2024-4-3 15:16:11 Author: cyble.com(查看原文) 阅读量:3 收藏
Key Takeaways
- Once again, a fake e-shop campaign has been detected, this time targeting 18 Malaysian banks with upgraded malicious applications.
- The campaign has progressed from its initial focus on Malaysian banks to a broader scope that now encompasses banks in Vietnam and Myanmar.
- The latest version of the malware introduces advanced features such as screen-sharing functionality, the utilization of accessibility services, and intricate communication with command and control servers, signifying an elevated level of sophistication and perseverance.
- The upgraded variant was observed employing the open-source string obfuscator “Paranoid” and incorporating the Janus WebRTC module for screen sharing.
Overview
In September 2022, Cyble Research and Intelligence Lab (CRIL) noted a substantial uptick in the prevalence of the fake e-shop campaign, which had been actively targeting Malaysia, Vietnam, and Myanmar. Initially identified in 2021, the campaign primarily focused on numerous banks within Malaysia before extending its reach to include entities in Vietnam and Myanmar.
CRIL recently detected increased phishing websites associated with the fake e-shop campaign, identifying more than 10 sites actively distributing an enhanced version of the malicious APK. Initially, the campaign distributed APK files primarily utilizing phishing techniques coupled with an SMS stealer to pilfer user credentials. However, the latest iteration of the malware has been upgraded to include screen-sharing functionality and the exploitation of the Accessibility service.
Before we explore the characteristics of the new variant, let’s look into the previously identified variations within the campaign.
Fake e-shop campaign targeting Malaysia
Since 2021, the fake e-shop campaign has consistently targeted Malaysian banks. Using fake cleaning service pages/accounts across multiple social media platforms, victims are prompted to contact the TAs phone number via WhatsApp.
Subsequently, they are redirected to phishing sites and urged to download the malicious APK file.

Figure 1 – TA’s sending phishing site to the victim
Over time, the threat actor (TA) has expanded its focus to include more banks in Malaysia. In previous variants of the malware, it was observed targeting 10 Malaysian banks:
- Hong Leong Bank
- CIMB Bank
- Maybank
- AmBank
- Public Bank
- RHB Bank
- OCBC Bank
- Bank Rakhyat
- Bank Islam
- Bank Simpanan Nasional (BSN)
- Agrobank
Fake e-shop campaign Targeting Vietnam
In September 2022, the campaign expanded its operations to Vietnam. The TA established a phishing site named “hxxps://bestpay-vn[.]store,” posing as an authentic payment application website. This site was responsible for disseminating Android malware designed to target Vietnam’s HD Bank customers.

Figure 2 – Phishing site involved in fake e-shop campaign to target Vietnam
The malware has been observed to load a counterfeit website (hxxps://ebanking[.]hdbank.vn), prompting users to input their net banking credentials for HD Bank. Additionally, it utilizes the Command and Control (C&C) server “hxxps://sgbx[.]online,” which has been identified in other malicious applications associated with the fake e-shop campaign.
Fake e-shop campaign targeting Myanmar
In November 2022, we discovered a malicious APK with the hash value 1133bba91d548021a89e8d74173fae9dba254c3da60659c1d17d9021ba9d452e, which was associated with the same campaign but appeared to be targeting Myanmar. This particular sample maintained the theme of a cleaning service observed in the campaign aimed at Malaysia.

Figure 3 – Phishing website used in sample targeting Myanmar
The APK was designed to load a phishing site within a WebView crafted in the Burmese language. It displayed a fake payment page tailored to mimic the services of four banks operating in Myanmar and steal net banking credentials.
- Kanbawza Bank
- Yoma Bank
- Ayeyarwady Bank
- CB Bank
Updates to the fake e-shop campaign:
We’ve recently identified over 10 phishing sites pretending to be online shopping platforms. Below is a list of these fraudulent sites:
- hxxps://shopcenter-global[.]com
- hxxps://worldshopping-global[.]com
- hxxps://onlineshop-global[.]com
- hxxps://www[.]weshop-global[.]com
- hxxps://shopcenter-global[.]com
- hxxps://shopbox-global[.]com
- hxxps://myshopping-global[.]com
- hxxps://www[.]mystore-global[.]com
- hxxps://ecart-global[.]com
- hxxps://goshop-global[.]com
- hxxps://everydaystore-global[.]com
- hxxps://easyshop-global[.]com/
These phishing sites deviate from the themes observed last year and lack the same level of sophistication. They include only a few features of e-commerce websites and offer download buttons for Android and iOS applications, as depicted in the image below.

Figure 4 – Latest phishing site in fake e-shop campaign
Despite the phishing site displaying download buttons for Android and iOS, only the APK file is downloadable. The iOS application download button does not initiate any app download or redirect to the app store.
We’ve noticed several updates in the latest malicious application, including incorporating a screen-sharing feature using the Janus WebRTC plugin, exploitation of the accessibility service, implementation of C&C communication for data exfiltration and screen sharing, and an expanded list of targets.
The enhanced version of the malware now focuses on 18 Malaysian banks. Below is the comprehensive list:
- AFFIN BANK
- Agro Bank
- Alliance Bank
- May Bank
- AmBank
- Bank Simpanan Nasional
- CIMB
- Hong Leong Bank
- HSBC Bank
- Bank Islam
- KFH Malaysia
- Bank Muamalat
- OCBC Bank
- Public Bank
- Bank Rakyat
- RHB Bank
- Standard Chartered Bank
- UOB Malaysia
The malware employs two URLs: one for phishing and C&C activities and another for screen sharing. The figure below illustrates the campaign’s entire infection chain and the malicious application’s behavior.

Figure 5 – Fake e-shop campaign attack flow
Technical Details
APK Metadata Information
- App Name: eCart
- Package Name: org.ecrt.cr
- SHA256 Hash: 776f98f55e19b5b3f79124415796511703c96633505d6a1cae4614e9a1a70163

Figure 6 – Application metadata information
Upon installation, the malware prompts the victim to grant Accessibility service which later malware abuses this service to perform auto clicks on the infected device.

Figure 7 – Malware prompts for the Accessibility service
The malware initiates communication with the C&C server located at hxxps://superbunapp[.]com, transmitting logs related to the application’s permission status and the connectivity status of the remote server jimmyserv[.]online, utilized for screen-sharing.

Figure 8 – Malware sending log related to the Accessibility permission status
Upon analyzing the Accessibility service class “GestureDispatchService,” we discovered its utilization by the malware. The malware abuses this service to initiate and stop the screen-sharing service and perform various automated gestures such as moving cursors, entering text, and toggling buttons. These gestures are received from the implemented Janus plugin.

Figure 9 – Malware abusing accessibility service for screen sharing feature
The malware has been observed employing the open-source string obfuscator “Paranoid” to obfuscate strings, making the code difficult to analyze.

Figure 10 – Malware using Paranoid string obfuscator
After granting Accessibility permissions, victims are prompted to configure notifications, but instead, they are directed to change their default SMS app to the malicious application. This is followed by a dialogue box requesting screen capturing permissions.

Figure 11 – Malware initiating screen capture feature
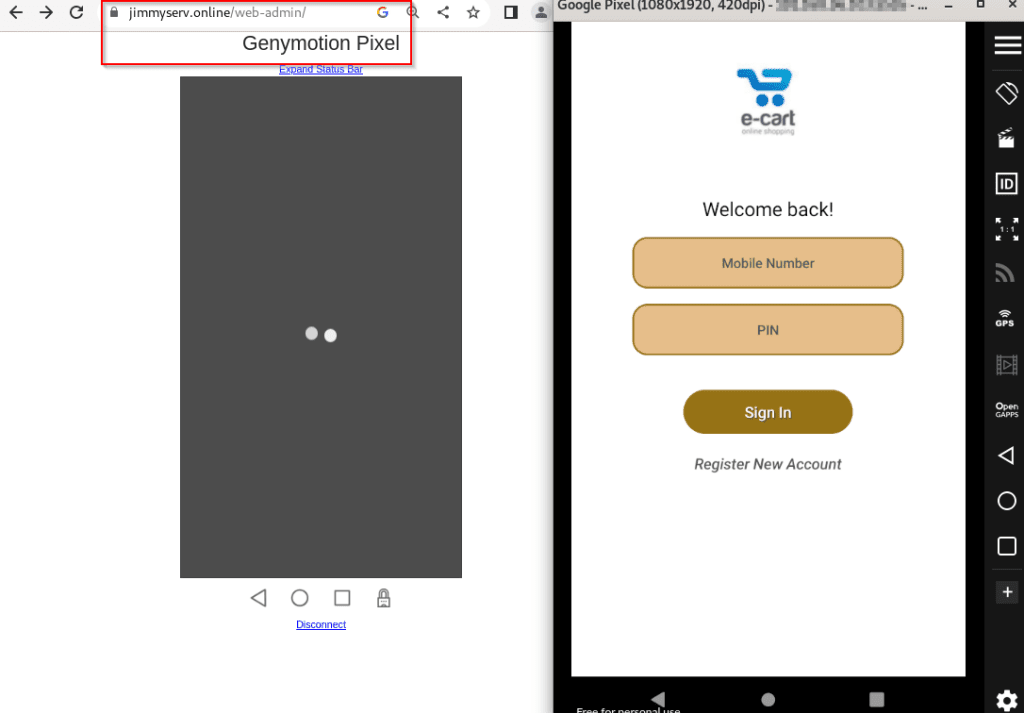
Upon commencement of screen capture permission, the malware establishes communication with the remote server “hxxps://jimmyserv[.]online” to configure the Janus WebRTC server and send screen content. Additionally, the remote server hosts the web admin panel accessible at the URL “hxxps://jimmyserv[.]online/web-admin/”, as depicted in Figure 13.

Figure 12 – Malware connects to the remote server to establish screen-sharing

Figure 13 – Admin panel of Remote server
The malware generates an 8-digit random session ID and a 4-digit random password, subsequently used to establish a remote server connection. In addition to the session ID and password, the malware also sends the device name, which can be viewed on the remote server, as illustrated in Figure 15.

Figure 14 – Generating random session ID and password

Figure 15 – Remote server connection with an infected device using the Janus plugin
During the application’s operation, we observed that the screen-sharing feature was not functioning due to misconfiguration in the Janus plugin. Nonetheless, the inclusion of this feature signifies an advancement in the fake e-shop campaign.
Phishing Activity
The malware has expanded its tactics to include phishing, aiming to extract credentials from the targeted application. It connects to the URL hxxps://superbunapp[.]com and loads a login and registration page.

Figure 16 – Fake login and registration pages
After the victim successfully logs in or registers into the malicious application, the malware retrieves product details from the C&C server for the fake online shop and presents them to the victim.

Figure 17 – Malware displays fake products
Once the victim proceeds to purchase the fake products, they encounter three payment options: credit card, debit card, and FPX payment, as depicted in the figure below.

Figure 18 – Payment methods provided by fake e-shop
As the image above shows, the malware targets 18 Malaysian banks through a fake FPX payment method. FPX (Financial Process Exchange) is an online payment system based in Malaysia that enables customers to make hassle-free payments. TA has crafted distinct FPX pages for each targeted bank to steal credentials. The following figure displays some of the fake FPX pages:

Figure 19 – Fake FPX pages
The below figure shows the network communication stealing credentials of May Bank:

Figure 20 – Malware sending FPX credentials to the C&C server
Conclusion
The fake e-shop campaign, first detected in 2021, has evolved significantly, extending its reach to various countries such as Malaysia, Vietnam, and Myanmar. Recent advancements point to an upsurge in phishing endeavors and the enhancement of the malware’s functionalities, notably incorporating screen-sharing capabilities and exploiting accessibility services, highlighting the dynamic landscape of cyber threats.
The expanded features exemplify the relentless endeavors of threat actors to enhance their tactics for targeting a broader array of victims, foreshadowing potential future upgrades. It underscores the imperative for users to maintain vigilance against phishing attempts and exercise caution when downloading applications or engaging with unfamiliar websites.
Our Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Only install software from official app stores such as the Play Store or the iOS App Store.
- Using a reputed antivirus and internet security software package is recommended on connected devices, including PCs, laptops, and mobile.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Be careful while opening links received via SMS or emails sent to your mobile device.
- Google Play Protect should always be enabled on Android devices.
- Be wary of any permissions that you give an application.
- Keep devices, operating systems, and applications up to date.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Procedure |
| Initial Access (TA0027) | Phishing (T1660) | Malware distribution via phishing site |
| Persistence (TA0028) | Event Triggered Execution: Broadcast Receivers (T1624.001) | The malware registered broadcast receivers to steal incoming SMS |
| Defense Evasion (TA0030) | Input Injection (T1516) | Malware can mimic user interaction, perform clicks and various gestures, and input data |
| Collection (TA0035) | Screen Capture (T1513) | Malware can capture screen content using the Janus WebRTC plugin |
| Collection (TA0035) | Protected User Data: SMS Messages (T1636.004) | Steals SMSs from the infected device |
| Exfiltration (TA0036) | Exfiltration Over C2 Channel (T1646) | Sending exfiltrated data over C&C server |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| cc3ca9738777afa55bbf0aa340cb41a6f547c50e9a19b6ff0ab498243033104d b83cb9b308d0423599d7bd815efb73a5992f419b 4d147c9e5fdb943d31f5458e2b9bc3fe | SHA256 SHA1 MD5 | Fake e-shop malicious apk file |
| hxxps://www[.]worldshopping-global[.]com/ | URL | Phishing website |
| hxxps://jimmyserv[.]online | URL | WebRTC remote server |
| hxxps://superbunapp[.]com | URL | C&C server |
| 776f98f55e19b5b3f79124415796511703c96633505d6a1cae4614e9a1a70163 51c9f273670a0a454119e1bb772986b230fa0133 620e450b2ee36010939106e7a036d442 | SHA256 SHA1 MD5 | Fake Trading application |
| hxxps://ecart-global[.]com | URL | Phishing website |
| hxxps://shopcenter-global[.]com hxxps://worldshopping-global[.]com hxxps://onlineshop-global[.]com hxxps://www[.]weshop-global[.]com hxxps://shopcenter-global[.]com hxxps://shopbox-global[.]com hxxps://myshopping-global[.]com hxxps://www[.]mystore-global[.]com hxxps://ecart-global[.]com hxxps://goshop-global[.]com hxxps://everydaystore-global[.]com hxxps://easyshop-global[.]com/ | URL | Phishing websites |
Related
如有侵权请联系:admin#unsafe.sh