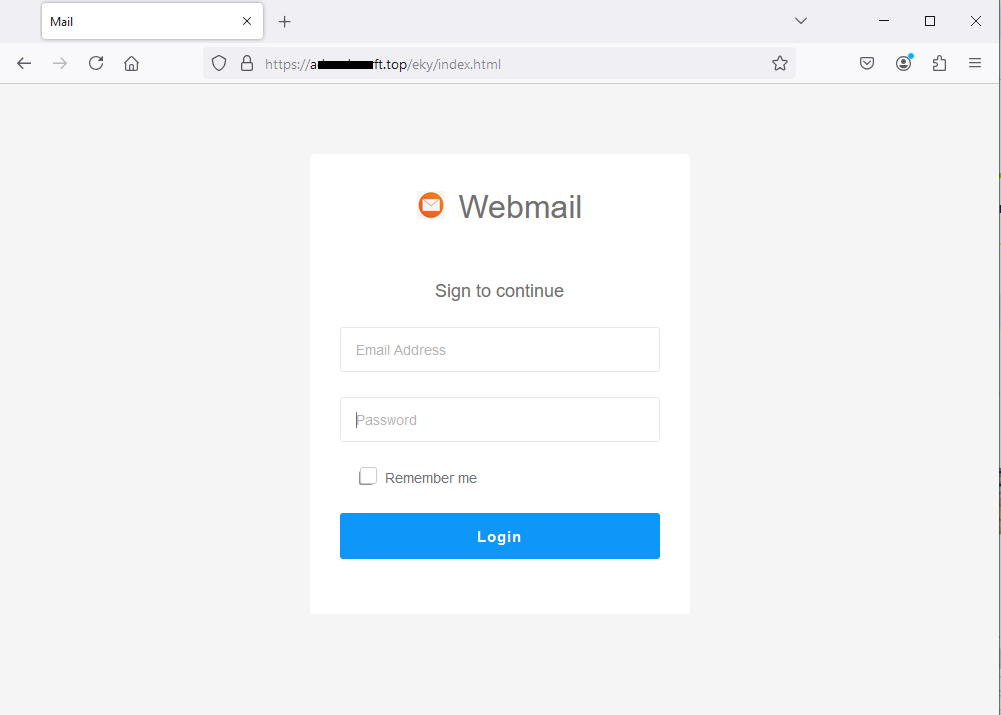
Anyone who unluckily clicks on the CONFERMA ORA (CONFIRM NOW) link, will be presented with the screen shown in the side image.
As we can see, the user is directed to a site that graphically simulates the Webmail login page-which, however, is hosted on an anomalous address/domain-where he is required to enter his login information.
Based on these considerations, we urge you to NEVER enter your credentials on unverified sites, as they will be sent to a remote server and used by cyber crooks with all the associated, easily imaginable, risks.
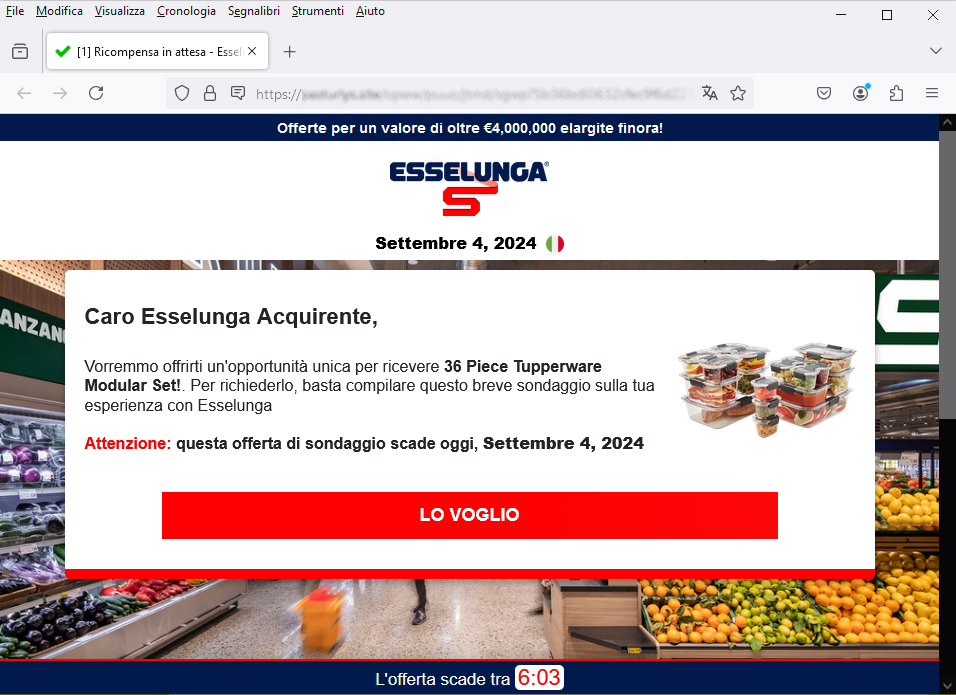
September 02, 2024 ==> Phishing ESSELUNGA
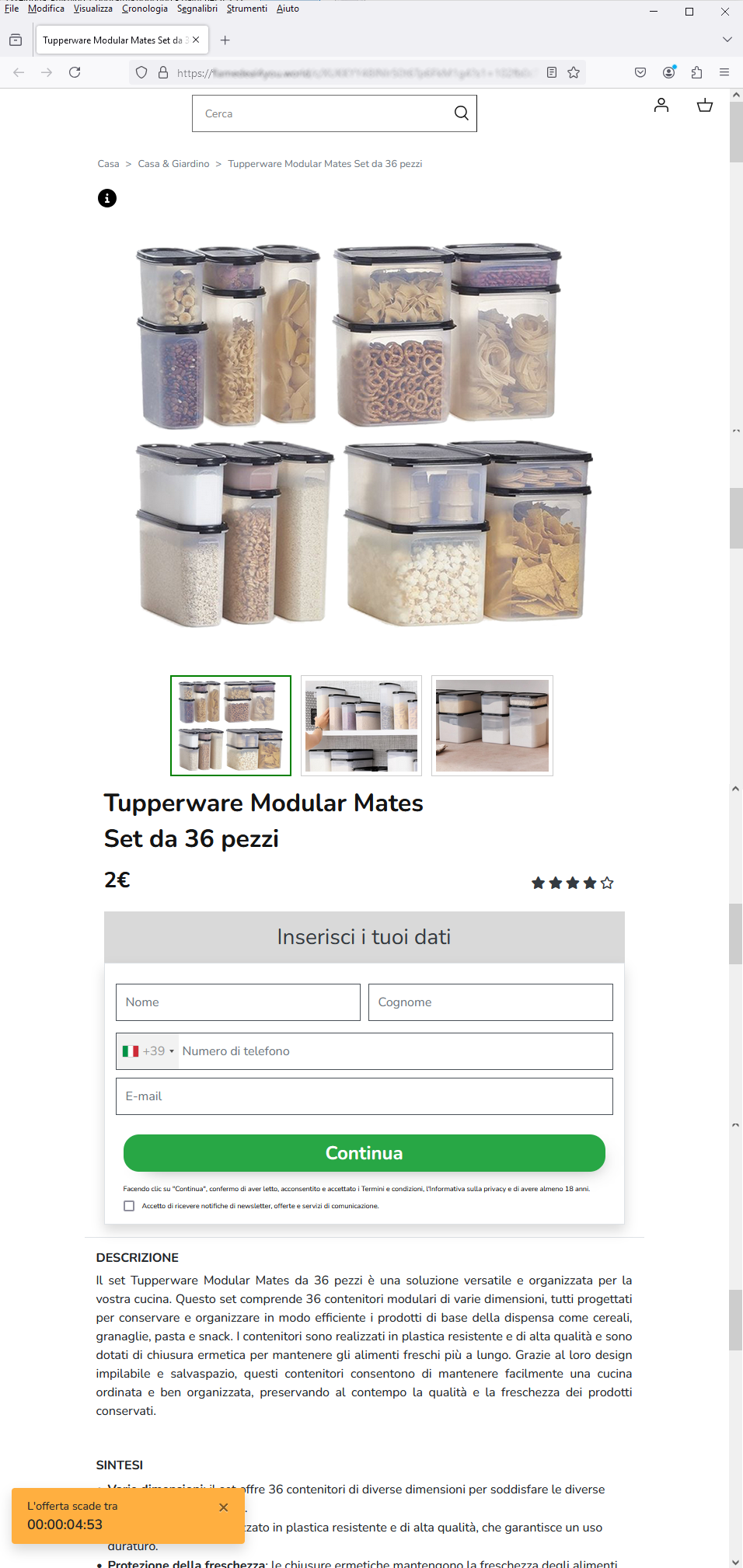
SUBJECT: <Hai vinto un 36 Piece Tupperware Modular Set #!oFJYQkj> (You won a 36 Piece Tupperware Modular Set #!oFJYQkj)
Below we analyze the following scam attempt that is spread through a false communication by the well-known large retail company Esselunga.
It is a promotional message that seems to propose an unmissable opportunity. The lucky user has been selected to participate in the ongoing monthly promotion through a survey that will allow him or her to win a prize: a 36 Piece Tupperware Modular Set ...or so it seems.
Certainly behind this phishing there is a real decoy for many inexperienced users.
Clearly Esselunga is uninvolved in the mass mailing of these malicious campaigns, which are real scams whose goal remains, as always, to steal sensitive data of the unsuspecting recipient
So keep an eye out. All it takes to avoid unpleasant incidents, is a little attention and a quick glance.
As we analyze the email, we see that the message comes from an email address <inkos85d0sd(at)hakunamatata[dot]info> not traceable to Esselunga's official domain. This is definitely anomalous and should, at the very least, make us suspicious. However, if we go ahead and click on the provided link here is what happens:
we are redirected to a landing page that, although graphically well done (with misleading images and the authentic logo of Esselunga) does not seem trustworthy at all.
In fact, the survey to obtain the prize is hosted on an anomalous address/domain:
[NomeDominioFake*].site
*FakeDomainName is a domain that simulates a known brand domain or is a randomly named domain.
which has no connection with Esselunga.
Cyber criminals masterminding the scam, try to induce the user to quickly finish the survey by making him/her believe that only few people can win, and the gifts are about to run out. There is also a countdown timer at the bottom of the screen, which however, if stopped - as we simulated - will start over immediately. This is a rather strange thing.
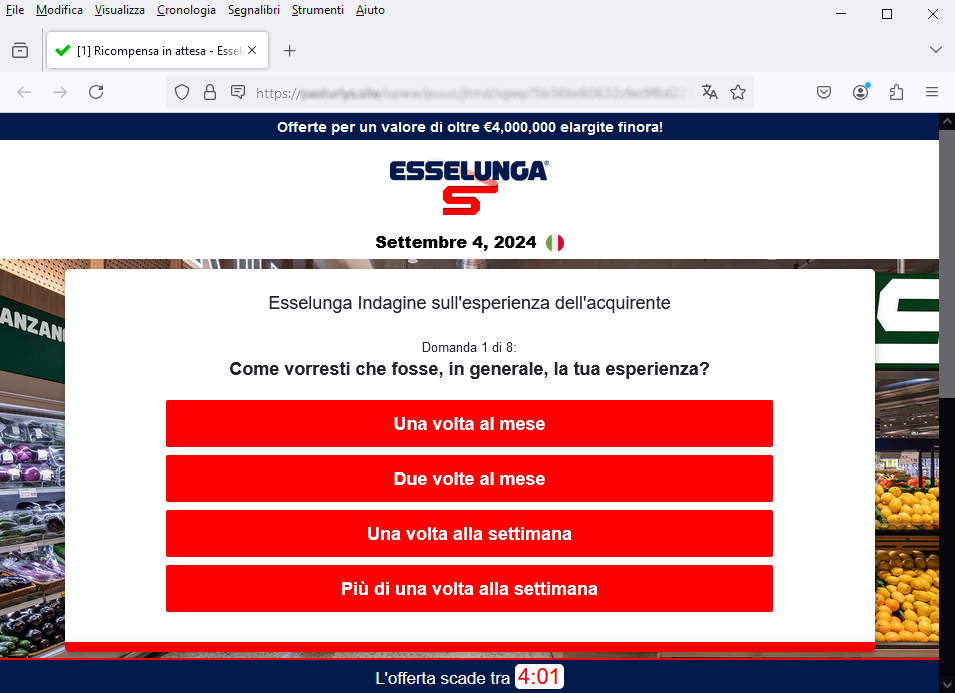
If we click on LO VOGLIO (I WANT IT), we are taken to the next screens, where we are asked to answer 8 questions.
Here specifically is question 1/8. These are, in fact, all very general questions focusing on the degree of satisfaction with the services offered by Esselunga and the daily habits of consumers. We see that the countdown timer is also present here to prompt the user to quickly finish the process for the award.
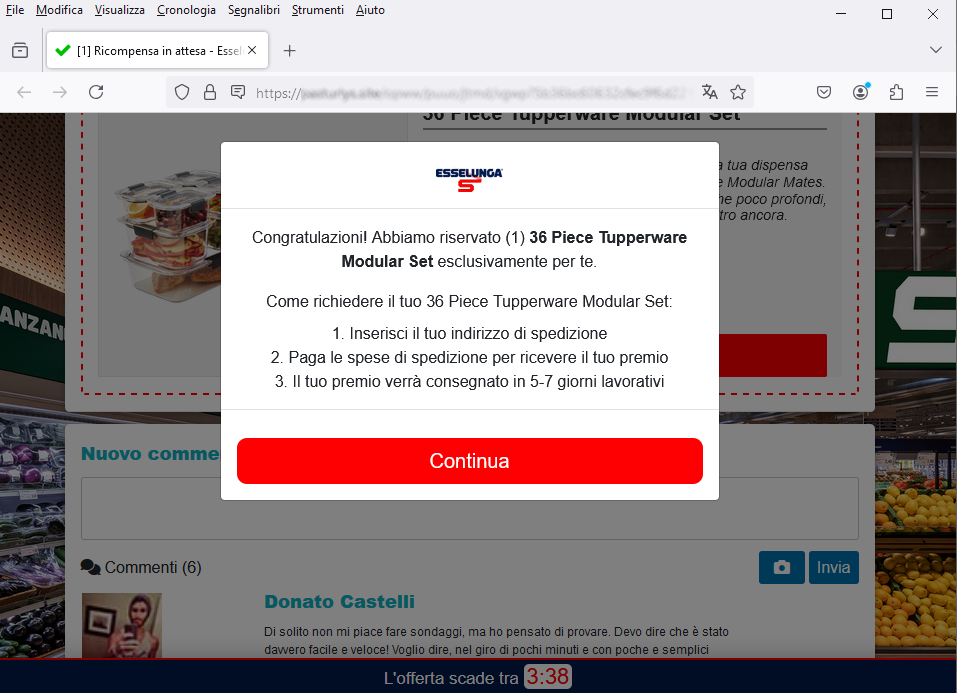
''Congratulazioni! Abbiamo riservato (1) 36 Piece Tupperware Modular Set esclusivamente per te.''
(Congratulations! We have reserved (1) 36 Piece Tupperware Modular Set exclusively for you.)
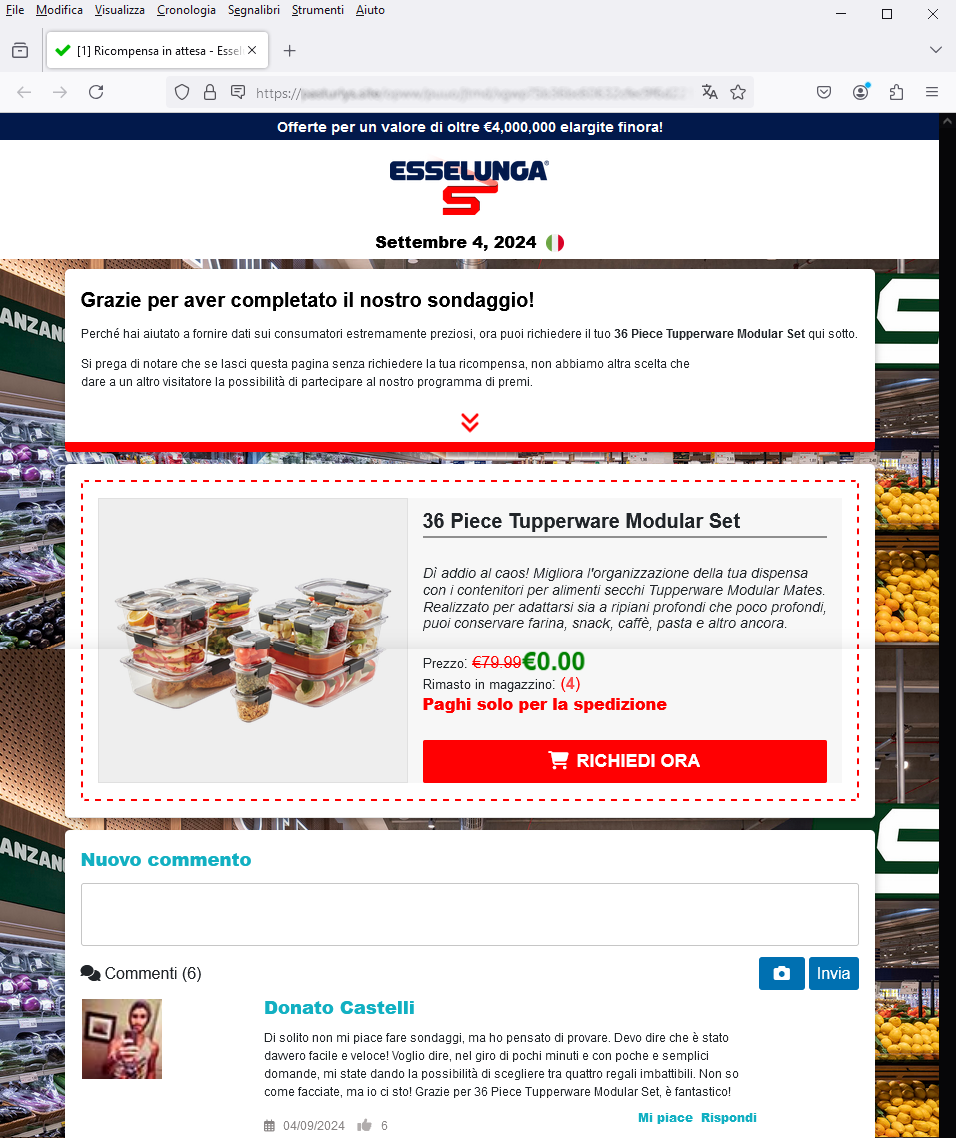
Here we go: in fact, all we need to do is enter our shipping address and pay the shipping cost, and in 5-7 business days the prize will be delivered.
To make the scam more trustworthy, several comments have been reported from customers who seem to have already participated in the survey. These are all reassuring testimonials/feedback about the actual delivery of the winnings and thus on the reliability of the message.
Surely if so many users were lucky why not try your luck?!
Then, if we click on Continua (Continue) we will be directed to another page to enter our shipping address and pay shipping costs.
As we can see from the side image, the purpose of the cyber criminals is to induce the victim to enter his/her sensitive data needed to ship the prize. Next credit card information will very probably be requested to pay shipping costs.
The page you are redirected to, in order to enter your personal information, is hosted on a new abnormal address/domain:
[NomeDominioFake*]
To conclude, we always urge you to be wary of advertising/promotional messages that boast of "giving away" valuables, and avoid clicking on suspicious links whose links may lead to a counterfeit site. In fact, if you trust these messages, your most valuable data will be delivered to cyber crooks who can use it at will.
Vir.IT eXplorer Lite VirIT Mobile Security Italian Anti-Malware software that protects Android™ smartphones and tablets, from Malware intrusions and other unwanted threats, and empowers the user to safeguard their privacy with an advanced heuristic approach (Permission Analyzer). TG Soft makes VirIT Mobile Security available for free by accessing the Google Play Store market (https://play.google.com/store/apps/details?id=it.tgsoft.virit) from which you can download the Lite version, which can be freely used in both private and corporate settings. You can upgrade to the PRO version by purchasing it directly from our website=> click here to order
A little bit of attention and glance can save a lot of hassles and headaches...
We urge you NOT to be fooled by these types of e-mails, which, even though they use familiar and not particularly sophisticated approach techniques, if there is a resurgence, with reasonable likelihood more than a few unfortunates will be fooled.
We invite you to check the following information on phishing techniques for more details:06/08/2024 14:50 - Phishing: most popular credential and/or data theft attempts in August 2024...
04/07/2024 17:22 - Phishing: the most common credential and/or data theft attempts in July 2024.
03/06/2024 17:22 - Phishing: the most common credential and/or data theft attempts in June 2024..
03/05/2024 11:56 - Phishing: the most common credential and/or data theft attempts in May 2024..
03/04/2024 10:23 - Phishing: the most common credential and/or data theft attempts in April 2024...
04/03/2024 10:42 - Phishing: the most common credential and/or data theft attempts in March 2024..
06/02/2024 08:55 - Phishing: the most common credential and/or data theft attempts in February 2024...
02/01/2024 16:04 - Phishing: the most common credential and/or data theft attempts in January 2024....
11/12/2023 09:39 - Phishing: the most common credential and/or data theft attempts in December 2023...
03/11/2023 08:58 - Phishing: the most common credential and/or data theft attempts in November 2023....
03/10/2023 16:35 - Phishing: the most common credential and/or data theft attempts in October 2023....
05/09/2023 10:35 - Phishing: the most common credential and/or data theft attempts in September 2023....
01/08/2023 17:33 - Phishing: the most common credential and/or data theft attempts in August 2023..
03/07/2023 10:23 - Phishing: the most common credential and/or data theft attempts in July 2023..

If you are not yet using Vir.IT eXplorer PRO, it is advisable to install Vir.IT eXplorer Lite -FREE Edition- to supplement the antivirus in use to increase the security of your computers, PCs and SERVERS.
Try Vir.IT eXplorer Lite
VirIT Mobile Security AntiMalware ITALIAN for ALL AndroidTM Devices
Acknowledgements
TG Soft's Anti-Malware Research Center would like to thank all users, customers, reseller technicians, and all people who have transmitted/reported material attributable to Phishing activities to our Research Center, that allowed us to make this information as complete as possible.How to submit suspicious emails for analysis as possible phishing but also virus/malware or Crypto-Malware
You can submit materials to TG Soft's Anti-Malware Research Center safely and free of charge in two ways:
 For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
For more details on how to safely forward suspicious e-mails, we invite you to consult the following public page: How to send suspicious emails for analysis
We provide all this information to help you prevent credential theft, viruses/malware or, even worse, next-generation Ransomware / Crypto-Malware.
TG Soft's C.R.A.M. (Anti-Malware Research Center)
Any information published on our site may be used and published on other websites, blogs, forums, facebook and/or in any other form both in paper and electronic form as long as the source is always and in any case cited explicitly “Source: CRAM by TG Soft www.tgsoft.it” with a clickable link to the original information and / or web page from which textual content, ideas and / or images have been extrapolated.
It will be appreciated in case of use of the information of C.R.A.M. by TG Soft www.tgsoft.it in the report of summary articles the following acknowledgment/thanks “Thanks to Anti-Malware Research Center C.R.A.M. by TG Soft of which we point out the direct link to the original information: [direct clickable link]”
如有侵权请联系:admin#unsafe.sh