2024-4-18 02:1:31 Author: securityaffairs.com(查看原文) 阅读量:19 收藏
Linux variant of Cerber ransomware targets Atlassian servers

Threat actors are exploiting the CVE-2023-22518 flaw in Atlassian servers to deploy a Linux variant of Cerber (aka C3RB3R) ransomware.
At the end of October 2023, Atlassian warned of a critical security flaw, tracked as CVE-2023-22518 (CVSS score 9.1), that affects all versions of Confluence Data Center and Server.
The vulnerability is an improper authorization issue that can lead to significant data loss if exploited by an unauthenticated attacker.
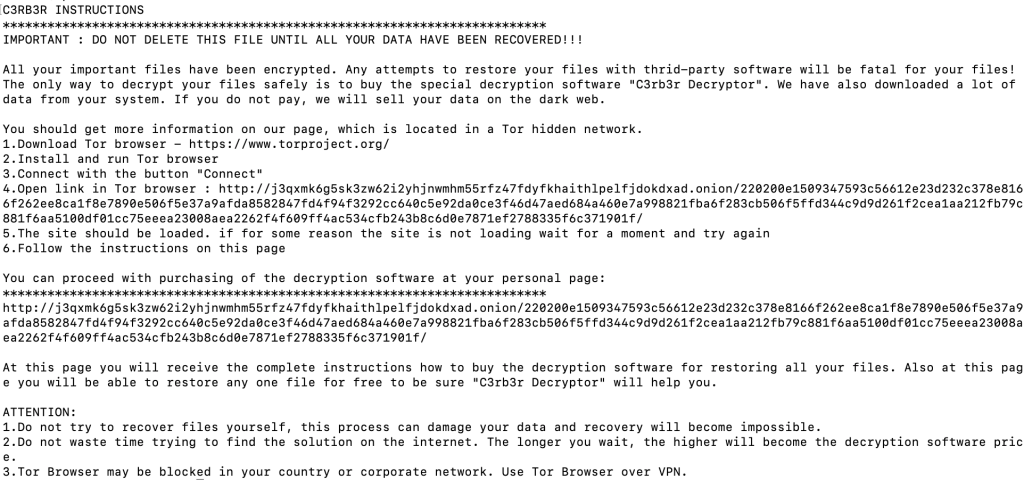
Cado Security Labs recently became aware that Cerber ransomware is being deployed into Confluence servers via the CVE-2023-22518 exploit. The experts pointed out that there is very little knowledge about the Linux variant of the ransomware family.
Cerber has been active since at least 2016, most recently it was involved in attacks against Confluence servers.
The malware includes three heavily obfuscated C++ payloads compiled as 64-bit Executable and Linkable Format (ELF) files and packed with UPX. UPX is a widely-used packer among threat actors, enabling the storage of encoded program code within the binary. At runtime, the code is extracted in memory and executed, a process known as “unpacking,” to evade detection by security software.
Attackers exploited this vulnerability to gain initial access to vulnerable Atlassian instances.
“We have observed instances of the Cerber ransomware being deployed after an attacker leveraged CVE-2023-22518 in order to gain access to vulnerable instances of Confluence. It is a fairly recent improper authorization vulnerability that allows an attacker to reset the Confluence application and create a new administrator account using an unprotected configuration restore endpoint used by the setup wizard.” states Cado Security.
Financially motivated threat actors created an admin account to deploy the Effluence web shell plugin and execute arbitrary commands on the vulnerable server.
The attackers use the web shell to download and run the primary Cerber payload.
“In a default install, the Confluence application is executed as the “confluence” user, a low privilege user. As such, the data the ransomware is able to encrypt is limited to files owned by the confluence user. It will of course succeed in encrypting the datastore for the Confluence application, which can store important information.” continues the report. “If it was running as a higher privilege user, it would be able to encrypt more files, as it will attempt to encrypt all files on the system.”
The payload is written in C++ and is highly obfuscated, and packed with UPX. The researchers pointed out that it serves as a stager for further payloads, the malware uses a C2 server at 45[.]145[.]6[.]112 to download and unpack further payloads. Upon execution, the malicious code can delete itself from the disk.
Upon execution, the malware unpacks itself, and tries to create a file at /var/lock/0init-ld.lo.
It then connects to the (now defunct) C2 server at 45[.]145[.]6[.]112 and fetches a log checker known internally as agttydck.
Upon executing the “agttydck.bat” the encryptor payload “agttydcb.bat” is downloaded and executed by the primary payload.
The agttydck malware, written in C++ and packed with UPX, performs several malicious actions: it logs activity in “/tmp/log.0” at startup and “/tmp/log.1” at completion, searches the root directory for encryptable directories, drops a ransom note in each directory, and encrypts all files, appending a “.L0CK3D” extension.

“Cerber is a relatively sophisticated, albeit aging, ransomware payload. While the use of the Confluence vulnerability allows it to compromise a large amount of likely high value systems, often the data it is able to encrypt will be limited to just the confluence data and in well configured systems this will be backed up. This greatly limits the efficacy of the ransomware in extracting money from victims, as there is much less incentive to pay up.” concludes the report that also includes Indicators of compromise (IoCs).
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, Cerber ransomware)
如有侵权请联系:admin#unsafe.sh