
2024-3-29 21:0:13 Author: www.sentinelone.com(查看原文) 阅读量:4 收藏
The Good | U.S. Treasury Cracks Down on Russian & Chinese State-Backed Threats
In back-to-back announcements this week, the U.S. Department of the Treasury has sanctioned cryptocurrency exchanges leveraged by Russian dark markets and a Chinese-based company linked to APT31 threat actors (aka Zirconium and Violet Typhoon).
Thirteen entities and two individuals now face sanctions by the Treasury’s Department’s Office of Foreign Assets Control (OFAC) for their role in developing and servicing OFAC-designated Russian dark web markets and banks. Bitpapa IC FZC LLC and Obshchestvo S Ogranichennoy Otvetstvennostyu Tsentr Obrabotki Elektronnykh Platezhey (TOEP) both facilitated substantial transactions with entities like Hydra Market and Garantex, while Crypto Explorer DMCC (AWEX) operated as a crypto exchange, facilitating conversions involving OFAC-designated Russian banks.
Before its seizure in April 2022, Hydra Market was one the world’s largest and longest-operating darknet markets, attributed with over 80% of all darknet-related crypto transactions at the time.
The Treasury, in collaboration with other international agencies, has also placed sanctions on a Wuhan-based company and two Chinese nationals associated with targeting U.S. politicians to support China’s espionage objectives. Both individuals are allegedly linked to APT31, a PRC state-backed hacking group focused on stealing information from government officials, journalists, and academics.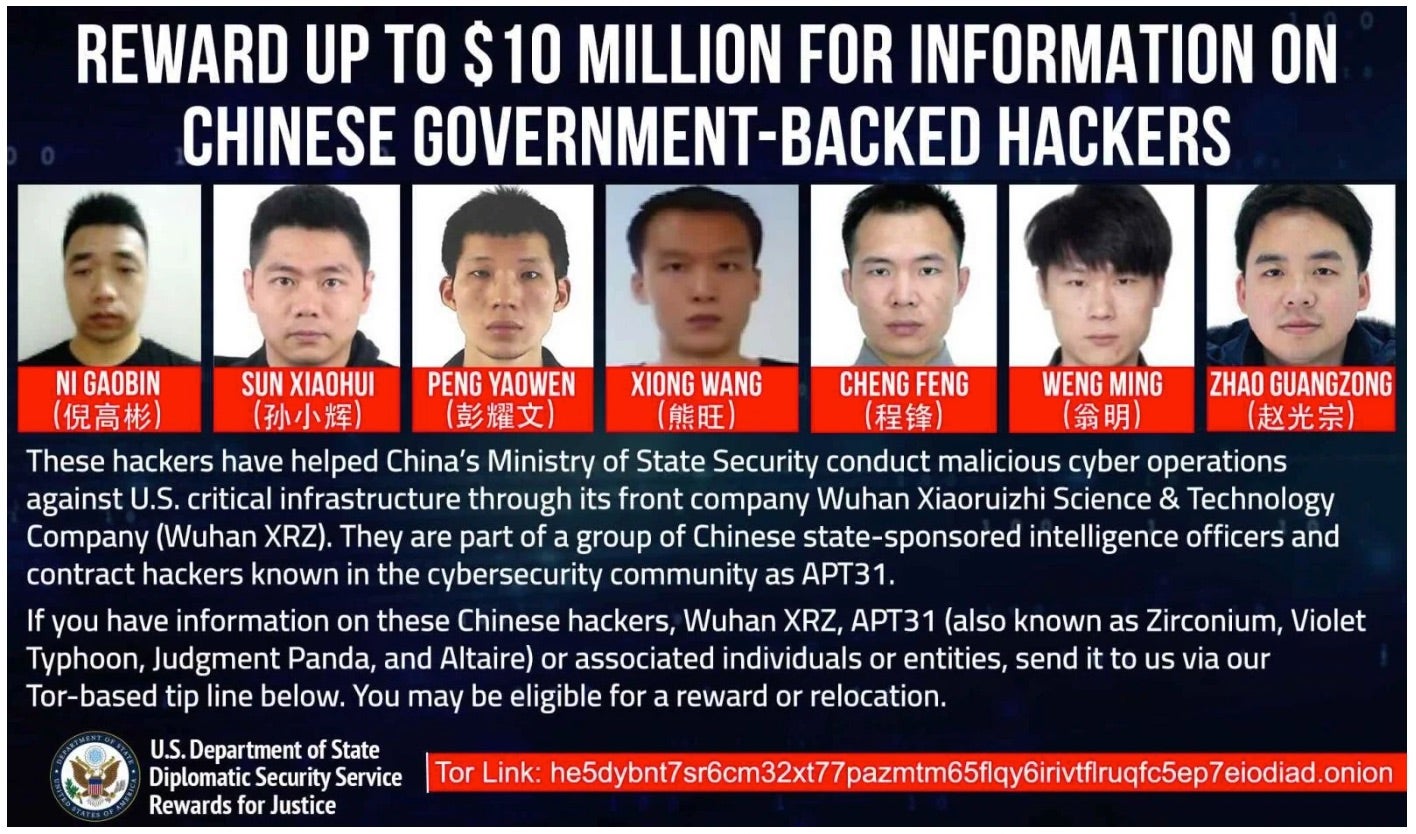
The coordinated effort with the DoJ, FBI, Department of State, and the UK Foreign, Commonwealth & Development Office (FCDO) led to unsealed indictments and sanctions, freezing all assets and interests in the United States connected to the designated individuals and entities. These sanctions are part of an ongoing commitment by the U.S. government to protect national security interests amidst evolving geopolitical tensions.
The Bad | Upgraded PhaaS Phishing Kit Threatens Microsoft & Google MFA Measures
The emergence of a new phishing-as-a-service (PhaaS) platform dubbed “Tycoon 2FA” is targeting Microsoft 365 and Gmail accounts with the aim of circumventing two-factor authentication (2FA) safeguards.
Initially detected by cybersecurity analysts in October 2023 during routine threat monitoring, Tycoon 2FA had been operational since at least August 2023 and initially distributed through private Telegram channels by a group called Saad Tycoon. Similarities between Tycoon 2FA and other adversary-in-the-middle (AitM) platforms indicate potential code reuse or collaborative efforts between developers.
Tycoon 2FA’s modus operandi involves a multi-step process where users are tricked into interacting with phishing pages. Background scripts then extract the user’s email in order to customize the attack while the user is redirected to a fake Microsoft login page to steal credentials. The threat actors then employ a reverse proxy server hosting phishing web pages to intercept session cookies. Once a user completes the MFA challenge and successfully authenticates their access, the actors can then replay the sessions and bypass multi-factor authentication (MFA) mechanisms.

Most currently, the analysts have reported Tycoon 2FA’s latest version upgrade, which enhances its capabilities, by expanding traffic filtering and refining stealth tactics to evade analysis. The modifications are indicative of ongoing efforts to refine the kit’s effectiveness in avoiding detection by identifying and bypassing typical traffic patterns.
Recent estimates show that Tycoon 2FA is associated with thousands of phishing pages found in the wild since August 2023. Given this broad user base of cybercriminals using the service for their phishing operations, it is essential for organizations to double down on educating their users on how to recognize the signs of phishing attacks, even if they have MFA enabled.
The Ugly | Chinese APTs Target ASEAN Members in Cyber Espionage Campaign
A new report shed light this week on a three-month long espionage campaign conducted by two Chinese-based advanced persistent threat (APT) groups. Most notably, both APTs have focused their efforts on entities and member nations of the Association of Southeast Asian Nations (ASEAN).
The first of the two APT groups is known by names such as Stately Taurus, Camaro Dragon, or Earth Preta, active since 2012. As observed, Stately Taurus targeted organizations in Japan, Singapore, Myanmar, and the Philippines via phishing scams delivering two custom-created malware packages. Coincidentally, the state-sponsored APT group took advantage of a recent ASEAN-Australia Special Summit event to launch this campaign – a tactic used by threat actors to exploit the increased online activity, communications, and digital traffic characteristic of major events.
One of the malware packages is designed to masquerade as a ZIP file, containing an executable named “Talking_Points_for_China.exe” to initiate the deployment of a known Stately Taurus malware called “PUBLOAD” upon execution. This executable, a renamed copy of the legitimate software KeyScrambler.exe, executes malicious code discreetly through DLL side-loading. The second package comprises a screensaver executable titled “Note PSO.scr”, which serves as a conduit for retrieving additional malicious payloads from a remote IP address. These payloads include a benign program disguised as “WindowsUpdate.exe” alongside a rogue DLL.
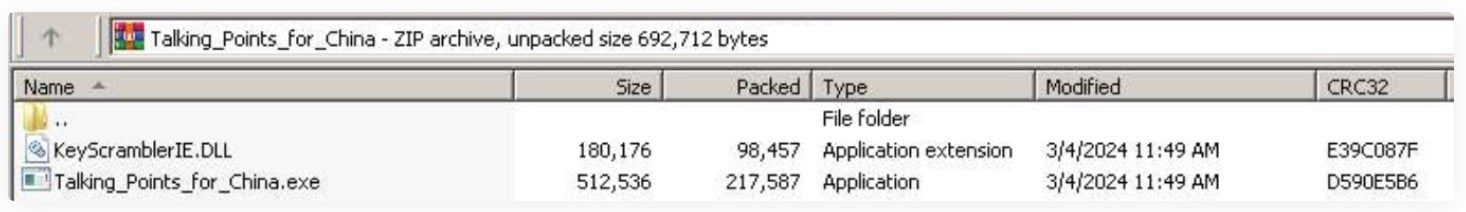
The second, unidentified APT group has been observed compromising government entities in Singapore, Cambodia, and Laos. Given their role in managing sensitive diplomatic and economic information, attacks on ASEAN member countries are consistent. These kinds of cyber espionage campaigns will continue to be a key challenge for government entities, where nation state-backed threat groups aim to collect geopolitical leverage within their regions in order to get ahead in the international arena.
如有侵权请联系:admin#unsafe.sh