1)背景
最近听同事说在WindowsXP下通过PsSetCreateProcessNotifyRoutine注册了一个进程创建回调,然后尝试通过PEB来获取被创建进程的命令行参数,发现PEB结构中的命令行等相关数据还没有被填充进去。
通过查看GetCommandLineA函数的反汇编,得知进程的命令行保存在一个固定的地址0x7C8855F4
MOVE EAX, DWORD PTR [0x7C8855F4] RETN
在进程创建回调中,附加到目标进程,再查看这个地址的数据,如下所示。 因为时机还不对,这个地址还没被申请呢!!
kd> db 0x7C8855F4 7c8855f4 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? 7c885604 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? 7c885614 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? 7c885624 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? 7c885634 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? 7c885644 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? 7c885654 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ???????????????? 7c885664 ?? ?? ?? ?? ?? ?? ?? ??-?? ?? ?? ?? ?? ?? ?? ?? ????????????????
通过windbg,检查PEB结构中的ProcessParameters字段,该字段指向一个_RTL_USER_PROCESS_PARAMETERS结构,并且该字段固定地址为0x20000
kd> dt _PEB 7ffd5000 ntdll!_PEB +0x000 InheritedAddressSpace : 0 '' +0x001 ReadImageFileExecOptions : 0 '' +0x002 BeingDebugged : 0 '' +0x003 SpareBool : 0 '' +0x004 Mutant : 0xffffffff Void +0x008 ImageBaseAddress : 0x01000000 Void +0x00c Ldr : (null) +0x010 ProcessParameters : 0x00020000 _RTL_USER_PROCESS_PARAMETERS +0x014 SubSystemData : (null) +0x018 ProcessHeap : (null)
查看ProcessParameters中的数据,发现Commdline字段中保存的是一个无效地址0x000008ec
kd> dt _RTL_USER_PROCESS_PARAMETERS 0x00020000 ntdll!_RTL_USER_PROCESS_PARAMETERS +0x000 MaximumLength : 0x1000 +0x004 Length : 0x970 +0x008 Flags : 0x2000 +0x00c DebugFlags : 0 +0x010 ConsoleHandle : 0x00310002 Void +0x014 ConsoleFlags : 0 +0x018 StandardInput : 0x00000003 Void +0x01c StandardOutput : 0x00000007 Void +0x020 StandardError : 0x0000000b Void +0x024 CurrentDirectory : _CURDIR +0x030 DllPath : _UNICODE_STRING "--- memory read error at address 0x00000498 ---" +0x038 ImagePathName : _UNICODE_STRING "--- memory read error at address 0x000008ac ---" +0x040 CommandLine : _UNICODE_STRING "--- memory read error at address 0x000008ec ---" +0x048 Environment : 0x00010000 Void +0x04c StartingX : 0 +0x050 StartingY : 1 +0x054 CountX : 0x64 +0x058 CountY : 0x64 +0x05c CountCharsX : 0 +0x060 CountCharsY : 0 +0x064 FillAttribute : 0 +0x068 WindowFlags : 0 +0x06c ShowWindowFlags : 1 +0x070 WindowTitle : _UNICODE_STRING "--- memory read error at address 0x0000091c ---" +0x078 DesktopInfo : _UNICODE_STRING "--- memory read error at address 0x0000094c ---" +0x080 ShellInfo : _UNICODE_STRING "--- memory read error at address 0x0000096c ---" +0x088 RuntimeData : _UNICODE_STRING "" +0x090 CurrentDirectores : [32] _RTL_DRIVE_LETTER_CURDIR
但是通过windbg的扩展命令!peb却能正常查看PEB结构中的命令行数据,怎么直接通过dt _PEB address 就不行了?
kd> !peb
PEB at 7ffd5000
InheritedAddressSpace: No
ReadImageFileExecOptions: No
BeingDebugged: No
ImageBaseAddress: 01000000
NtGlobalFlag: 0
NtGlobalFlag2: 0
Ldr 00000000
*** unable to read Ldr table at 00000000
SubSystemData: 00000000
ProcessHeap: 00000000
ProcessParameters: 00020000
CurrentDirectory: '< Name not readable >'
WindowTitle: 'notepad 11111111111.txt'
ImageFile: 'C:\WINDOWS\system32\notepad.exe'
CommandLine: 'notepad 11111111111.txt'
尝试在进程空间内暴力搜索命令行参数,得到以下两个结果:
kd> s -u 0x0 0x7ffffff "notepad 11111111111" 000208ec 006e 006f 0074 0065 0070 0061 0064 0020 n.o.t.e.p.a.d. . 0002091c 006e 006f 0074 0065 0070 0061 0064 0020 n.o.t.e.p.a.d. .
000208ec 这个地址看起来很眼熟,原来是(PEB.ProcessParameters + PEB.ProcessParameters.CommandLine),因为PEB结构中的_RTL_USER_PROCESS_PARAMETERS结构还没被完全填充好,在创建进程的通知回调被触发时,这个结构中的CommandLine只是一个相对偏移。
(000208ec = 0x00020000 + 0x000008ec )
2)分析
00020000 00 10 00 00 64 09 00 00-00 20 00 00 00 00 00 00 ....d.... ...... 00020010 01 00 30 00 00 00 00 00-03 00 00 00 07 00 00 00 ..0............. 00020020 0b 00 00 00 4e 00 08 02-90 02 00 00 0e 00 00 00 ....N........... 00020030 12 04 14 04 98 04 00 00-38 00 3a 00 ac 08 00 00 ........8.:..... 00020040 28 00 2a 00 e8 08 00 00-00 00 01 00 00 00 00 00 (.*............. <---- WORD PTR [0x00020044] = offset; 0x20000+offset = commandline; 00020050 01 00 00 00 64 00 00 00-64 00 00 00 00 00 00 00 ....d...d....... 00020060 00 00 00 00 00 00 00 00-00 00 00 00 01 00 00 00 ................ 00020070 28 00 2a 00 14 09 00 00-1e 00 20 00 40 09 00 00 (.*....... .@... 00020080 00 00 02 00 60 09 00 00-00 00 00 00 00 00 00 00 ....`........... 00020090 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000200a0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000200b0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000200c0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000200d0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000200e0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000200f0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020100 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020110 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020120 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020130 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020140 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020150 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020160 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020170 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020180 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020190 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000201a0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000201b0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000201c0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000201d0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000201e0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000201f0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020200 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020210 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020220 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020230 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020240 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020250 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020260 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020270 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020280 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020290 43 00 3a 00 5c 00 44 00-6f 00 63 00 75 00 6d 00 C.:.\.D.o.c.u.m. 000202a0 65 00 6e 00 74 00 73 00-20 00 61 00 6e 00 64 00 e.n.t.s. .a.n.d. 000202b0 20 00 53 00 65 00 74 00-74 00 69 00 6e 00 67 00 .S.e.t.t.i.n.g. 000202c0 73 00 5c 00 41 00 64 00-6d 00 69 00 6e 00 69 00 s.\.A.d.m.i.n.i. 000202d0 73 00 74 00 72 00 61 00-74 00 6f 00 72 00 00 00 s.t.r.a.t.o.r... 000202e0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000202f0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020300 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020310 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020320 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020330 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020340 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020350 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020360 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020370 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020380 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020390 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000203a0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000203b0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000203c0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000203d0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000203e0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 000203f0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020400 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020410 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020420 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020430 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020440 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020450 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020460 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020470 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020480 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................ 00020490 00 00 00 00 00 00 00 00-43 00 3a 00 5c 00 57 00 ........C.:.\.W. 000204a0 49 00 4e 00 44 00 4f 00-57 00 53 00 5c 00 73 00 I.N.D.O.W.S.\.s. 000204b0 79 00 73 00 74 00 65 00-6d 00 33 00 32 00 3b 00 y.s.t.e.m.3.2.;. 000204c0 43 00 3a 00 5c 00 57 00-49 00 4e 00 44 00 4f 00 C.:.\.W.I.N.D.O. 000204d0 57 00 53 00 5c 00 73 00-79 00 73 00 74 00 65 00 W.S.\.s.y.s.t.e. 000204e0 6d 00 33 00 32 00 3b 00-43 00 3a 00 5c 00 57 00 m.3.2.;.C.:.\.W. 000204f0 49 00 4e 00 44 00 4f 00-57 00 53 00 5c 00 73 00 I.N.D.O.W.S.\.s. 00020500 79 00 73 00 74 00 65 00-6d 00 3b 00 43 00 3a 00 y.s.t.e.m.;.C.:. 00020510 5c 00 57 00 49 00 4e 00-44 00 4f 00 57 00 53 00 \.W.I.N.D.O.W.S. 00020520 3b 00 2e 00 3b 00 43 00-3a 00 5c 00 50 00 79 00 ;...;.C.:.\.P.y. 00020530 74 00 68 00 6f 00 6e 00-32 00 37 00 3b 00 43 00 t.h.o.n.2.7.;.C. 00020540 3a 00 5c 00 50 00 72 00-6f 00 67 00 72 00 61 00 :.\.P.r.o.g.r.a. 00020550 6d 00 20 00 46 00 69 00-6c 00 65 00 73 00 5c 00 m. .F.i.l.e.s.\. 00020560 42 00 6f 00 72 00 6c 00-61 00 6e 00 64 00 5c 00 B.o.r.l.a.n.d.\. 00020570 44 00 65 00 6c 00 70 00-68 00 69 00 37 00 5c 00 D.e.l.p.h.i.7.\. 00020580 42 00 69 00 6e 00 3b 00-43 00 3a 00 5c 00 50 00 B.i.n.;.C.:.\.P. 00020590 72 00 6f 00 67 00 72 00-61 00 6d 00 20 00 46 00 r.o.g.r.a.m. .F. 000205a0 69 00 6c 00 65 00 73 00-5c 00 42 00 6f 00 72 00 i.l.e.s.\.B.o.r. 000205b0 6c 00 61 00 6e 00 64 00-5c 00 44 00 65 00 6c 00 l.a.n.d.\.D.e.l. 000205c0 70 00 68 00 69 00 37 00-5c 00 50 00 72 00 6f 00 p.h.i.7.\.P.r.o. 000205d0 6a 00 65 00 63 00 74 00-73 00 5c 00 42 00 70 00 j.e.c.t.s.\.B.p. 000205e0 6c 00 5c 00 3b 00 43 00-3a 00 5c 00 50 00 52 00 l.\.;.C.:.\.P.R. 000205f0 4f 00 47 00 52 00 41 00-7e 00 31 00 5c 00 42 00 O.G.R.A.~.1.\.B. 00020600 6f 00 72 00 6c 00 61 00-6e 00 64 00 5c 00 43 00 o.r.l.a.n.d.\.C. 00020610 42 00 55 00 49 00 4c 00-44 00 7e 00 31 00 5c 00 B.U.I.L.D.~.1.\. 00020620 42 00 69 00 6e 00 3b 00-43 00 3a 00 5c 00 50 00 B.i.n.;.C.:.\.P. 00020630 52 00 4f 00 47 00 52 00-41 00 7e 00 31 00 5c 00 R.O.G.R.A.~.1.\. 00020640 42 00 6f 00 72 00 6c 00-61 00 6e 00 64 00 5c 00 B.o.r.l.a.n.d.\. 00020650 43 00 42 00 55 00 49 00-4c 00 44 00 7e 00 31 00 C.B.U.I.L.D.~.1. 00020660 5c 00 50 00 72 00 6f 00-6a 00 65 00 63 00 74 00 \.P.r.o.j.e.c.t. 00020670 73 00 5c 00 42 00 70 00-6c 00 3b 00 43 00 3a 00 s.\.B.p.l.;.C.:. 00020680 5c 00 57 00 49 00 4e 00-44 00 4f 00 57 00 53 00 \.W.I.N.D.O.W.S. 00020690 5c 00 73 00 79 00 73 00-74 00 65 00 6d 00 33 00 \.s.y.s.t.e.m.3. 000206a0 32 00 3b 00 43 00 3a 00-5c 00 57 00 49 00 4e 00 2.;.C.:.\.W.I.N. 000206b0 44 00 4f 00 57 00 53 00-3b 00 43 00 3a 00 5c 00 D.O.W.S.;.C.:.\. 000206c0 57 00 49 00 4e 00 44 00-4f 00 57 00 53 00 5c 00 W.I.N.D.O.W.S.\. 000206d0 53 00 79 00 73 00 74 00-65 00 6d 00 33 00 32 00 S.y.s.t.e.m.3.2. 000206e0 5c 00 57 00 62 00 65 00-6d 00 3b 00 43 00 3a 00 \.W.b.e.m.;.C.:. 000206f0 5c 00 50 00 72 00 6f 00-67 00 72 00 61 00 6d 00 \.P.r.o.g.r.a.m. 00020700 20 00 46 00 69 00 6c 00-65 00 73 00 5c 00 4d 00 .F.i.l.e.s.\.M. 00020710 69 00 63 00 72 00 6f 00-73 00 6f 00 66 00 74 00 i.c.r.o.s.o.f.t. 00020720 20 00 56 00 69 00 73 00-75 00 61 00 6c 00 20 00 .V.i.s.u.a.l. . 00020730 53 00 74 00 75 00 64 00-69 00 6f 00 5c 00 43 00 S.t.u.d.i.o.\.C. 00020740 6f 00 6d 00 6d 00 6f 00-6e 00 5c 00 54 00 6f 00 o.m.m.o.n.\.T.o. 00020750 6f 00 6c 00 73 00 5c 00-57 00 69 00 6e 00 4e 00 o.l.s.\.W.i.n.N. 00020760 54 00 3b 00 43 00 3a 00-5c 00 50 00 72 00 6f 00 T.;.C.:.\.P.r.o. 00020770 67 00 72 00 61 00 6d 00-20 00 46 00 69 00 6c 00 g.r.a.m. .F.i.l. 00020780 65 00 73 00 5c 00 4d 00-69 00 63 00 72 00 6f 00 e.s.\.M.i.c.r.o. 00020790 73 00 6f 00 66 00 74 00-20 00 56 00 69 00 73 00 s.o.f.t. .V.i.s. 000207a0 75 00 61 00 6c 00 20 00-53 00 74 00 75 00 64 00 u.a.l. .S.t.u.d. 000207b0 69 00 6f 00 5c 00 43 00-6f 00 6d 00 6d 00 6f 00 i.o.\.C.o.m.m.o. 000207c0 6e 00 5c 00 4d 00 53 00-44 00 65 00 76 00 39 00 n.\.M.S.D.e.v.9. 000207d0 38 00 5c 00 42 00 69 00-6e 00 3b 00 43 00 3a 00 8.\.B.i.n.;.C.:. 000207e0 5c 00 50 00 72 00 6f 00-67 00 72 00 61 00 6d 00 \.P.r.o.g.r.a.m. 000207f0 20 00 46 00 69 00 6c 00-65 00 73 00 5c 00 4d 00 .F.i.l.e.s.\.M. 00020800 69 00 63 00 72 00 6f 00-73 00 6f 00 66 00 74 00 i.c.r.o.s.o.f.t. 00020810 20 00 56 00 69 00 73 00-75 00 61 00 6c 00 20 00 .V.i.s.u.a.l. . 00020820 53 00 74 00 75 00 64 00-69 00 6f 00 5c 00 43 00 S.t.u.d.i.o.\.C. 00020830 6f 00 6d 00 6d 00 6f 00-6e 00 5c 00 54 00 6f 00 o.m.m.o.n.\.T.o. 00020840 6f 00 6c 00 73 00 3b 00-43 00 3a 00 5c 00 50 00 o.l.s.;.C.:.\.P. 00020850 72 00 6f 00 67 00 72 00-61 00 6d 00 20 00 46 00 r.o.g.r.a.m. .F. 00020860 69 00 6c 00 65 00 73 00-5c 00 4d 00 69 00 63 00 i.l.e.s.\.M.i.c. 00020870 72 00 6f 00 73 00 6f 00-66 00 74 00 20 00 56 00 r.o.s.o.f.t. .V. 00020880 69 00 73 00 75 00 61 00-6c 00 20 00 53 00 74 00 i.s.u.a.l. .S.t. 00020890 75 00 64 00 69 00 6f 00-5c 00 56 00 43 00 39 00 u.d.i.o.\.V.C.9. 000208a0 38 00 5c 00 62 00 69 00-6e 00 00 00 43 00 3a 00 8.\.b.i.n...C.:. 000208b0 5c 00 57 00 49 00 4e 00-44 00 4f 00 57 00 53 00 \.W.I.N.D.O.W.S. 000208c0 5c 00 73 00 79 00 73 00-74 00 65 00 6d 00 33 00 \.s.y.s.t.e.m.3. 000208d0 32 00 5c 00 63 00 61 00-6c 00 63 00 2e 00 65 00 2.\.c.a.l.c...e. 000208e0 78 00 65 00 00 00 00 00-63 00 61 00 6c 00 63 00 x.e.....c.a.l.c. <---- 0x000208E0 = calc -test 123456789 000208f0 20 00 2d 00 74 00 65 00-73 00 74 00 20 00 31 00 .-.t.e.s.t. .1. 00020900 32 00 33 00 34 00 35 00-36 00 37 00 38 00 39 00 2.3.4.5.6.7.8.9. 00020910 00 00 00 00 63 00 61 00-6c 00 63 00 20 00 2d 00 ....c.a.l.c. .-. 00020920 74 00 65 00 73 00 74 00-20 00 31 00 32 00 33 00 t.e.s.t. .1.2.3. 00020930 34 00 35 00 36 00 37 00-38 00 39 00 00 00 00 00 4.5.6.7.8.9..... 00020940 57 00 69 00 6e 00 53 00-74 00 61 00 30 00 5c 00 W.i.n.S.t.a.0.\. 00020950 44 00 65 00 66 00 61 00-75 00 6c 00 74 00 00 00 D.e.f.a.u.l.t...
3)代码
#include <ntifs.h>
VOID Attach(PEPROCESS Process)
{
ULONG offset;
PWCHAR commandline;
KAPC_STATE ks;
KeStackAttachProcess(Process, &ks);
offset = (ULONG)*((PCSHORT)0x20044);
commandline = (PWCHAR)(0x20000 + offset);
DbgPrint("[KeStackAttachProcess]: commandline from 0x%08x: %S\n", (ULONG_PTR)commandline,commandline);
KeUnstackDetachProcess(&ks);
}
void PcreateProcessNotifyRoutine(HANDLE ParentId,HANDLE ProcessId,BOOLEAN Create)
{
PEPROCESS SubEProcess;
if (Create)
{
DbgPrint("[Create Process]: ParentId:%d ProcessId:%d \n", (ULONG)ParentId, (ULONG)ProcessId);
SubEProcess = NULL;
if (NT_SUCCESS(PsLookupProcessByProcessId(ProcessId, &SubEProcess)))
{
Attach(SubEProcess);
ObDereferenceObject(SubEProcess);
}
}
}
VOID DriverUnload(PDRIVER_OBJECT DriverObject)
{
UNREFERENCED_PARAMETER(DriverObject);
DbgPrint("DriverUnload Enter \n");
PsSetCreateProcessNotifyRoutine(PcreateProcessNotifyRoutine, TRUE);
}
NTSTATUS DriverEntry(PDRIVER_OBJECT DriverObject, PUNICODE_STRING RegistryPath)
{
UNREFERENCED_PARAMETER(RegistryPath);
DbgPrint("DriverEntry Enter \n");
do
{
PsSetCreateProcessNotifyRoutine(PcreateProcessNotifyRoutine,FALSE);
DriverObject->DriverUnload = DriverUnload;
} while (0);
return STATUS_SUCCESS;
}
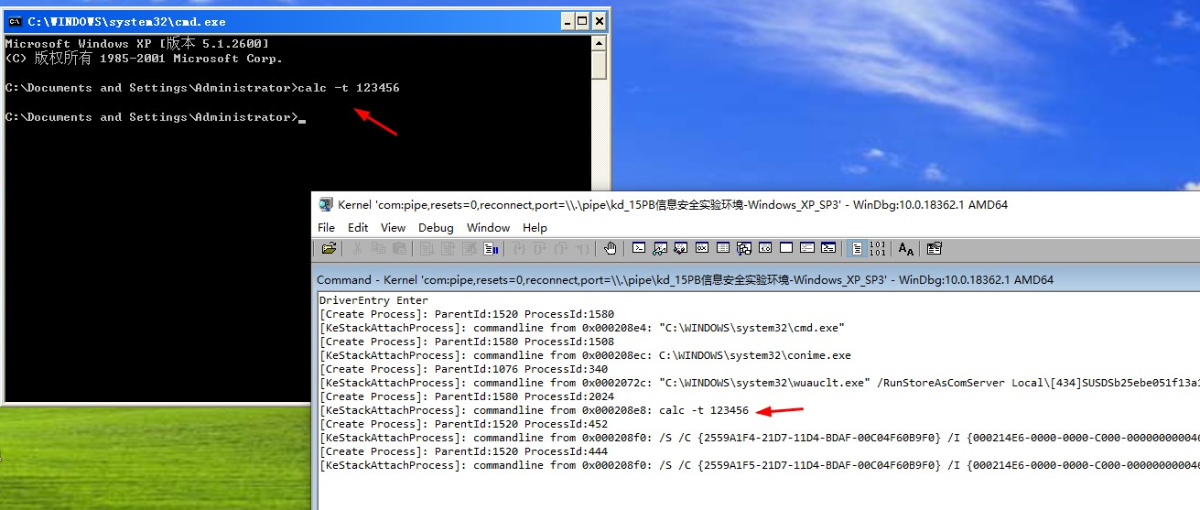
4)效果

文章来源: https://bbs.pediy.com/thread-259657.htm
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh