2024-4-3 02:59:56 Author: securityaffairs.com(查看原文) 阅读量:16 收藏
XSS flaw in WordPress WP-Members Plugin can lead to script injection

A cross-site scripting vulnerability (XXS) in the WordPress WP-Members Membership plugin can lead to malicious script injection.
Researchers from Defiant’s Wordfence research team disclosed a cross-site scripting vulnerability (XXS) in the WordPress WP-Members Membership plugin that can lead to malicious script injection.
The Unauthenticated Stored Cross-Site Scripting vulnerability was reported to Wordfence by the WordPress developer Webbernaut as part of the company Bug Bounty Extravaganza.
Webbernaut received a $500 bounty.
The WP-Members Membership Plugin is currently installed on over 60,000 WordPress websites.
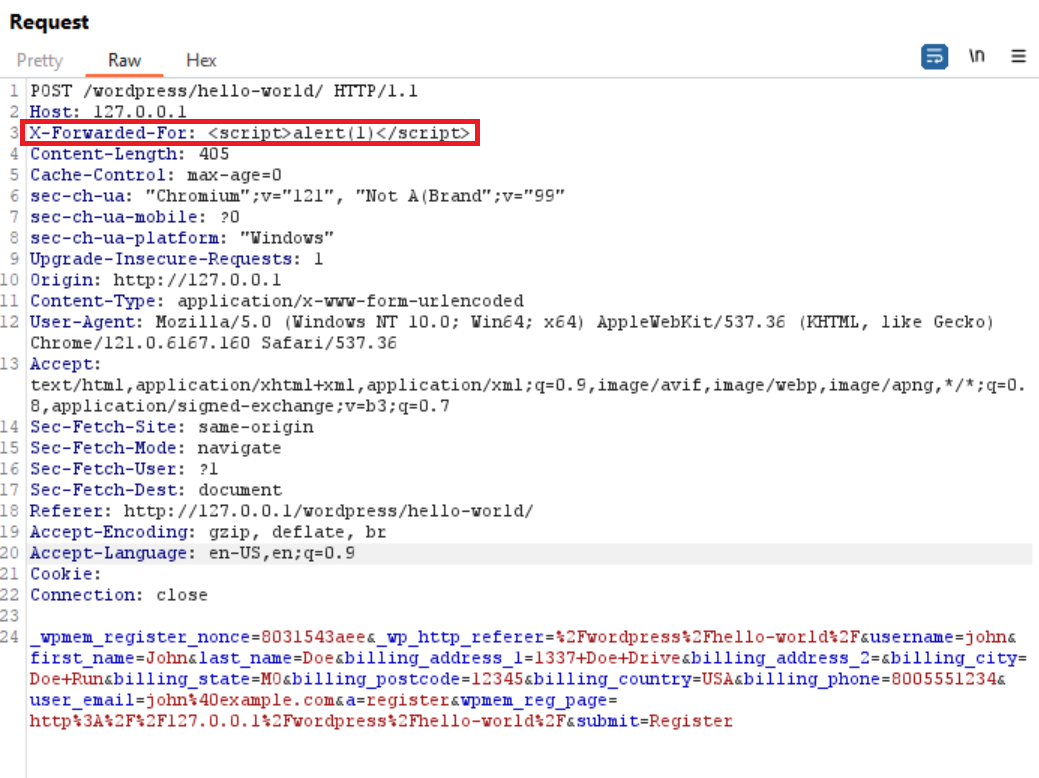
“The vulnerability allows threat actors to inject arbitrary JavaScript via the X-Forwarded-For header, used by the plugin for logging purposes.” reads the advisory published by Wordfence. “When viewed by an administrator, the malicious code is executed in the context of the administrator’s browser session and allows for the creation of malicious administrator users as well as changes to an affected site’s settings which could lead to a complete site takeover.”
The flaw impacts all versions up to, and including, 3.4.9.2, the issue is due to insufficient input sanitization and output escaping. An unauthenticated attacker can trigger the flaw to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page which is the edit users page.
Wordfence states that the flaw was only partially patched in version 3.4.9.2 and fully patched in version 3.4.9.3.
In order to exploit this XSS, an attacker could intercept a registration request after filling out and submitting the registration form using a proxy. Then the attacker can modify the raw request to contain an X-Forwarded-For header set to a malicious payload enclosed in script tags.

The request allows the creation of a user account with the details provided by the attacker.
The plugin stores the IP address of users who filed the registration form in their profile through the vulnerable rktgk_get_user_ip function.
The rktgk_get_user_ip function checks whether the request contains an HTTP_CLIENT_IP or HTTP_X_FORWARDED_FOR header. If either header is present, the function uses that value as the user’s IP instead of the REMOTE_ADDR variable, and then returns the provided value as the IP address. Since the input was not sanitized, an attacker can manipulate the HTTP headers supplying a malicious web script, which would then be stored as the user’s IP.
If an administrator edits or views this user account, the injected JavaScript will be present in the generated source code when the page loads.
“It is important to understand that this malicious code will be executed in the context of an administrator’s browser session and can be used to create malicious user accounts, redirect site visitors to other malicious sites and perform other malicious actions.” continues the advisory.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, WordPress)
如有侵权请联系:admin#unsafe.sh